Home » Best Practices for Robust Identity and Access Governance » Understanding the Foundational Elements of Federated Identity Access Management
Understanding the Foundational Elements of Federated Identity Access Management
Learn about the foundational pillars and key components of federated identity and access management, including its role in IAM and Zero Trust architectures.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
IT and security teams often find that the administrative overhead of manually provisioning, managing, and deprovisioning accounts across dozens of disparate systems is immense. A lack of centralized visibility makes it difficult to enforce consistent access policies, track user activity, and ensure timely deprovisioning, resulting in orphaned accounts and significant compliance risks.
Federated identity and access management (FIAM) is a strategic framework that addresses these challenges. It enables users from different organizations or domains to access shared resources using a single, unified set of credentials managed by a trusted central authority.
This article breaks down the complexities of federated identity and access management, exploring the principles, components, technologies and best practices of FIAM.
Summary of foundational pillars of federated identity and access management
The following table lists key fundamental elements that define and govern FIAM.
Element | Core function |
Identity federation and trust framework | Establishes secure, policy-based trust between separate domains and organizations |
Transactional roles and actors | Defines the functional architecture and roles of the user (principal), identity provider (IdP), and service provider (SP) in a federated transaction |
Identity exchange mechanism | Administers key federation standards (SAML, OAuth 2.0, OIDC) for interoperable and secure identity communication |
Attribute-based access control | Passes user attributes in assertions to enable granular, context-aware authorization at the service provider |
IAM and Zero Trust architecture | Aligns FIAM with broader IAM and zero-trust principles for adaptive access control |
Identity assurance and auditability | Provides critical guardrails for data protection, identity assurance, and auditability to meet regulatory standards |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Identity federation and trust framework
Identity federation is a system that establishes trust among two or more domains for the purpose of authenticating users and sharing the information needed to authorise their access to resources. It allows a user to authenticate once in their home domain and gain access to resources in other domains through a trust framework without requiring reauthentication.
This “trust” is a technical and policy-based relationship that is formally established by exchanging metadata, which includes cryptographic public keys (digital certificates) and endpoint URLs for communication. This initial exchange allows each party to verify the authenticity of all subsequent messages cryptographically.
Here are some reasons why you may need identity federation:
- Scalability: Onboarding external partners, contractors, or organisational units becomes easier because you reuse identity rather than create new silos.
- Security: Federation reduces credential proliferation because there are fewer places where passwords are stored or reused.
- User experience: It enables single sign-on (SSO) across federated domains.
- Governance: Identity federation enables centralized auditability of federation relationships and access flows.
Key components and their roles
At the core of a federated identity architecture are three essential components, each fulfilling a distinct role:
- User (or principal): The individual attempting to access a resource.
- Identity provider (IdP): The authoritative system responsible for creating, maintaining, and managing identity information and authenticating the user. Examples include Microsoft Entra ID or an on-premises Active Directory Federation Service (AD FS).
- Service Provider (SP): The application or resource the user wants to access. The SP trusts the IdP to perform the authentication and consumes the identity information provided by the IdP to make an authorization decision.
The typical federated workflow proceeds as follows:
- A user attempts to access an SP (e.g., navigates to a SaaS application).
- The SP, recognizing that the user is unauthenticated, generates an authentication request and redirects the user’s browser to the IdP.
- The IdP challenges the user to authenticate (e.g., with a username, password, and multi-factor authentication).
- Upon successful authentication, the IdP packages the user’s identity information into a security token, known as an assertion. This token is digitally signed with the IdP’s private key.
- The IdP sends this signed token back to the user’s browser, which then forwards it to the SP.
- The SP receives the token, validates the IdP’s digital signature, and extracts the user’s identity information. If the signature is valid, the SP trusts the information, establishes a session for the user, and grants access.
