Home » Best Practices for Robust Identity and Access Governance » Identity Governance Solutions: A Comprehensive Guide to Modern Access Control
Identity Governance Solutions: A Comprehensive Guide to Modern Access Control
Learn how identity governance solutions can address the challenges of managing access to resources in a remote-first and cloud-first world, ensuring secure and compliant access for the right people.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
In a remote-first and cloud-first world, every organization needs to monitor and manage access to resources, specifying who has access, when, and for what purpose. Today, they have a bigger attack surface area to protect, evolving threats to manage, and increasing compliance and regulatory requirements to meet. Simply managing identity and access falls short of meeting these challenges.
This article will examine how identity governance and identity governance solutions help address these challenges, ensuring that the right people can access the necessary resources at the appropriate time.
Summary of key identity governance solutions features
The table below summarizes the essential features an identity governance solution must have, which this article will explore in more detail.
| Terminology | Description |
|---|---|
| Identity lifecycle management | Process of automating user identity creation, modification, and deletion from onboarding to offboarding. |
| Access lifecycle management | Involves automating the assignment, modification, and removal of access privileges for a user identity. |
| Segregation of Duties (SoD) | A security principle that divides a critical task between multiple people to avoid one of them from taking unilateral actions. |
| Least privilege access | A security principle that grants identities only the minimum required permissions necessary to perform a task. |
| Identity sprawl check | The uncontrolled and rapid growth of user identities. |
| Access creep check | Gradual accumulation of access permissions over time with changing roles. |
| Unified console | A unified console simplifies identity governance and management across multiple systems. |
| Audit trails | Centralized and immutable audit trails enable accountability, security, and compliance. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Introduction to identity governance
Identity governance is an approach to managing and controlling access to digital identities. It ensures that the right people have the minimum necessary access to resources and data, based on their roles and responsibilities, and that this access aligns with business needs.
While Identity and Access Management (IAM) focuses on authorization and authentication, identity governance focuses on ongoing oversight of identities based on policies, processes, and technologies.
The objective is to reduce risk and improve security posture through regular and consistent review of identities and the level of access permissions they have. Some of the questions organizations can answer through identity governance include:
- Who has access to confidential resources?
- Why do they have access to confidential resources?
- Should they continue to have access to these confidential resources?
- Are there orphaned identities that may pose a threat?
Identity governance framework
Today, organizations use multiple systems, both on-premises and in the cloud, and users of different roles are spread across different geographies. Manually managing and reviewing identities on such a large scale can be challenging.
An identity governance framework consists of standards, policies, and processes driven by a tool that enables an organization to manage, review, and certify identities and their access privileges, including privileged access. A framework also helps organizations keep up with changing identity management and compliance requirements.
Advantages of identity governance
Identity governance provides practical benefits, including enhanced security, reduced risk of unauthorized access, early mitigation of access risks, improved compliance, and enhanced audit readiness. Specifically, it provides the following advantages:
- Automated identity lifecycle management from onboarding and offboarding. Thus, when users leave the organization, their identity and access are automatically revoked, avoiding security risks.
- Automated access reviews and an auditable record of access details enable organizations to meet compliance requirements and pass audits. Financial organizations are subject to multiple stringent regulations, such as GDPR, FFIEC, GLBA, etc. Identity governance is especially beneficial in avoiding fines and reputational damage due to non-compliance.
- Separation of Duties (SoD) is enabled by policies that prevent a single user from having conflicting access permissions that can lead to malicious activity.
- Improved compliance and audit readiness from a centralized and unified view of identity permissions across multiple systems, such as on-premises, cloud, and even third-party applications.
- Granular audit trails with proper identity governance in place, organizations have an auditable record of access approvals and detailed audit trails covering access requests and approvals, making it easier to produce documentation for compliance requirements.
- Elimination of privilege creep because access reviews and certifications help identify and eliminate the accumulation of access permissions over time, also called privilege creep.
An identity governance solution is essential for highly regulated industries, such as financial services, that handle sensitive customer data, including customer IDs, bank details, transactions, card information, and other personally identifiable information (PII). It is an efficient, effective, and probably the only viable way to ensure data security and compliance today.
Without a framework and a solution that can help you implement, manage, and monitor it, an organization will face challenges such as:
- Identity sprawl, where there is uncontrolled growth of identities across applications, systems, and platforms, sometimes even creating duplicates.
- Access creep occurs when users accumulate access permissions that no longer meet their current job requirements. For example, an IT administrator who moved from the finance team to the HR team may retain permissions to financial systems.
- Unmet compliances or compliance violations occur when organizations cannot provide detailed access information, access reviews, and evidence of least-privilege principles.
- Security blind spots due to a lack of visibility into access details, orphaned accounts, and access privileges.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Components of identity governance solutions
An identity governance solution must include basic components, such as identity lifecycle management, access workflows (including requests, approvals, and reviews), policy enforcement, segregation of duties, and visibility. We discuss these points in more detail below.
Identity lifecycle management
One of the foundational components of an identity governance framework is automating the user journey from creation to job role changes and deletion. Automation ensures that identities are created quickly on demand, adjusted as the user’s role changes, and revoked when the user leaves the organization, thereby eliminating the risks associated with orphaned accounts. Automation also reduces administrative overhead in managing the lifecycle of these identities.
