Home » Best Practices for Robust Identity and Access Governance » Practical Steps to Establish an Identity Governance Framework
Practical Steps to Establish an Identity Governance Framework
Learn the key components and principles of an effective identity governance framework and how to align them with risk and compliance needs.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Next Chapter >
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
An identity governance framework provides the structure needed to manage digital identities and control access within an organization. It describes who should have proper authorization for systems and defines the steps that need to be taken to maintain identity compliance over time.
Proper identity and governance administration helps organizations guide policy decisions, set accountability, and link identity practices to security goals. As organizations use more hybrid and cloud systems, both frameworks and solutions help them stay consistent, reduce risk, and meet regulatory requirements.
This article explains the key ideas, principles, standards, and practices that make up an identity governance framework, with clear descriptions of each main component and how it fits into overall identity administration.
Summary of key components of an identity governance framework
Before you dive into modeling your own governance framework, make sure you understand what makes an identity governance framework effective for your organization.
| Component | Purpose |
|---|---|
| Governance principles and policies | Establishes guiding principles and policies to enforce consistent identity rules. |
| Risk and compliance alignment | Integrates identity governance with organizational risk and compliance needs. |
| Identity lifecycle standards | Defines structured processes for onboarding, role changes, and offboarding. |
| Role and access modeling | Creates roles, entitlements, and models to enforce least privilege. |
| Oversight and accountability | Assigns ownership, performs audits, and ensures transparency in governance. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Governance principles and policies
Any serious identity governance effort begins with a set of principles that everyone can understand and a set of policies that are clear enough to enforce. Most organizations anchor these around the principle of least privilege and policy‑driven access control.
Least privilege is straightforward—at least in theory. Users, services, and applications should receive only the access they genuinely need to perform their tasks. In reality, though, many organizations end up with the opposite situation, where people accumulate permissions as they change roles, projects, or managers, and little is ever removed.
Policy‑driven access enforcement is the practical counterpart of least privilege access. Rather than relying on individual judgment each time someone asks for access, the organization defines policies. Examples might include “finance analysts can access the general ledger system with read‑write permissions, subject to manager and system‑owner approval” or “all contractors must use multi‑factor authentication (MFA) when connecting to internal systems.” Those policies are then implemented in tools (identity governance platforms, directories, cloud IAM, etc.) so that consistent decisions are made automatically wherever possible.
A common weakness in many environments is that policies exist in scattered documents or people’s heads. A stronger governance framework deliberately stores all identity‑related policies in a central, version‑controlled repository. Security teams, HR, IT operations, application owners, and auditors all refer to this same source of truth. This arrangement both reduces confusion and makes audits more predictable: Instead of explaining ad hoc practices, you can simply show that your implemented controls match your documented policies.
Once those policies are in place, the next question is whether they are actually aligned with the organization’s risk profile and regulatory obligations.
Risk and compliance alignment
Identity is one of the main ways attackers gain a foothold. Mismanaged access, especially in the areas of privileged accounts and sensitive applications, turns into real incidents and real findings in audits. An identity governance framework that lives in isolation, disconnected from the formal risk and compliance function, will always be incomplete.
