Home » Best Practices for Robust Identity and Access Governance » Essential Capabilities of Access Governance Tools for Automated Policy Enforcement
Essential Capabilities of Access Governance Tools for Automated Policy Enforcement
Learn how access governance tools can alleviate the challenges of managing access security in a hybrid environment with features like unified administration and automated policy enforcement.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Access governance is one of the toughest challenges that IT admins face today. In a hybrid environment where your resources are scattered across on-premises data centers and a multitude of cloud platforms (such as Microsoft Entra ID), managing access security and keeping things under control is complicated. Access governance tools automate routine tasks, enforce policies consistently, and provide clear visibility across environments.
This article explores the pillars of true hybrid access governance, from unified administration to instant recovery. You’ll see how a comprehensive toolset can transform this challenge from a source of constant stress to the heart of your security strategy.
Summary of essential capabilities of an access governance tool
Choosing the right access governance tool is a critical decision that can impact your security posture, operational efficiency, and compliance standing. The following table provides a checklist of non-negotiable capabilities that can serve as a high-level guide when evaluating solutions.
| Capability | Purpose |
|---|---|
| Unified hybrid administration | Provides a single console to manage both on-premises Active Directory and cloud services (Entra ID, Microsoft 365), eliminating gaps in visibility and control |
| Granular least privilege enforcement | Moves beyond theory to provide the tools needed to easily implement and maintain the principle of least privilege (PoLP), drastically reducing the attack surface |
| Automated policy enforcement and lifecycle management | Automates user provisioning, modifications, and deprovisioning across all connected systems, ensuring security, consistency, and IT efficiency |
| Real-time monitoring and threat detection | Provides continuous visibility into all changes and access activities, enabling instant detection and response to unauthorized or risky modifications |
| Instant identity recovery | Delivers the ability to instantly recover from malicious or accidental changes to the identity infrastructure, ensuring business continuity |
| Comprehensive audit and compliance reporting | Helps generate detailed, exportable reports for auditors, with immutable change history |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Unified hybrid administration
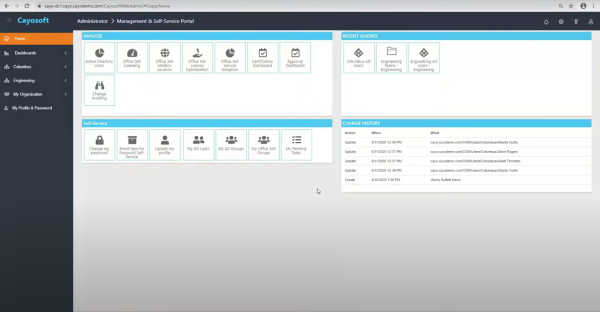
One of the biggest challenges in a hybrid Microsoft environment is the split between on‑premises Active Directory (AD) and cloud‑based Entra ID. Each has its own schema, tools, and quirks. For admins, that often means juggling multiple consoles, PowerShell modules, and reports just to complete routine tasks. There are risks associated with constant context‑switching because a single missed step or an inconsistent policy can leave security blind spots.
The solution many organizations turn to is real-time unified administration. Consolidating hybrid identities into a single view strengthens governance by eliminating blind spots and making the impact of any change immediately visible.
Native tools can cover these tasks separately, but they don’t deliver end‑to‑end, hybrid‑aware automation. Purpose‑built solutions such as Cayosoft are designed specifically for hybrid Microsoft environments to provide the “single pane of glass” that administrators need to unify and simplify identity management across AD and Entra ID.
Imagine needing to provision a new employee. Instead of a multi-step manual process across different tools, you can, from a single console:
- Create the user in the correct AD organizational unit (OU) based on their department.
- Add them to the appropriate on-prem security and distribution groups.
- Synchronize the user to Entra ID.
- Assign the correct Microsoft 365 license.
- Add them to the required Entra ID groups for SaaS application access.
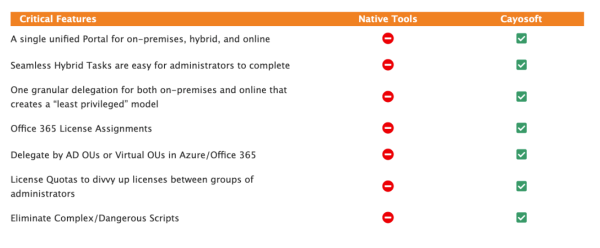
With centralized management, you eliminate the gaps where errors and misconfigurations occur. Native integration means the tool speaks the language of both AD and Entra ID fluently, translating administrative actions into the correct operations on each platform seamlessly.
Granular least privilege enforcement
The principle of least privilege (PoLP) is one of the foundations of cybersecurity. The principle states that users and systems should have only the access required to perform their work. For example, a receptionist should not be able to see financial reports; a sales manager should have access to sales records but not HR data.