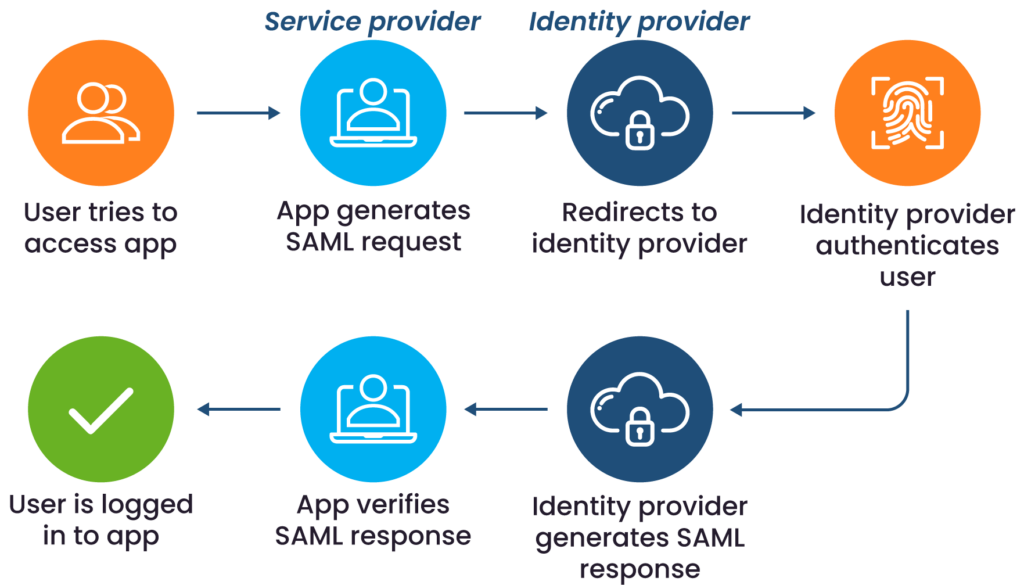
Federated authentication flow: single sign-on (source)
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Standard protocols and technologies
For federation to work across different vendors and platforms, it relies on open standards that define how authentication and authorization information are exchanged securely. Security Assertion Markup Language (SAML), OAuth 2.0, and OpenID Connect (OIDC) are the dominant protocols used.
SAML 2.0
Security Assertion Markup Language (SAML) is primarily an authentication protocol designed for enterprise-grade SSO. It answers the question: “Is this user who they say they are, and what can you tell me about them?” It uses XML-based “assertions” that contain statements about the authenticated user, including their identity and relevant attributes (e.g., group memberships, department). SAML is robust and well-suited for web-based enterprise SSO, such as employees accessing corporate SaaS applications or for B2B federation with partners.
OAuth 2.0
OAuth 2.0 is strictly an authorization framework, not an authentication protocol. It is designed to answer a different question: “Can this application have permission to access this user’s data on their behalf?” It defines flows for a user to grant a third-party application limited access to their resources on another service without sharing their credentials. It issues “access tokens” that represent a specific set of permissions (scopes) for a limited time and is fundamental for modern API security and mobile applications, such as allowing an app to access your Google Calendar.
OpenID Connect (OIDC)
OpenID Connect (OIDC) is an authentication layer built directly on top of OAuth 2.0. It standardizes the process of using OAuth 2.0 for user login, effectively answering the question: “Who is this user?” OIDC extends OAuth 2.0 by introducing an ID token, which is a JSON web token (JWT) containing claims about the authentication event (who was authenticated, by which IdP, and when). The application receives both an access token (for API authorization) and an ID token (for user authentication). OIDC is the modern standard for consumer and mobile app logins (such as “Sign in with Google”) due to its lightweight JSON/JWT format and API-friendly nature.
Protocol comparison
The following table summarizes the protocols described above.
Feature | SAML 2.0 | OAuth 2.0 | OpenID Connect (OIDC) |
Primary Function | Authentication and authorization (Federated SSO) | Authorization (delegated access) | Authentication (identity layer on OAuth 2.0) |
Token Format | XML (SAML Assertion) | JSON (access token; format not strictly defined) | JSON (JWT for ID token, plus access token) |
Primary Use Case | Enterprise SSO (e.g., employee access to corporate SaaS apps), B2B federation | Third-party API access (e.g., “App X wants to access your contacts”) | Modern consumer/mobile SSO (e.g., “Sign in with Google”), API authentication |
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Attribute-based access control
Traditional role-based access control (RBAC) models, where permissions are tied to static roles such as “manager,” often struggle with “role explosion” in complex environments and lack the necessary context for making dynamic, fine-grained decisions. Attribute-based access control (ABAC) is a more advanced authorization model in which access rights are granted dynamically by evaluating policies based on the attributes of the user, the resource, the requested action, and the environment.