The starting point is to understand where identity‑related risk is concentrated. In most organizations, a relatively small set of systems and accounts carries the majority of the risk. Once these are identified, identity governance can be designed as a set of controls that address concrete risk scenarios. For example, if one risk scenario is that a dormant privileged account might be exploited, the framework should describe which controls mitigate it. Those might include:
- Automatic disabling of accounts shortly after HR marks someone as terminated
- Regular reporting on inactive admin accounts
- Periodic access reviews focused on privileged users
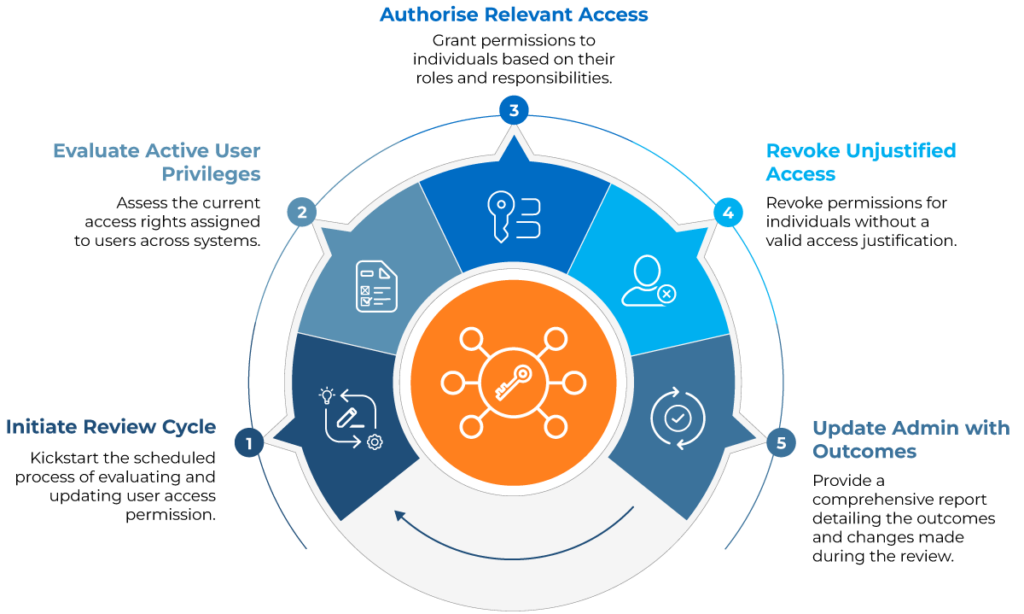
An example image of a user’s access review cycle (source)
For risks like a single user both creating and paying vendors in the financial system, the framework should specify segregation‑of‑duties rules that prevent the user from holding both entitlements unless there is an approved, time‑bound exception.
The regulatory landscape is, as a result, shifting toward stricter requirements for identity accountability. Standards such as ISO/IEC 27001, NIST SP 800‑53, and NIST SP 800‑63 assume that organizations can show, at any point, who has access to what, who approved it, and when those entitlements changed. They also expect evidence of regular access reviews and of controls regarding privileged accounts and sensitive data. If these expectations are not built directly into the everyday processes of identity governance, teams end up scrambling during audits, trying to stitch together an incomplete picture from log files and aging spreadsheets.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Identity lifecycle standards
Every identity passes through a series of stages: People join the organization, change roles or departments, take leaves of absence, rejoin the organization, and eventually leave. The same is true for non‑human identities, such as service accounts and automated integrations, which may be created for specific projects and later be forgotten. Most identity‑related incidents and audit findings trace back, in one way or another, to failures in these lifecycle transitions.
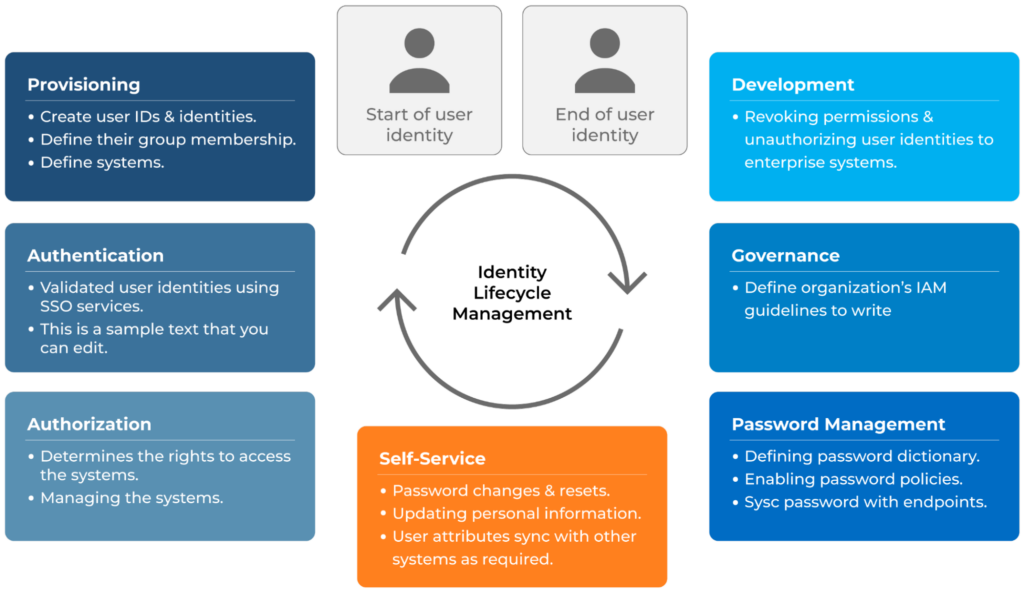
A typical identity lifecycle process diagram that most organizations follow (source)
Because most security and audit failures trace back to unresolved lifecycle changes, the joiner-mover-leaver model (JML) is the usual way to structure and govern these transitions.
