An invisible config reset. No alert. No rollback. Here’s how Cayosoft Guardian helps it leaders regain visibility and stay resilient when Microsoft’s platform makes changes behind the scenes.
In June 2025, Petri.com confirmed a serious issue affecting organizations using Microsoft Intune. During a routine upgrade from the 23H2 to 24H2 Windows security baseline, custom configurations were silently deleted.
Not by accident. Not by an admin.
This was a backend process initiated by Microsoft and it wiped key security settings without warning.
The admin console still displayed a clean “Success” message. However, behind the scenes, the customizations for Defender, BitLocker, and Firewall were removed. Settings tied to the older baseline were removed entirely.
For most IT and security teams, there was no alert. No rollback. And no immediate indication that their hardened device posture had just been weakened.
What Happened?
According to Microsoft, this was tied to how Intune handles baseline upgrades. When a new baseline version is released, administrators are encouraged to create a new profile, rather than updating an existing one.
What is the problem caused by this Intube bug? When moving from 23H2 to 24H2, Intune’s backend deleted the custom policies linked to the older baseline. This process wasn’t transparent. It wasn’t logged in a way that admins could act on. And for many, it happened without them even realizing it.
While the root cause is technical, the consequence is operational and strategic: critical security settings disappeared, silently, in production.
Microsoft’s Native Capabilities: Helpful, but Limited
To Microsoft’s credit, Intune includes some native tools meant to support configuration tracking and baseline upgrades:
- Policy versioning (you must create a new profile for new baseline versions)
- Legacy policy visibility (read-only view of deprecated baselines)
- Audit logs (some user-driven events are captured)
- Reporting dashboards (focus on compliance, not config change)
But these tools are limited when it comes to real-world change detection, especially when changes aren’t initiated by your team.
They don’t alert you to baseline-linked settings being deleted.
They don’t show you what specifically changed.
They don’t offer meaningful before-and-after context.
And they don’t give you the ability to act before the impact spreads across your environment.
In short, they weren’t built for resilience; they were built for administration.
Cayosoft Guardian: Built for Resilience
This is where Cayosoft Guardian becomes essential.
Cayosoft doesn’t try to replace Microsoft tools; it extends them, giving IT and security teams the one thing they lacked during this incident: visibility.
Here’s how Cayosoft Guardian helps organizations detect and respond to risks like this:
Change Detection That Goes Beyond Logs
Guardian monitors the actual state of your security configuration, not just policy assignments or log entries. When a change occurs, even if it’s initiated by Microsoft, Cayosoft compares the previous known-good state to the current one and flags the delta immediately.
Alerting on Microsoft-Initiated Changes
Most tools won’t flag these backend-initiated changes because they weren’t driven by user action. Cayosoft treats any drift in expected configuration as critical whether it was caused by a user, a policy push, or a platform update.
Before-and-After Snapshots
When something changes, Cayosoft shows you exactly what was there before and what replaced it. This clarity enables you to investigate quickly, communicate effectively with stakeholders, and act decisively, even if you can’t directly reverse the change.
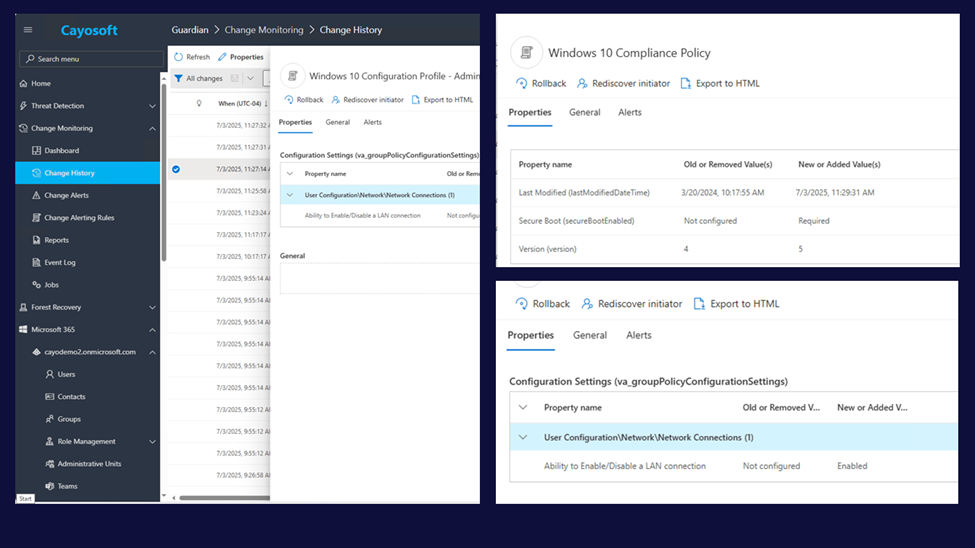
Full Audit Trail
Whether it’s for internal post-mortem, leadership briefings, or regulatory review, Cayosoft provides a complete historical record of what changed, when, and how (who), including platform-driven actions Microsoft doesn’t expose.
Resilience Means Seeing What Microsoft Doesn’t Tell You
The most dangerous changes in your environment aren’t always the ones an attacker makes sometimes, they’re the changes your own platform introduces quietly, automatically, and without transparency.
That’s why resilience starts with visibility.
This Intune baseline issue wasn’t isolated. It was a reminder that trusted systems can introduce risk, and most organizations lack the tooling to catch it in time.
Cayosoft closes that gap.
We help hybrid enterprises monitor critical systems like Active Directory, Entra ID M365, and Intune and catch changes before they become outages, exposures, or audit failures.
You can’t stop Microsoft from updating baselines. But with Cayosoft, you can detect the fallout and move quickly to recover.
Strengthen Your Hybrid Active Directory Security with Cayosoft Guardian™
Monitor and protect your Active Directory with real-time change tracking and instant recovery. Enhance your password policies and safeguard privileged accounts effectively.
Final Thought
If you didn’t see this Intune baseline issue coming, you’re not alone.
But if it happens again — and it will — Cayosoft makes sure you’re not the last to know.
Because in a world where your config management platform can become a risk vector, you need more than compliance.
You need resilience.
📚 Read the full incident coverage at Petri.com
🔐 Learn more about Cayosoft Guardian
FAQs
The Intune Baseline rollback bug refers to a backend issue where custom security settings—such as Defender, BitLocker, and Firewall policies—were silently deleted during an upgrade from the 23H2 to 24H2 Windows security baseline in Intune. These deletions occurred without admin action or alerts, making the bug particularly dangerous for enterprise environments.
Detecting the impact of the Intune Baseline rollback bug is challenging because Microsoft’s native tools don’t log these backend-driven changes. IT teams need solutions like Cayosoft Guardian, which tracks real-time configuration changes and alerts on any drift from the known-good state, even if the change originates from Microsoft’s own platform.
Yes, Microsoft has acknowledged that this behavior was tied to how Intune handles baseline upgrades. However, they did not initially warn customers, and their tools did not provide clear visibility or rollback options. The Intune Baseline rollback bug underscores the risks of relying solely on native tools for critical configuration management.
Native Intune tools are not designed to detect backend-initiated deletions like those caused by the Intune Baseline rollback bug. While they offer some visibility into policy versions and deprecated baselines, they fall short in real-world scenarios where administrators need proactive alerts and detailed before-and-after comparisons.
Ignoring the Intune Baseline rollback bug means accepting a significant blind spot in your security posture. When critical settings vanish without notice, systems can become vulnerable to threats, compliance violations, or operational failures—often without anyone realizing until it’s too late.