Home » Best Practices for Robust Identity and Access Governance » IT Administrator’s Handbook: Practical Privileged Access Management Best Practices
IT Administrator’s Handbook: Practical Privileged Access Management Best Practices
Learn about securing your organization's critical vulnerabilities and privileged access with a PAM solution, including best practices and recommendations for implementation without specific tools.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
As you modernize your organization’s infrastructure, add more critical systems, and expose your infrastructure due to multiple work locations, your attack surface expands, exposing more critical vulnerabilities in your environment. One area of concern is that attackers commonly take advantage of unsecured user accounts, which tend to have privileged access to most (if not all) systems. They can then perform lateral attacks, which compromise your organization and can lead to significant losses of both data and money.
You need a way to ensure that any privileged access is closely monitored and audited, and one way to achieve that is by using a privileged access management (PAM) solution. These products significantly improve security and reduce risk from outside attacks when paired with appropriate standards in your environment.
This article explores privileged access management, including best practices and recommendations for what to do for your organization. You can expect to learn how PAM strengthens security posture and enables secure, efficient operations in modern IT environments. Please note that this article doesn’t cover implementing any PAM solutions or related security software, so you can follow it without any specific tools.
Summary of privileged access management best practices
Here is a summary of the best practices that will be discussed in the article.
|
Best practice |
Description |
|---|---|
|
Enforce least privilege access |
Limit user permissions to the minimum necessary for their job roles. |
|
Use just-in-time (JIT) access |
Provide temporary privileged access only when needed, reducing persistent risk. |
|
Implement session recording and auditing |
Monitor and log all privileged sessions for accountability and compliance. |
|
Secure privileged credentials |
Store passwords and secrets in a secure, encrypted vault with access controls. |
|
Regularly review and rotate access rights |
Periodically audit and update access rights and credentials. |
Before we proceed, let’s review what identity-based access is. Identity-based access serves as a foundational layer for secure access management and complements privileged access management by establishing trusted identities before privileged access is granted or monitored. This method ensures that you have the capacity to evaluate each and every access request made by means of authentication.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Enforce least privilege access
Keep access permissions to resources at the minimum necessary by employing the principle of least privilege (PoLP). By limiting access to exactly what is required, organizations can reduce the potential for damaging misuse of sensitive systems and data. This idea is applied as much as possible across the whole IT ecosystem and is essential to lowering the risk of security breaches.
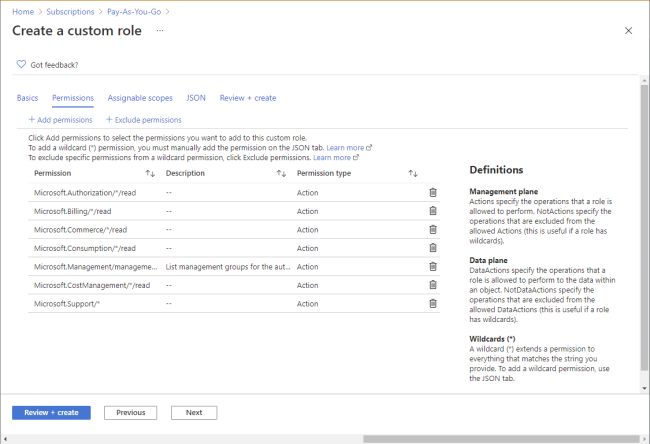
For example, an IT administrator-privileged account can access a small three-node cluster for maintenance. However, the account’s scope of access is only for that cluster, and its cluster role, let’s say, is only limited to database services. Usually, a common mistake for organizations is improper enforcement of least privilege, where a group of users has access to all servers with full administrator rights, which would pose a high risk when a threat actor compromises said account.
Usually, PAM solutions don’t integrate this principle out of the box, as administrators mainly plan and scope access manually and directly through Active Directory (AD). However, some solutions still have the ability to manage privileged access and least privilege delegation. For example, Microsoft Entra ID, Cyberark, and Cayosoft Administrator all tap into AD, which helps you manage privileged user accounts efficiently.