- For joiners, the framework should specify which system acts as the authoritative source for new identities: typically HR for employees, a vendor management system for contractors, and an identity provider or directory for some categories of external users. When a new record appears in that system, the identity governance processes are triggered. An account is created in the directory or identity provider, baseline access (such as to email and collaboration tools) is granted, and role‑specific access is assigned based on job function, department, and location. Done well, this ensures that new employees arrive on the first day with the right access in place and without a flurry of manual tickets.
- Movers are more subtle but often more dangerous. When someone changes departments, locations, or roles, new access must be granted to support the new responsibilities, and old access must be reviewed and removed where no longer needed. Many organizations are good at the first part and poor at the second, which leads to cumulative privilege creep. A mature identity governance framework will describe which kinds of changes in HR or directory attributes should trigger a mover workflow, and it will specify that entitlements not justified by the new role must either be removed or explicitly renewed as an exception.
- Leavers require particularly prompt action. The framework should make it clear that HR termination events are the authoritative signal to begin deprovisioning. Accounts should be locked or disabled quickly (especially high‑risk ones), and access to applications and data should be removed in an orderly fashion. For certain roles, such as system administrators or senior executives, termination may also need to trigger additional monitoring and review to detect suspicious activity related to the departure.
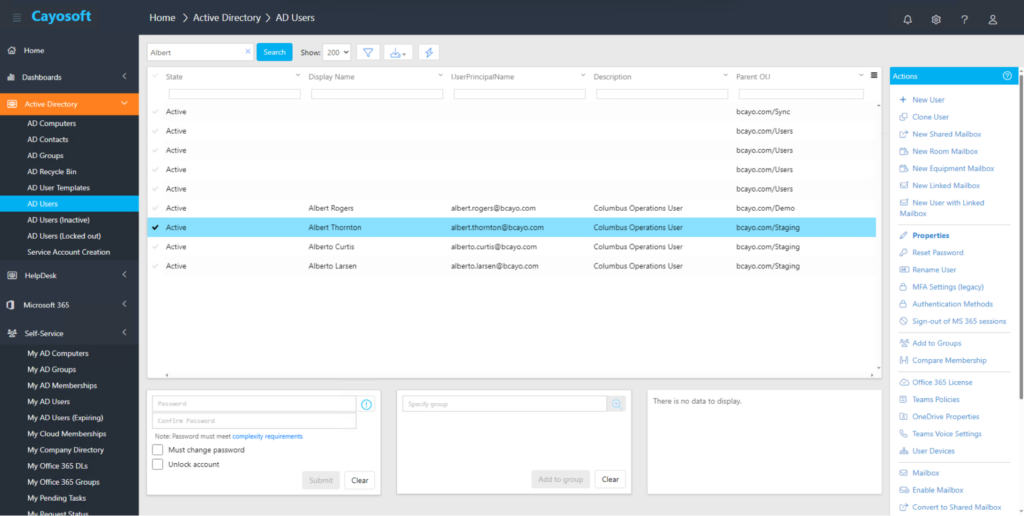
An example solution used for identity and governance administration (source)
A robust framework also explicitly addresses edge cases. For example, an employee returning from a brief leave of absence might have his or her previous access restored automatically, whereas a rehire after a long gap could be treated as a fresh joiner, with access reassigned according to current policies.