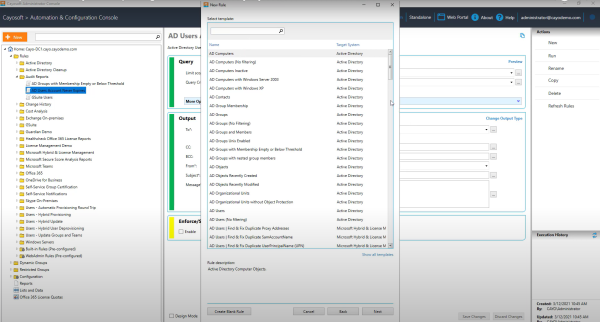
In practice, enforcing this principle across a large or mature environment is difficult. Native Microsoft tools rarely give administrators the level of precision they need. To delegate the task of resetting user passwords in a specific OU in Active Directory, for instance, you have to use the complex Delegation of Control Wizard. The granularity just isn’t there. This is another area where native tools fall short and it is highly recommended to leverage purpose-built solutions.
These gaps create two familiar problems in real environments. First, admins often compensate with ad hoc PowerShell scripts, which work for the person who wrote them but become a maintenance burden as teams change. Second, many IT leaders quietly accept “over‑delegation” because it is the only way to hand work off to front‑line staff without constant escalation. Neither approach is sustainable. Scripts introduce fragility, and over‑delegation can open doors for attackers.
Consider leveraging solutions that enable the true enforcement of least privilege by allowing organizations to delegate very specific tasks, not just broad permissions. This is a critical distinction. Instead of making someone a “Group Administrator,” you can create a role for your help desk that grants only the permissions needed to reset user passwords and unlock accounts, and scope it to apply only to users in a specific OU, such as sales.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Automated policy enforcement and lifecycle management
The governance risk of permission creep is a direct result of manual, inconsistent identity management processes. People join, change departments, get promotions, or leave altogether; each of these transitions requires precise and timely adjustments to their access rights. When the workflow (or sizable chunk of it) is manual, it’s most likely to fail in the long run.
The only scalable and reliable way to maintain a state of least privilege is through automation, particularly by tying access controls to the identity lifecycle. Your access governance solution must be designed to integrate directly with your authoritative source for identity information, which is typically an HR system like Workday, SAP SuccessFactors, or a simple database. Essentially, the integration allows the governance tool to:
- Detect the new entry
- Apply a role-based policy based on the user’s title, department, and location
- Create the user account in both on-prem AD and Entra ID with the correct attributes
- Assign the necessary software licenses and group memberships as needed
- Send a notification to the user’s manager with their login details
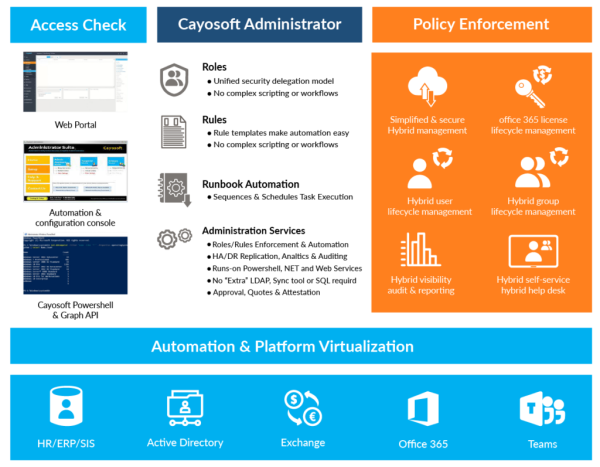
An automated process ensures that access is granted consistently and in accordance with predefined policies, eliminating the risk of human error and maintaining a least-privilege state from the outset. Similarly, when an employee leaves, the platform can automatically initiate a deprovisioning workflow that deactivates the account, revokes all group memberships, removes licenses, and archives the employee’s mailbox, ensuring a clean and secure offboarding.
Real-time monitoring and threat detection
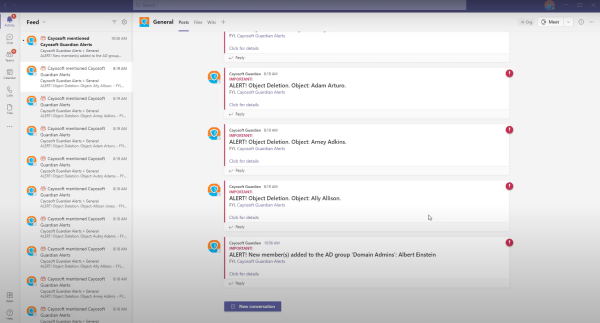
Microsoft provides native logs for AD and Entra ID, but anyone who has worked with them knows the reality: They are verbose, fragmented across consoles, and flooded with noise. Besides visibility, the time to respond while using these logs is another point of concern. Important events drown in routine chatter, and during a security incident, the time required to extract the relevant details can make the investigation feel impossible. In many cases, admins only notice a problem when users start reporting outages or when auditors request explanations weeks later. For example, if an administrator (or an attacker using their account) removes a security group or modifies directory synchronization settings, native tools leave IT with a messy and slow recovery.