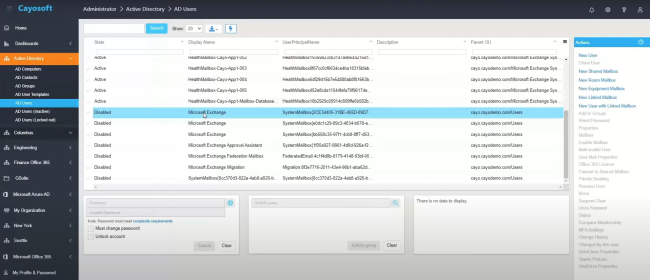
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Use just-in-time access
Just-in-time (JIT) access is a security practice where different identities like users, service accounts, and applications are granted elevated access for a specific time window. . This may seem similar to the previously discussed principle of least privilege where privileged accounts often retain continuous access, however, JIT reduces exposure by ensuring that elevated permissions are only temporary, purpose-driven, and time-limited.
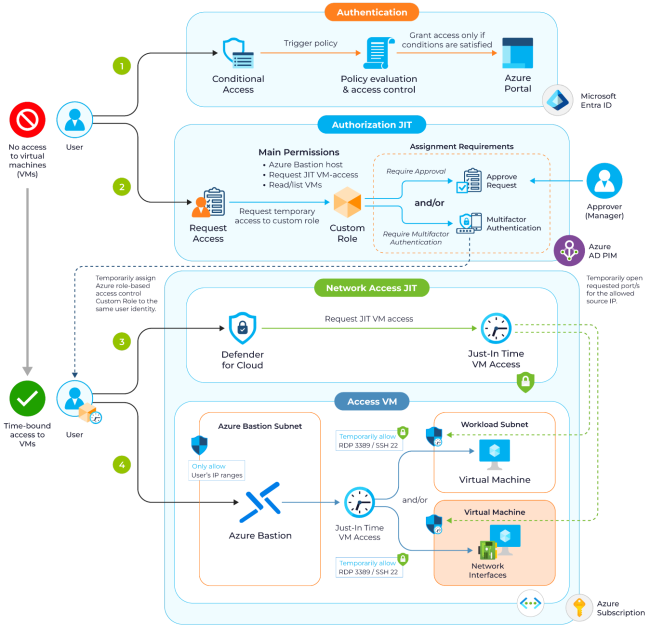
JIT access can also be revoked automatically after the time window expires or manually whenever an activity has concluded. For example, a database administrator may request access to a production system for a scheduled update. Through JIT, access is granted only for the duration of the maintenance window and automatically revoked afterward, leaving no lingering entry points for potential misuse.
Incorporating JIT access within a privileged access management (PAM) solution strengthens identity security by provisioning least privileged access only when it is required. Not all PAM solutions are equipped with JIT capabilities, but when available, it can prevent privilege sprawl and reduce the risk associated with dormant or excessive rights.
Implement session recording and auditing
If a breach or configuration error does occur, recorded sessions provide definitive evidence about what actions were taken, by whom, and when. This is one of the benefits of having a solution that implements session recording and auditing. Mainly for compliance purposes, the solution can record sessions, keystrokes, and usually, screen recording if needed. For example, if someone alters a critical database but considers it unapproved or unexpected, session logs can help identify the root cause rapidly.
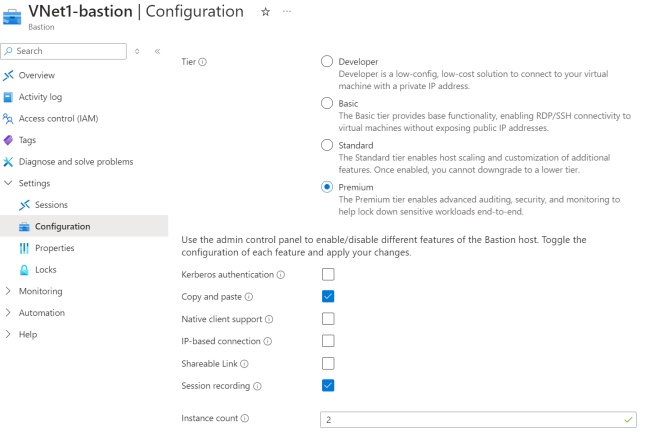
PAM solutions with built-in session recording make auditing even more effective as they link recorded sessions to user accounts, ensuring full traceability and accountability.
