Home » Best Practices for Robust Identity and Access Governance » The Core Concepts of Identity Lifecycle Management
The Core Concepts of Identity Lifecycle Management
Learn about the foundational principles, stages, and governance of identity lifecycle management and its importance for secure and compliant access management in modern organizations.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
When a new employee joins your organization, HR notifies IT, which creates a user account. Permissions are granted so that the employee can access email, internal applications, and shared drives. Months later, though, that employee may shift departments, needing access to new systems and losing access to old ones. Two years later, that person leaves the company, and the organization assumes that IT removed their access.
But did it actually happen?
This scenario highlights the importance of identity lifecycle management (ILM). Irrespective of the size of an organization, ILM forms the foundation of secure, efficient, and compliant identity and access management. When ILM is neglected, organizations risk overprovisioned accounts, security breaches, compliance failures, and operational inefficiencies. This article examines the foundational principles, stages, and governance that underpin the entire process.
Summary of key identity lifecycle management concepts
To help discuss this issue, we frame it in the form of three key stages of ILM, which are summarized in the following table, as well as the important concept of identity governance.
| Stage/Concept | Description |
|---|---|
| Onboarding | The initial phase, where new user accounts are created and foundational access privileges are granted |
| Access management | The continuous process of modifying user rights and privileges as their roles evolve or responsibilities change within the organization |
| Deprovisioning | The final stage, where user accounts are deactivated or deleted and all associated access rights and privileges are revoked |
| Identity governance | The overarching policy and process framework that ensures that all lifecycle activities are secure and compliant |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
What is identity lifecycle management?
Identity lifecycle management (ILM) is the comprehensive process of controlling and overseeing digital identities within an organization from the moment they are created until they are finally removed. At its core, ILM ensures that every user, whether an employee, contractor, or even service accounts, has appropriate, secure access to the resources they need throughout their time with the organization, and only for as long as necessary.
The identity lifecycle typically follows three main stages, often referred to as the “joiner-mover-leaver” (JML) cycle:
- Onboarding (“joiner”)
- Access management (“mover”)
- Deprovisioning (“leaver”)
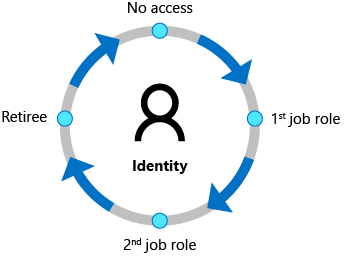
While this is a good starting point, it’s important to recognize that ILM goes far beyond simply creating usernames or resetting passwords. A modern digital identity includes a wide range of attributes and resources, such as the following:
- Attributes: Name, title, department, manager, office location, etc.
- Credentials: Passwords, multi-factor authentication (MFA) methods, and security keys
- Entitlements: Group memberships, application roles, and file share permissions
- Licenses: Microsoft 365 E3 licenses, Adobe Creative Cloud, etc.
- Resources: Mailboxes, cloud storage, and so forth
A robust ILM framework manages all these components not just at the point of onboarding, but continually throughout a user’s time with the organization and during their exit. It ensures that only the right people have access to the right resources, at the right time, for the right duration.
Many years ago, identity management was a simpler process: You had a server rack running Active Directory (AD), and that was that. Today, nearly every organization operates in a hybrid environment. You have a traditional on-premises AD that often sits alongside cloud-native Microsoft Entra ID (formerly Azure AD), each responsible for managing access to overlapping but distinct sets of applications and services.
These systems differ significantly in terms of how they structure user information, their approach to group management, and the tools available for administration. Attempting to manage identities across both environments using only native tools can create inconsistencies, security gaps, and user frustration. Policies set in one environment may not translate properly to the other, resulting in fragmented governance and potential exposure of sensitive data.
To address these concerns, organizations increasingly rely on purpose-built identity management solutions, which automate and orchestrate the entire lifecycle across both on-premises and cloud platforms. These solutions help enforce consistent policies, streamline user experiences, and significantly reduce the risks associated with manual errors or oversight.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Identity lifecycle management stage 1: Onboarding
The lifecycle begins the moment a new employee signs an offer letter; the onboarding process is your first opportunity to establish a secure and efficient identity foundation.
User provisioning
Gone are the days of manually creating user accounts based on service desk tickets. The process should be triggered directly from your source of truth for employee data: the HR system. When a new employee is added to the HR system, like SAP or Workday, an automated workflow should kick off to do the following:
- Create the user account: A new account should be created in on-premises Active Directory, Microsoft Entra ID, or both.