In a federated context, the IdP can embed these rich attributes (e.g., role, department, or security clearance) directly into the SAML assertion or OIDC ID token. The SP then consumes this token, extracts the attributes, and feeds them into its local authorization engine to make a real-time access decision based on a predefined policy.
For example, a policy could state: “A user with the attribute role=Manager can action=approve a resource_type=expense_report only if the resource_attribute.amount is less than their user_attribute.approval_limit.”
However, the power of ABAC is directly proportional to the quality and reliability of the attributes it uses. If attributes are inaccurate or outdated (e.g., an employee changes roles but their department attribute is not updated), the entire security model fails. This challenge is magnified in hybrid environments, where attributes may exist in both on-premises Active Directory and cloud directories such as Entra ID.
Making ABAC a reliable security model requires robust identity governance and data hygiene. Cayosoft Administrator addresses this by providing rule-based automation and centralized control over identity attributes across hybrid AD and Entra ID environments. By automating identity lifecycle management based on a source of truth, such as an HR system, Cayosoft ensures that attributes are consistently and accurately maintained. This enforcement of data hygiene provides the clean, reliable attribute data that is essential for ABAC policies to function securely and effectively.
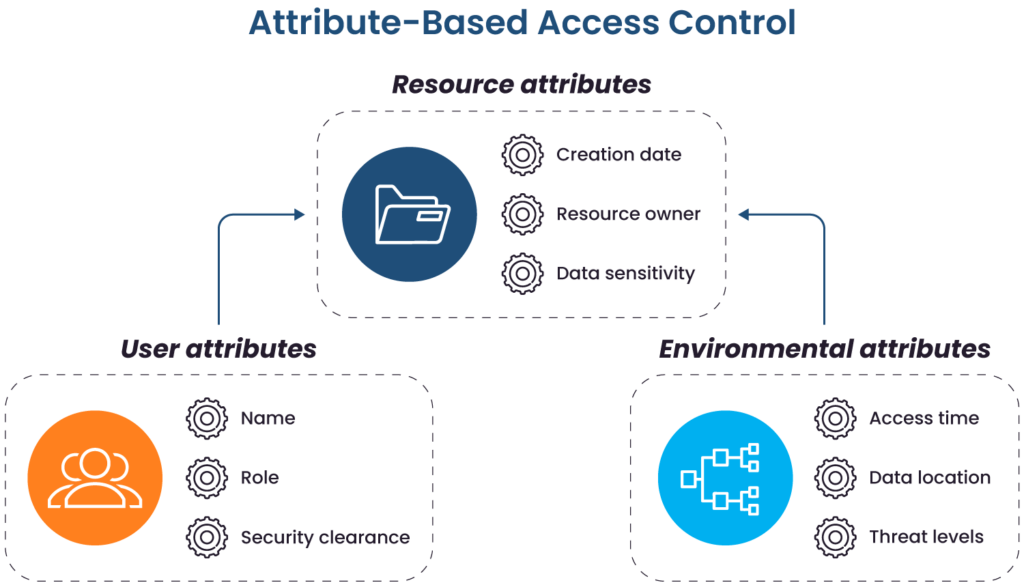
Attribute-based access control (source)
Integration with IAM and zero-trust architectures
FIAM is not a standalone solution but rather a foundational component of a comprehensive identity and access management (IAM) program. It is the mechanism that extends a central IAM policy engine across organizational and network boundaries. This capability makes it a critical enabler for modern security paradigms, such as zero trust.
Zero-trust architecture (ZTA) abandons the traditional security approach, which inherently trusts users and devices inside the network perimeter. Instead, ZTA operates on three core principles:
- Never trust, always verify: No user or device is trusted by default. Every access request must be authenticated and authorized, every single time.