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Secure privileged credentials
As an administrator, you can improve the security of privileged users’ access credentials. There are many ways to secure privileged credentials, but usually, they cover the following:
- Password vaulting: Store privileged credentials in an encrypted secret vault with restricted, auditable access.
- Multi-factor authentication (MFA): Enforce verification of a user’s identity by means of another method like a personal device or an email.
- Policy enforcement: Apply policies like conditional access based on role, location, device posture, or risk level.
As mentioned, these are just a few of the security principles enforced to secure identity-based access. Like most organizations, administrators should not only resort to using one principle. The table below explores a few use cases where you can implement a multi-layer security framework for your privileged access accounts by combining multiple security controls.
| Use Case | Security Control Applied | Potential Outcome |
|---|---|---|
| Accessing a domain admin password | Password vaulting + MFA + approval secured from an autdorized administrator | Ensures tdat only autdorized users can retrieve secrets |
| Automated service account autdentication | Password vaulting + password rotation | Eliminates hardcoded credentials |
| Logging into a production cloud console | Password vaulting + MFA + just-in-time access | Restricts use to verified users witdin a set time window |
| tdird-party contractor access | Password vaulting + policy-based access + session recording | Limits access scope and ensures traceability |
Also, multiple solutions in the market provide an additional layer of security on top of your privileged access accounts’ security controls. One example of these solutions is Cayosoft, which offers a unified solution for securing and managing all your Microsoft Entra ID directories.
Regularly review and rotate access rights
Periodically auditing who has access to what systems, what level of privilege they possess, and whether those rights are still warranted are all part of intensive access reviews. Usually, these regular access reviews go through either a single or multiple levels of approvers before access is granted. This procedure helps businesses identify unused or excessive access permissions and guarantees compliance with the least privilege concept.
In parallel, rotating access reduces the risk of credential compromise. Access rotation generally refers to the periodic change of multiple access methods, such as keys, hashes, and passwords.
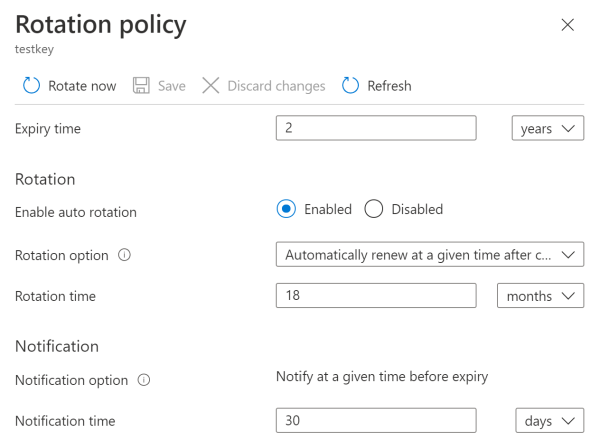
However, if incorporated with secure password vaults and automation, PAM solutions can schedule regular rotation of passwords or trigger changes immediately after access is revoked or an employee exits.
In addition, some solutions provide the ability to audit users who reuse passwords in all of the privileged accounts that they own. This provides you an opportunity to inform and make users aware at their own security risk.
When used together, access reviews and credential rotation form a proactive governance model. They complement other PAM capabilities, ensuring that privileged access is granted appropriately and continuously verified, adjusted, and secured throughout its lifecycle.
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Conclusion
The long-term success of a privileged access management program often comes down to organizational commitment and continuous refinement. While the technical capabilities of PAM solutions are important, the quality of your implementation, your team’s adherence to established processes, and your ability to adapt to evolving threats can be the genuine differentiators that prevent security breaches and maintain compliance over time.
When evaluating your PAM strategy, focus on the most critical elements for your environment. Remember that privileged access management represents a fundamental shift in how organizations approach security. Rather than relying on perimeter defenses and static passwords, you’re implementing dynamic, context-aware controls that adapt to risk levels.
Ready to see how automated rollback capabilities can strengthen your privileged access management strategy? Schedule a demo of Cayosoft Guardian to discover how rapid privilege change detection and rollback can close critical security gaps in your environment.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content