Home » Best Practices for Robust Identity and Access Governance » Critical Recommendations for Identity Governance and Administration
Critical Recommendations for Identity Governance and Administration
Learn how identity governance and administration (IGA) assists organizations in managing digital identities, controlling access, and implementing best practices for secure access to resources and compliance.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Identity governance and administration (IGA) is a strategic discipline that enables businesses to manage digital identities to ensure secure access to resources and comply with legal obligations. It includes identity governance frameworks necessary to protect sensitive data, especially now that modern businesses increasingly adopt cloud services and hybrid infrastructure.
Fundamentally, IGA assists organizations in addressing the following questions:
- Who should have access
- How that access is used, and
- Who has access to what
This entails controlling access privileges using role-based and policy-based models, maintaining user identities, and implementing auditing and oversight tools.
The article discusses the essential best practices and recommendations, explaining how identity governance and administration drives contemporary identity and access management techniques.
Summary of identity governance and administration best practices
|
Best practices |
Description |
|---|---|
|
Establish a clear identity lifecycle process |
Define clear processes for provisioning, modifying, and deprovisioning identities. |
|
Implement role-based access control (RBAC) |
Utilize standardized roles to streamline access assignments and minimize unnecessary privileges. |
|
Conduct periodic access reviews |
Regularly review user access to ensure it aligns with job responsibilities. |
|
Enforce policy-based access controls |
Apply access policies based on business rules and risk profiles. |
|
Monitor and audit identity activities |
Continuously track identity usage and generate audit logs for compliance. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Establish a clear identity lifecycle process
The identity lifecycle includes stages such as internal transfers, role changes, offboarding, and onboarding. A clearly defined identity lifecycle procedure guarantees that users are granted access suitable for their positions and responsibilities throughout their time with the company. It ensures precise and timely modifications to access rights through the lifecycle stages.
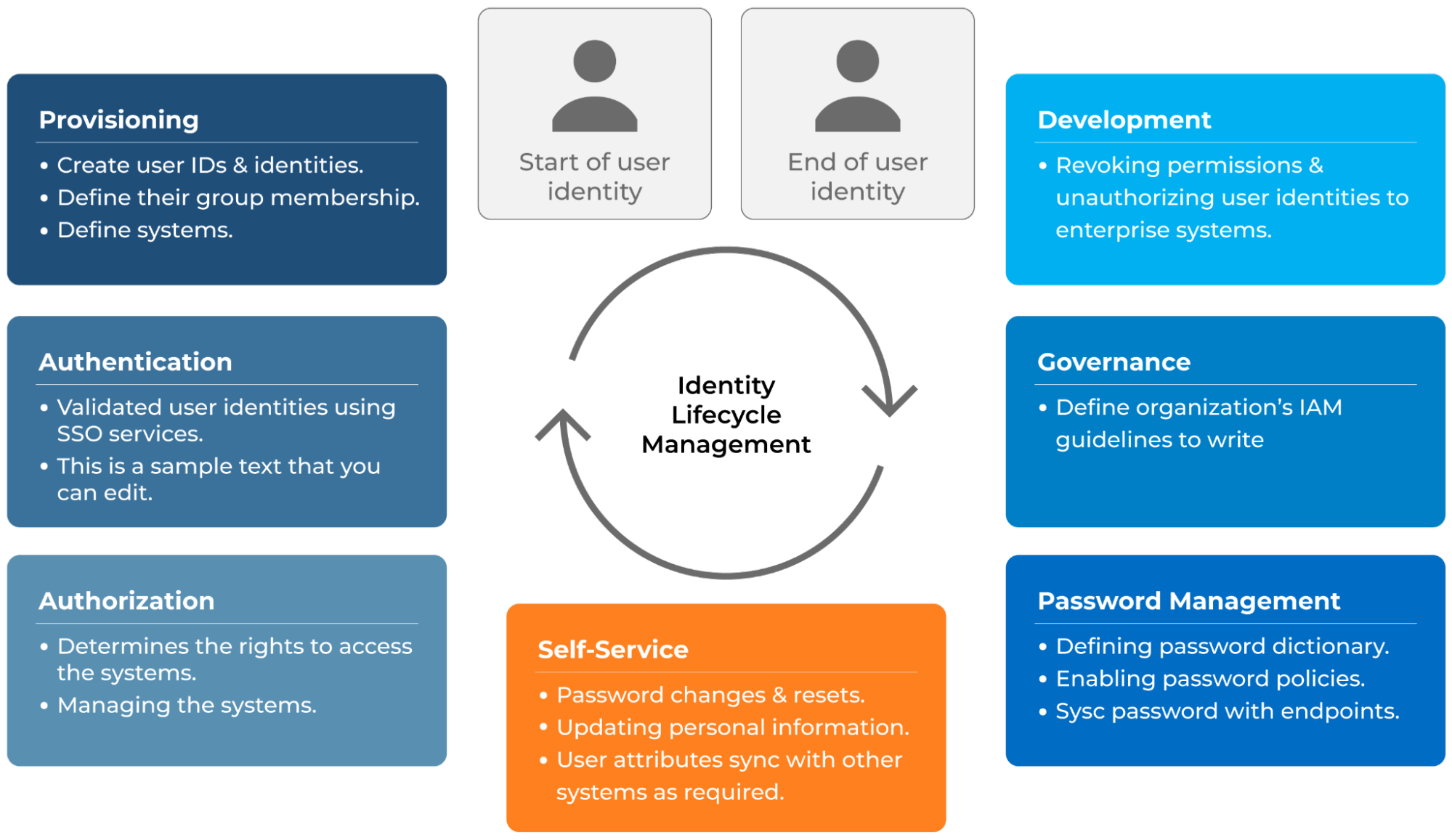
Administrators can drive identity processes by utilizing third-party solutions that specialize in IGA. These solutions typically include built-in features that automatically initiate provisioning workflows, such as:
- Assign access according to the user’s position when a new employee is hired.