- Assume breach: Security controls are designed with the assumption that an attacker is already inside the network. The goal is to prevent lateral movement.
- Least privilege access: Users and devices are granted the minimum level of access required to perform their function and for the minimum time necessary. This is an important best practice for identity and access governance.
FIAM is essential for implementing zero trust in a distributed, multi-cloud world. It directly enables the “never trust, always verify” principle by forcing every cross-domain access request through a centralized IdP for strong authentication, such as MFA. Furthermore, by passing rich, real-time attributes for ABAC, FIAM provides the context-aware signals (e.g., user identity, device posture, location) that a zero-trust policy engine needs to make dynamic, per-request access decisions.
Implementing zero trust across a hybrid environment (on-prem AD and cloud Entra ID) is complex. Inconsistent policies and administrative silos create security gaps that undermine the ZTA model. A true zero-trust architecture requires unified policy enforcement across all identity domains.
Cayosoft Administrator enables organizations to define granular, rule-based delegation models that enforce the principle of least privilege for administrators, thereby significantly reducing the risk of misconfigurations in federated access settings. With automated identity lifecycle management and enforced consistent policies across both on-premises and cloud environments, Cayosoft helps build the resilient, unified identity fabric that is the foundation of any successful zero-trust strategy.
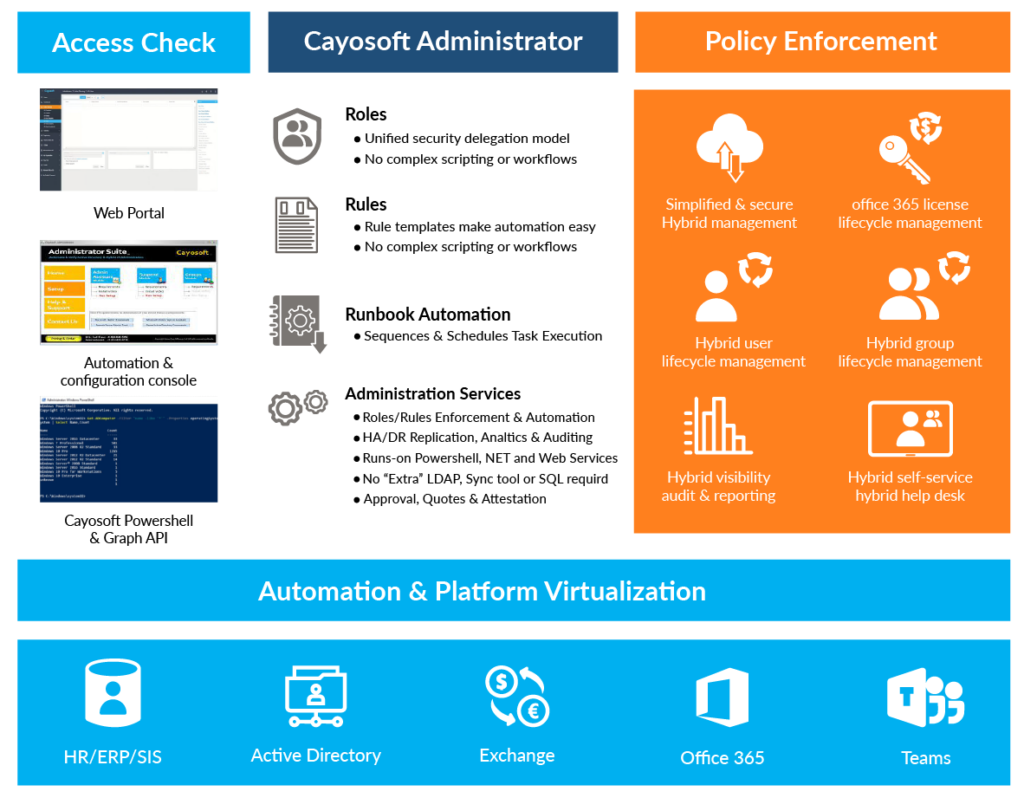
Architecture of Cayosoft Administrator
Security and compliance considerations
While powerful, federated systems introduce unique security challenges. The centralized nature of the IdP means that its compromise can become a single point of failure, potentially granting an attacker broad access to all connected SPs. Common threats include:
- Token forging and replay attacks: An attacker with an IdP’s signing key can forge valid tokens, while an intercepted token can be “replayed” to gain unauthorized access.