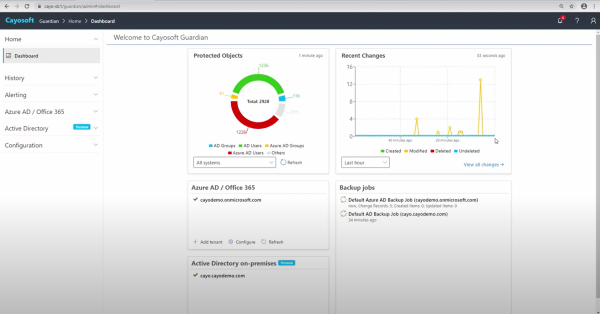
For this reason, real-time monitoring and threat detection are considered core components of an effective access governance suite. Different platforms address this differently. Cayosoft Guardian approaches this from two angles.
First, the tool can consolidate every change across AD and Entra ID into a single, readable trail with real-time alerts pushed into email, Teams, or your SIEM. That means admins see the right events at the right time without digging through endless logs.
Second, you can add immediate rollback. If a critical group is deleted, Guardian can restore it with all of its memberships intact in seconds. What normally takes hours of manual effort can be completed in a single controlled recovery step.
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Instant identity recovery
Prevention and detection are critical, but a governance strategy is incomplete without recovery. In the face of an attack, a robust access governance tool must go beyond simple backups and provide means to rapidly recover the core identity fabric to a “known-good” state.
Traditional disaster recovery methods for AD are notoriously slow, complex, and fraught with risk. A standard system state backup might restore your domain controller, but it might also restore the malware or backdoor that the attacker used to compromise it in the first place. An AD forest recovery using native tools is a painstaking, multi-day process that requires deep expertise and nerves of steel, all while the business is hemorrhaging money every minute it’s offline.
A specialized forest recovery platform shouldn’t just back up the virtual machine or the server’s operating system; it should continuously back up the identity data itself, such as the users, groups, attributes, and linkages that make up your directory.
When a failure occurs, the system can:
- Provision clean, patched replacement servers automatically.
- Restore identity data from trusted backups with integrity checks.
- Perform the metadata cleanup required for a healthy forest.
Having this level of automated, identity-aware recovery can reduce recovery time from days or weeks to just a few hours, ensuring rapid business continuity and minimizing the financial and reputational damage of an attack.
Comprehensive audit and compliance reporting
It doesn’t matter how secure your systems are if you can’t prove it to an auditor or compliance officer. For any organization subject to regulations such as SOX, HIPAA, GDPR, or PCI-DSS, the ability to produce detailed, accurate reports on who has access to what and who made changes to what is a non-negotiable governance requirement.
Anyone who has gone through an audit with only native Microsoft tools knows the pain. Collecting evidence usually means pulling logs from multiple controllers and cloud tenants, exporting CSVs, normalizing timestamps, and then trying to reconcile event IDs against plain-English actions.
When selecting a governance tool, factor in whether you can generate critical reports with just a few clicks. For example, can you:
- Generate an up-to-date roster of who can reach a sensitive application or share and route it to the business owner for attestation?
- Instantly list current members of groups like Enterprise Admins or Entra ID Global Administrators without combing through ADUC, PowerShell, or multiple portals?
- Know exactly what was modified, by whom, and when through time-stamped logs?
A centralized identity governance platform can remove the burden of such complex reporting considerably. Because it is the control point for administration, it automatically records changes in a clean, auditable database. The reports come from the same place where policies are enforced, so they are accurate, consistent, and instantly available.
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Conclusion
A useful governance tool does four things well: manage access, enforce policy, recover fast, and report clearly. Native Microsoft tools can handle pieces of this, but not with the depth or consistency most enterprises need (especially in hybrid environments).
Microsoft’s tools aren’t weak; they were just never built for governance in the first place. Active Directory, Entra ID, and PowerShell are administration platforms that assume perfect processes, consistent people, and enough time to manage every change manually. Enterprises don’t operate that way.
Cayosoft provides a complete solution that empowers administrators to overcome the complexities of modern access governance. Book a demo today to see how Cayosoft can help you simplify your identity and access governance.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Explore More Chapters
Next Chapter >