- Define identity attributes: This isn’t a one-size-fits-all process; it is a precise process based on predefined rules and templates. The system retrieves key data from the HR record, including name, job title, department, and uses it to populate the corresponding attributes in AD and Entra ID.
- Assign baseline permissions: This practical, templated approach applies role-based access control (RBAC), a model that grants access based on a user’s defined role within the organization. There is no guessing what access, for example, a new L1 cyber analyst needs; you assign them the “L1 Cyber Analyst” role, which comes with a predefined set of entitlements, such as access to specific file shares, applications, and distribution groups.
In larger organizations, manual onboarding is inefficient and prone to errors, so the entire sequence—from HR trigger to a fully provisioned, licensed, and permissioned user—can and should be fully automated. This is where a solution like Cayosoft Administrator acts as the intelligent workflow engine. It provides powerful, rule-based automation that takes information from virtually any HR/ERP/SIS system and completely provisions user accounts, assigning the resources required for the user to perform their job. Cayosoft Administrator can simultaneously create accounts in on-premises AD and Entra ID, ensuring consistency and eliminating the typical provisioning delays associated with synchronization tools.
Authentication
Once an account is provisioned, the user needs a way to prove their identity. Authentication is the process of verifying that an individual is genuinely who they claim to be before granting access to digital resources or sensitive information. Traditionally, this involves methods such as entering a username and password, but it may also include other means, such as personal identification numbers or biometric verification, including fingerprints or facial recognition. The primary goal of authentication is to ensure that only authorized individuals can access specific systems or data, thereby forming the foundation of a secure digital environment.
The onboarding stage is an opportunity to establish a strong authentication posture, which is about enrolling users in a resilient authentication framework. To understand this framework, we must first understand three recognized “factors” in authentication:
- Something you know: This is the most common and least secure factor. It’s a piece of sensitive information, such as a password, PIN, or the answer to a security question.
- Something you have: This is a physical object in your possession, like a YubiKey or a mobile phone receiving a push notification from the Microsoft Authenticator app.
- Something you are: This refers to biometric data, such as a fingerprint scan or facial recognition (like Windows Hello for Business).
Multi-factor authentication (MFA) is the practice of requiring a user to present at least two of these different factors before granting access. For example, a user might enter their password and then must approve a notification on their phone. According to Microsoft, enabling MFA blocks over 99.9% of identity compromise attacks.
As part of your onboarding workflow, you should enforce MFA registration on the user’s very first login. Microsoft Entra ID makes this simple to enforce through Conditional Access policies, ensuring that no user can access corporate resources until they have a strong, multi-factor authentication method registered.
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Identity lifecycle management stage 2: Access management
An employee’s role is rarely static. They get promoted, change departments, or join special projects. As their responsibilities shift, so should their access rights. This ongoing management is a critical and often overlooked part of the lifecycle.
Authorization
Before proceeding, it is important to understand the difference between authentication and authorization:
- Authentication is about proving your identity. Think of it as like showing your passport at airport security.
- Authorization is the act of granting permission to do something or go somewhere. It’s like a boarding pass that says that you’re allowed to go to Gate B7 and sit in Seat 14C (but not enter the cockpit).
The single most important philosophy governing authorization is the principle of least privilege (PoLP), which states that a user should only be granted the absolute minimum permissions required to perform their explicit job functions. The reason is simple: it minimizes risk. If a least-privileged user account is ever compromised, the attacker’s damage radius is severely limited.
So, how do we enforce this principle in a complex IT environment? By using structured access control models:
- Role-based access control (RBAC): When a user transitions from the sales team to the marketing team, you don’t just add new marketing permissions on top of their old sales permissions. Instead, a proper ILM process revokes the “sales” role and all its associated entitlements and assigns the “marketing” role. This ensures that the user’s access is always aligned with their current responsibilities, maintaining a state of least privilege.
- Attribute-based access control (ABAC): ABAC is a more dynamic and granular evolution of RBAC that makes authorization decisions in real time based on policies that combine attributes of the user, the resource, and the environment. For example, you can create a policy that states: “Grant access to the ‘Q3 Financial Projections’ file only if the user’s department attribute is ‘finance,’ the data’s classification label is ‘confidential,’ and the user is accessing from a compliant, corporate-managed device.” This context-aware model provides an incredibly powerful way to protect sensitive resources.