- Instant modifications to access privileges in a role change.
- Deactivate or remove credentials during termination events.
Such automated integration facilitates adherence to access control regulations, streamlines user provisioning, and minimizes manual input. It also minimizes human mistakes and delays caused by manual operations. It reduces the possibility of unauthorized access and privilege creep, particularly in sensitive settings.
Automated workflows also provide traceability for auditing and regulatory reporting, ensuring consistent policy enforcement. Integrating automated lifecycle governance into identity procedures ultimately improves security while preserving operational agility.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Implement role-based access control (RBAC)
Role-based access control (RBAC) standardizes access provisioning according to precisely specified job tasks. It considerably lowers the risk of overprivilege by allowing businesses to map everyday tasks to specific roles rather than granting access as needed. This access standardization facilitates the uniform application of the principle of least privilege and expedites provisioning.
Dynamic RBAC
Some circumstances require access to be modified, such as due to policy enforcement, compliance requirements, or changes in role or organization. Dynamic role assignment automatically assigns users to jobs based on criteria such as position, region, and employment status. As a result, access entitlements are updated in real-time when user attributes change.
This dynamic RBAC capability is supported by many vendors offering attribute-based role management, such as Microsoft Entra ID and Cayosoft.
There are several other advanced techniques that you can implement with RBAC; however, implementing dynamic RBAC effectively increases responsiveness to abrupt organizational changes while reducing administrative expenses.
Principle of least privilege
The security best practice known as the principle of least privilege (PoLP) restricts and minimizes access permissions to resources to the bare minimum necessary to carry out a user’s designated activities. It is also essential for reducing the risk of security breaches and is implemented throughout the IT ecosystem.
For access provided over longer periods, adding the principle of least privilege to existing processes introduces complexity and can result in access entitlements becoming stale and outdated over time. When sudden organizational changes occur, dynamic RBAC may not be sufficient on its own. Hence, periodic access reviews become necessary.
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Conduct periodic access reviews
Access reviews allow organizations to validate that users maintain appropriate access over time. The timeframe of the review process is typically determined by the degree of risk associated with the systems and data in question. Lower-risk systems can be examined every three to six months, while higher-risk applications require more regular review cycles. However, every organization’s processes can vary.
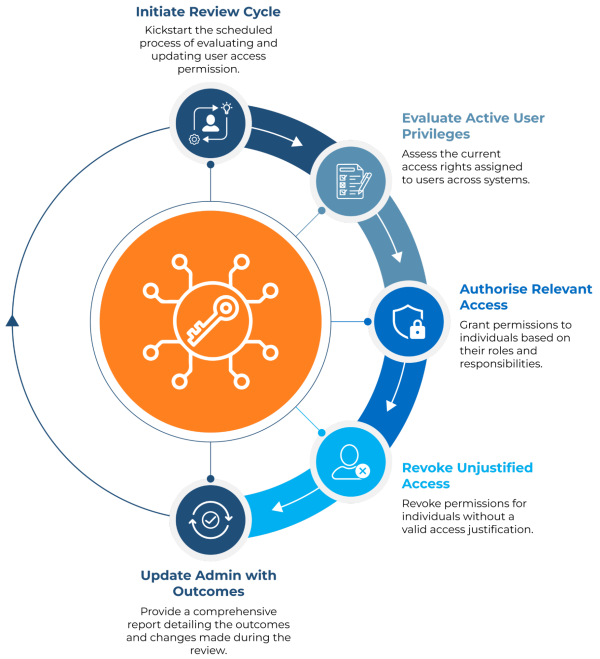
As a best practice, access reviews should include all stakeholders involved in a particular system being reviewed, such as managers, users, and application or product owners familiar with the access needs of their teams and systems. In addition to these processes, regular access reviews must go through multiple levels of approvers before access is granted. This procedure helps businesses identify unused or excessive access permissions, ensuring compliance within the principle of least privilege.