- Metadata tampering and certificate misuse: Attackers can modify federation metadata to redirect users to a malicious IdP or may exploit weak certificate lifecycle management to use stolen or expired signing certificates.
- Data privacy risks: Sharing user attributes across domains requires adherence to regulations like GDPR, which mandate principles such as data minimisation.
Mitigating these types of attacks requires a multi-layered approach combining technical controls and strong governance:
- Technical controls: All assertions must be digitally signed, and sensitive data within them should be encrypted. Communication channels must be secured with TLS. Short token lifetimes limit the window for replay attacks, and rigorous certificate management is essential.
- Governance and operational controls: The most critical defence is continuous monitoring and auditing. Organizations must have complete visibility into all federated authentication events and any changes to the trust framework.
Native logging tools in hybrid environments are fragmented, making it nearly impossible to correlate events across on-prem AD, Entra ID, and Microsoft 365 logs in real time. Effective security and compliance demand a single, immutable source of truth. Cayosoft Guardian provides this by delivering continuous change monitoring and a unified audit trail across the entire hybrid Microsoft environment. It provides real-time alerts on critical changes, such as modifications to federation settings or privilege escalations, that are often missed by SIEMs or native logs.
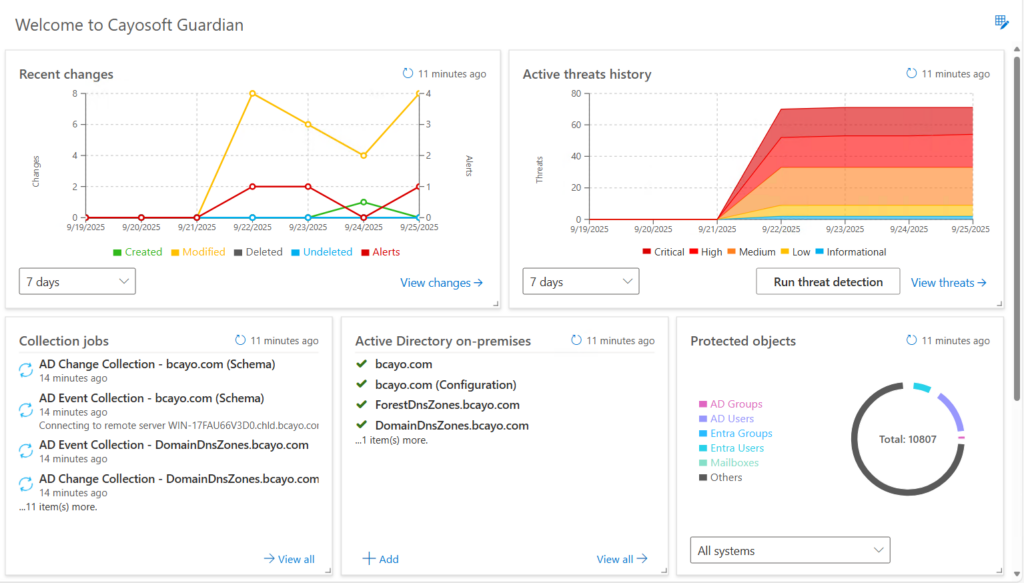
Cayosoft Guardian dashboard
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Conclusion
Achieving effective federated IAM is not a one-time project of simply implementing a protocol. It is a strategic discipline that requires a holistic approach built on three pillars: intelligent protocol adoption, deep integration into modern security architectures (such as zero trust), and, most importantly, continuous governance.
Executing these principles in complex hybrid environments is challenging, and specialized solutions like Cayosoft serve as a critical enabling layer. Cayosoft provides the automation, unified visibility, and granular control necessary to translate FIAM and zero-trust principles into a secure and manageable operational reality.
To see how automation can bridge common gaps and secure your federated ecosystem, sign up for a demo to see these principles in action.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content