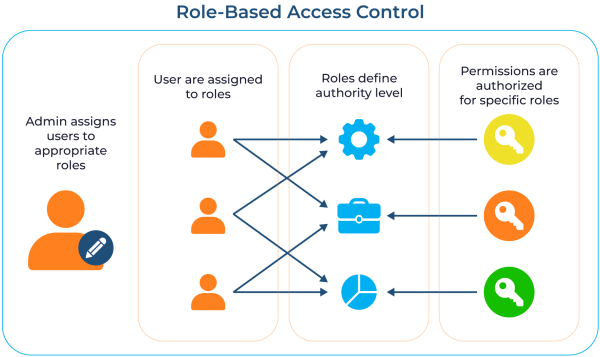
Managing these models across a hybrid environment, where permissions for on-premises file shares reside in Active Directory and access to cloud apps is governed by Microsoft Entra ID, is a significant challenge. This is where a unified dashboard, such as Cayosoft Administrator, becomes indispensable. It allows you to manage roles and access policies for both on-premises AD and Microsoft Entra ID from a single console. You can create powerful rules that use attributes to dynamically manage group memberships across your entire hybrid environment. For example, a single rule in Cayosoft can automatically add a user to an on-prem security group and a cloud-based Microsoft 365 Group when their job title changes. This ensures that your access control policies are enforced consistently, instantly, and accurately across your entire identity fabric, dramatically reducing both security risks and administrative toil.
Access reviews
Even with perfect onboarding, permissions tend to drift over time. A user is added to a project team for a few weeks, a manager grants temporary access to a sensitive folder for a quick task, and so on. Individually, these actions seem harmless. Collectively, they lead to a dangerous phenomenon: privilege creep.
An access review, also known as an access certification or attestation, is the formal process of reviewing and validating who has access to what. It is the essential security check-up that actively combats privilege creep and reasserts the principle of least privilege.
The old way of performing access reviews was a nightmare. It was manual, impossible to track, and so painful that it was rarely done effectively, if at all. Modern identity governance and administration (IGA) tools automate this entire workflow. Here’s how it should work:
- Automated campaigns: The system automatically initiates a review campaign on a predefined schedule (e.g., quarterly or annually).
- Intelligent assignment: The campaign intelligently assigns the review task to the person with the right context, typically the resource owner or the user’s direct manager, as listed in your identity system.
- Remediation: The manager receives a notification and is presented with a simple, web-based list of their direct reports and the access they hold. For each permission, they have a simple choice: approve or revoke.
The most critical part of this process is the final step: remediation. In the context of ILM, this phase can easily be overlooked, yet it’s essential for maintaining security and compliance. When a manager clicks “revoke,” it isn’t enough for the decision to simply be recorded; actual removal of access must follow. If this step is omitted, users may retain unnecessary privileges, which can lead to potential security risks and compliance issues.
Automation plays a vital role here, ensuring that as soon as access is revoked, the system promptly and reliably executes the removal. While platforms like Microsoft Entra ID have built-in features for running these access review campaigns in the cloud, remediation in a hybrid environment introduces an additional layer of complexity. A manager might revoke access to a cloud application, but what about the user’s permissions to the on-premises file share that belongs to the same project?
Having a unified hybrid management tool in situations like this can make a significant difference. While an access review platform determines what needs to be changed, a solution like Cayosoft Administrator can be the engine that robustly executes that change. Once a revocation decision is made, Cayosoft’s automation capabilities can ensure that the user is consistently removed from the necessary groups and entitlements across both on-premises Active Directory and Microsoft Entra ID. This guarantees that the decisions made during the review are fully enforced across your entire hybrid identity fabric, effectively closing the loop and eliminating the risk.
Self-service
Traditionally, IT has been the gatekeeper for every access request, and although this is for a good reason, it creates a bottleneck. The modern approach is to implement a secure self-service model that empowers users to manage common aspects of their digital identity. If well designed, this can deliver a win-win situation. For instance, consider the impact of eliminating the most common help desk tickets, such as password resets. For the IT team, this reclaiming of countless hours allows them to focus on proactive security hardening and system improvements. From the user’s perspective, they no longer need to file a ticket and wait hours for a simple password reset, thereby reducing frustration and allowing them to be more productive.