Credential rotation
Credential rotation refers to changing passwords or other authentication factors. As per the modern guidelines, a mandatory, periodic credential rotation for general user accounts is increasingly seen as unnecessary and can even lead to less secure practices. Instead, credential rotation for user accounts is now primarily recommended when a password is suspected or known to be compromised, or in response to specific risk events.
Despite this shift for general users, managing credentials remains critical, especially for privileged accounts and in response to threats. Modern solutions offer advanced capabilities to support this nuanced approach. They provide tools to automate password rotation for high-risk accounts and enable users to fetch their updated passwords in real-time via a password vault. These systems also allow for auditing of users who reuse passwords and those who don’t meet an organization’s established password complexity rules.
For example, Cayosoft Guardian can identify privileged accounts with weak password policies in on-premises Active Directory (AD), hybrid AD, and cloud Entra ID environments. Furthermore, Cayosoft Guardian actively monitors password-based attacks, like password spray attempts.
Monitor and audit identity activities
A strong IGA plan must include efficient identification, activity monitoring, and auditing. Constant visibility into how identities are used allows organizations to identify irregularities, enforce policies, and guarantee adherence to internal and regulatory standards. By recording and evaluating identity events, they can react quickly to potential attacks and setup errors before they escalate into security incidents
Here are a few recommendations to consider when planning a properly monitored and compliant identity governance and administration plan.
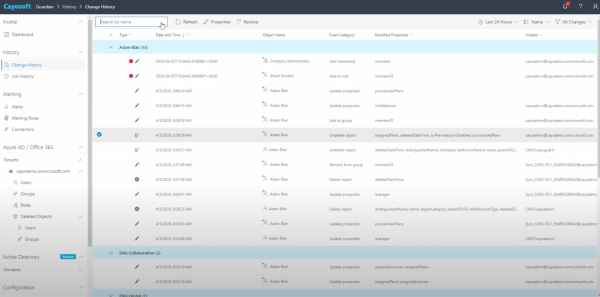
Enable continuous logging and alerting
Important IGA events defined in the lifecycle process, such as account provisioning, role modifications, access approvals, login attempts, and policy infractions, should all be recorded. Unauthorized access attempts and questionable privilege escalations can be detected with the aid of real-time alerts. SIEM solutions usually handle these features and offer centralized platforms for effective log data correlation and analysis.
Use dashboards for identity activity monitoring
Dashboards provide visual information that makes it easier to spot irregularities in identity usage trends. KPIs, such as the rate of access revocations or the time it takes to complete an access review, are also supported by dashboards. They enable the quick identification of unusual authorization changes, access from unexpected locations, and irregular login times.
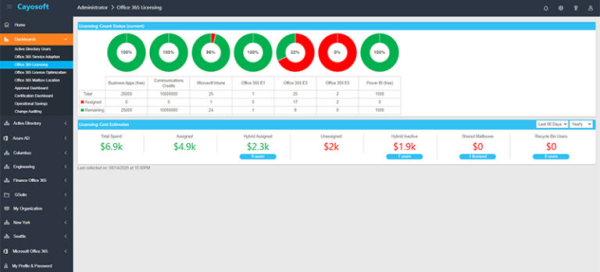
Retain logs for audit and compliance
Log retention should adhere to the time frames given by organizational guidelines or legal requirements. For the purposes of investigations and compliance audits, retained logs offer historical visibility. Cayosoft Guardian and Microsoft Sentinel are two such tools that enable customizable and legal retention setups.
Invest in user training and awareness
All stakeholders involved in the governance lifecycle should receive training on their responsibilities and the instruments used in IGA procedures. Training should begin with onboarding and be updated regularly to sustain comprehension and compliance. Knowledgeable users can mitigate risk by identifying governance issues and making informed access decisions.
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Final thoughts
A great identity governance lifecycle often comes down to an organization properly standardizing its process with continuous refinement over time. While the technical capabilities of IGA and their solutions are important, the quality of your implementation, the users’ adherence to established processes, and your ability as an administrator to adapt to issues and threats can be the major differentiators in improving efficiency and maintaining compliance over time.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content