Once lifecycle events determine when access should change, the framework should follow automated access modeling to decide what that access should be at each point.
Role and access modeling
Role and access modeling sets how entitlements are structured, assigned, and managed across the organization. This part of the governance framework turns business functions into standard access models that support least privilege and reduce unnecessary differences. Well-designed roles make sure that access is assigned consistently, lower the risk of privilege creep, and make governance easier across large identity systems.
Role hierarchies help organizations match job functions to clear access needs. These hierarchies usually include basic access for general users, special access for certain teams, and higher access for administrators. When roles are based on business needs instead of individual requests, entitlement sprawl goes down, and access provisioning becomes faster and more reliable. In Identity Governance and Administration (IGA) practices, role-based access control (RBAC) is key to standardizing access.
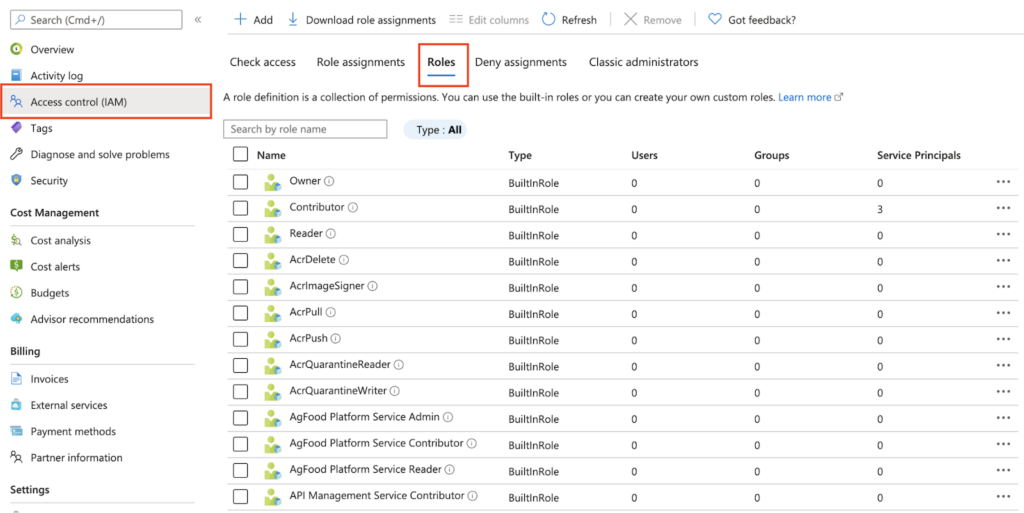
Example Azure IAM Roles for role-based access control. (source)
No matter how careful the initial design, roles change over time. If roles are never revisited, they slowly drift away from their original intent and pick up extra permissions along the way. To counter this, a mature framework includes a role recertification process. On a regular schedule—perhaps annually for standard roles and more frequently for high‑risk ones—the designated role owner reviews both the definition of the role and the list of people assigned to it. That individual confirms that the entitlements are still appropriate and that each assignee still needs the role. If not, the role is adjusted, and assignments are pruned.
Oversight and accountability
In most organizations, each critical application should have a clearly identified system owner, usually on the business side, who is accountable for deciding who should have access and in what capacity. Similarly, roles should have named owners who approve changes to the role definitions and decide who participates in periodic recertification. Security and risk teams provide oversight, setting minimum standards and reviewing how well identity controls are functioning, but they do not necessarily own every access decision.