However, self-service does not mean a free-for-all. A robust approval workflow must govern every request for elevated access. These workflows ensure that the right person validates every request before access is granted. Let’s walk through a typical workflow:
- Request: Sarah, a user in the marketing department, needs access to new video editing software. She goes to the self-service portal, finds the application, and clicks “Request Access.”
- Trigger: The system detects that this application requires a license, initiating a single-stage approval workflow.
- Approval: A notification is automatically sent to Sarah’s manager, who is dynamically looked up from her user profile. The manager verifies the business need and clicks “Approve.”
- Execution and Provisioning: Once the approval is given, the system automatically provisions Sarah’s account in the application, assigns the license, and adds her to the “Video Editors” security group.
- Notification: Sarah receives an email confirming that her access has been granted.
Setting up these hybrid-aware workflows is a core strength of a comprehensive management solution. For instance, Cayosoft Administrator comes with self-service password management capabilities that integrate seamlessly with your environment, reducing IT workload and empowering users to change existing passwords, reset forgotten passwords, and unlock their accounts independently, without costly delays.
Identity lifecycle management stage 3: Deprovisioning
Deprovisioning is often the most critical and most overlooked phase of the identity lifecycle. While provisioning grants access to new joiners, deprovisioning revokes it from those who no longer require it. Failing to remove access promptly creates security gaps, and the longer accounts linger unused, the greater the risk that they can be compromised or misused.
This risk materializes in the form of orphaned accounts. These are user identities that remain active after an employee leaves, a contractor’s engagement ends, or a service is retired. Each orphaned account represents an unmonitored entry point, ripe for lateral movement or privilege escalation by malicious actors. In regulated industries, these abandoned identities can also lead to compliance violations, hefty fines, and reputational damage.
A secure deprovisioning process must be swift, thorough, and automated. It should include:
- Immediate disabling: The moment the HR system flags an employee as terminated, their primary accounts (Active Directory, Microsoft Entra ID) should be disabled instantly. This immediately cuts off all access.
- Data and asset transfer: A workflow should be initiated to transfer ownership of their files, emails, and other digital assets to their manager.
- License reclamation: Software licenses should be reclaimed and returned to the pool immediately.
- Eventual deletion: After a specified period (e.g., 30-90 days), the disabled account should be permanently deleted in line with company policy.
Manually coordinating these steps across multiple teams is a recipe for disaster. Automating this with Cayosoft ensures that nothing is missed and that every departure is handled consistently and securely, closing a major potential security gap.
Identity governance
Identity governance sits at the top of the identity lifecycle framework, serving as the overarching discipline that binds together provisioning, authentication, authorization, and deprovisioning. Without effective governance, each individual process operates in isolation, leaving gaps in oversight, risking policy drift, and undermining your ability to demonstrate regulatory compliance.
At its core, identity governance codifies your organization’s security policies into actionable controls. It ensures that access requests, approval workflows, and periodic reviews adhere to standardized rules rather than ad hoc decisions. For example:
- Access request policies define who may request elevated privileges, under what circumstances, and through which approval channels.
- Separation of duties (SoD) controls automatically prevent conflicting entitlements, such as approving your expense reports.
- Periodic access reviews prompt resource owners to certify that current access remains valid. Automated reminders and reporting in Cayosoft help ensure that these reviews occur on schedule and that recertification actions are recorded.
Governance provides the answers to critical audit questions: Who has access to what? When was it granted? Who approved it? Why do they have it? By embedding governance into your ILM processes, you create a system that is not just efficient but also transparent and provably secure. It provides the clear audit trail needed to satisfy regulators and give your leadership team peace of mind.
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Conclusion
Identity lifecycle management (ILM) is a business-critical control point. Every employee, contractor, or partner who touches your systems represents both an operational dependency and a security risk. If identities are not governed end to end, organizations face higher costs, audit failures, and a broader attack surface.
Executives should view ILM as a continuous program that delivers three measurable outcomes:
- Risk reduction
- Cost efficiency
- Regulatory assurance
Unlike native tools that only cover pieces of the puzzle, Cayosoft is built to manage the entire identity lifecycle across hybrid environments. It automates provisioning and deprovisioning, enforces policies at scale, and provides compliance reporting out of the box. In practice, this means fewer orphaned accounts, faster onboarding, better license management, and a stronger security posture without adding staff.
Book a demo to see exactly how these workflows run, how reporting supports compliance, and how automation can replace the manual tasks currently slowing down your team.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content