Identity lifecycle management generally follows the ‘Joiner, Mover, Leaver’ (JML) process.
- Joiner: This phase of the process involves onboarding activities of new users (or employees), such as creating digital identities and access to resources, data, and applications.
- Mover: This phase involves changes to a user’s role, department, or location and, thus, access permissions.
- Leaver: This phase involves offboarding activities for users (or employees) who leave an organization, such as revoking permissions and deleting identities.
Access lifecycle management
Users’ access rights change over the course of their employment as they move across roles and contracts. Access lifecycle management involves periodically reviewing and certifying user access to ensure it is still relevant and necessary. This involves using contextual information, such as user sign-in activity and frequency, to make risk-based decisions. Access lifecycle management is crucial for compliance and a strong security posture.
Segregation of Duties (SoD)
Segregation of Duties or Separation of Duties (SoD) is also a fundamental control that identity governance frameworks must include. It prevents a single user from taking unilateral actions, especially irreversible actions. For example, a user who can create a financial transaction and also approve it.
Role-Based Access Control (RBAC)
Identity governance frameworks should define roles based on business functions and assign access privileges using the principle of least privilege. These roles and permissions should be managed and enforced centrally with periodic reviews.
Reporting and logging
Identity governance solutions should provide detailed reports and logs that help organizations with audits and demonstrate necessary compliance with regulations such as GDPR, HIPAA, and SOX. An audit trail provides comprehensive information about identity activities, answering questions such as who accessed what, when, and why.
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Identity Governance Solutions
The industry benchmark for cloud-native identity governance solutions is Microsoft Entra ID Governance. In the following section, we discuss its core capabilities and explore how Cayosoft complements Entra ID Governance by seamlessly extending, securing, and managing governance policies across complex hybrid Active Directory environments.
Microsoft Entra ID Governance
Microsoft Entra ID Governance is part of the Microsoft Entra Suite and extends Entra ID’s already powerful identity and access management capabilities. It is a preferred choice for organizations deeply invested in the Microsoft ecosystem. Using Entra ID Governance, you can govern and secure the lifecycle of identities and their access to groups, applications, and resources over time, along with privileged access governance.
The following image shows the identity, access, and privileged lifecycle when using Microsoft Entra ID Governance.
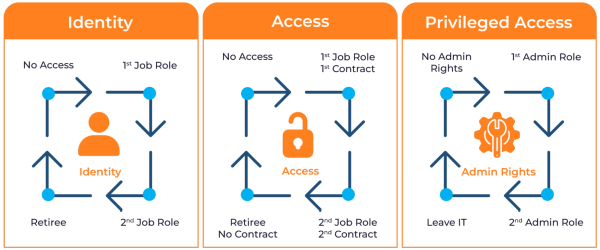
Additionally, you can automate many of the identity governance tasks in the Identity Governance section of the Microsoft Entra admin center.
While Microsoft Entra ID is a powerful identity management and governance solution, administering identities, especially in a hybrid environment that uses Active Directory, is still challenging. Even while using native tools, multiple consoles are required for hybrid identity administration. It also lacks advanced capabilities such as automated group memberships, including dynamic updates to them, automated user provisioning, license optimization, unified delegation across hybrid environments with granular access, and dynamic policies.
Cayosoft Administrator’s automation and management capabilities solve the complexities of identity lifecycle management in Microsoft hybrid environments across on-premises Active Directory (AD) and cloud-based Microsoft Entra ID (Azure AD) by addressing these challenges. It can automate user provisioning and de-provisioning while utilizing role-based access control (RBAC) to enforce the principle of least privilege, thereby eliminating manual and error-prone processes. A single console centralizes all identity-related tasks, including user, group, and license management.
Cayosoft’s Guardian is another product that further complements this by providing continuous monitoring, unified change history across hybrid systems, and security capabilities, such as detecting and mitigating malicious changes or unusual activities, including privilege escalation. It also provides a recovery feature that enables the rollback of unwanted or accidental changes.

Choosing an identity governance solution
Selecting an identity governance solution is a strategic decision for an organization that must align with the business requirements, technology landscape, environments, and risk profile. You must consider the following when choosing one:
- The ability to integrate, discover, and manage identities across diverse environments, such as on-premises, cloud, and hybrid. Organizations will lack unified visibility and effective governance without broad integration and connectivity.
- Detailed reporting and comprehensive audit trails for satisfying regulatory compliance requirements.
- Robust access certifications and Separation of Duties enforcement.
- A user-friendly and intuitive self-service portal for users and managers for access requests, approvals, and certifications for better adoption.
- A vendor that provides reliable support, a future roadmap, and continuous updates to keep pace with changing identity governance requirements.
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Conclusion
Identity governance is crucial to an organization’s cybersecurity and compliance strategy. They provide oversight into the organization’s identity and access posture, ensuring that the right people have the right access to resources at the right time. Identity governance helps improve security posture, especially in areas related to unauthorized access, meet compliance requirements, and improve audit readiness. Automating access management also enhances operational efficiency and reduces costs. Simply put, effective identity governance solutions and workflows enhance user experience, improve security, and positively impact the bottom line.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content