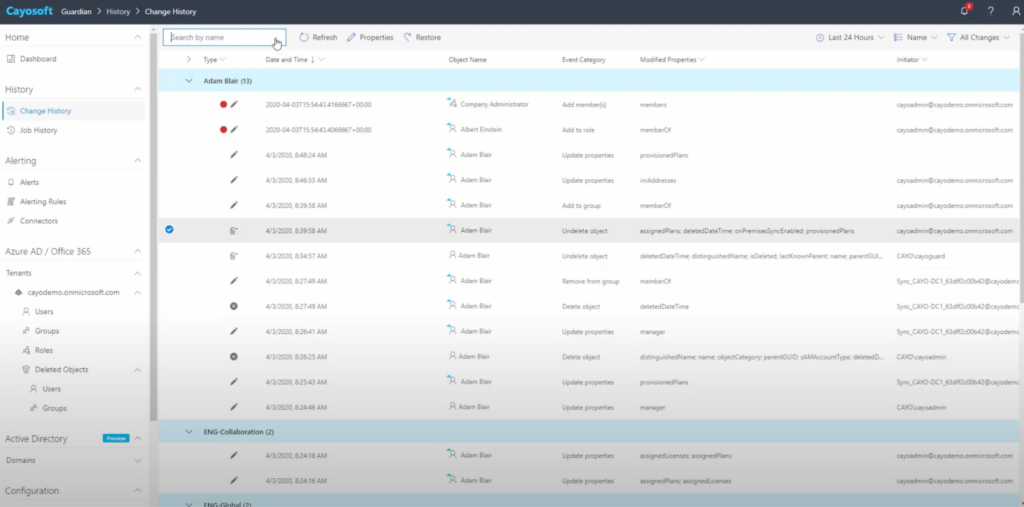
Example of Cayosoft Guardian’s logging and auditing system (source)
A simple way to make responsibilities explicit is to document them using a RACI‑style model for key activities:
- Who is responsible for granting access to a high‑risk application
- Who is accountable if something goes wrong
- Who must be consulted when policies change
- Who should be informed of major incidents or findings
Visibility is important, too. Dashboards provide visual information that makes it easier to spot irregularities in identity usage trends. They enable the quick identification of unusual authorization changes, access from unexpected locations, and irregular login times.
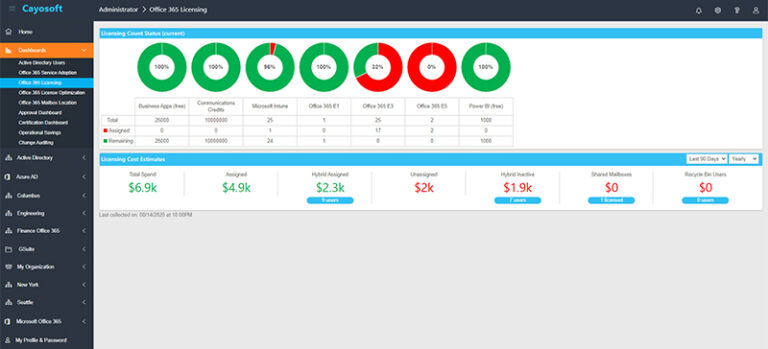
Example of Cayosoft Administrator’s dashboarding system (source)
The framework should also help identify which metrics matter. These might include the percentage of new joiners provisioned by their first day, the average time taken to deprovision leavers in critical systems, the number of orphaned accounts discovered in each review cycle, or the completion rates of scheduled access reviews. Over time, such metrics make it possible to judge whether identity governance is becoming more effective or simply more complicated.
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Alignment with well-known standards
Aligning an organization’s identity governance framework with global standards improves its overall governance stance. These standards give clear guidance on how identity controls should work, how to manage risks, and how to enforce security and accountability. There are many well-known standards being used by organizations; here are a few of them.
ISO/IEC 27001
This is the best known standard for information security management systems (ISMS), defining the requirements that an ISMS must meet. The standard provides companies of any size and from all sectors of activity with guidance for establishing, implementing, maintaining and continually improving an information security management system.
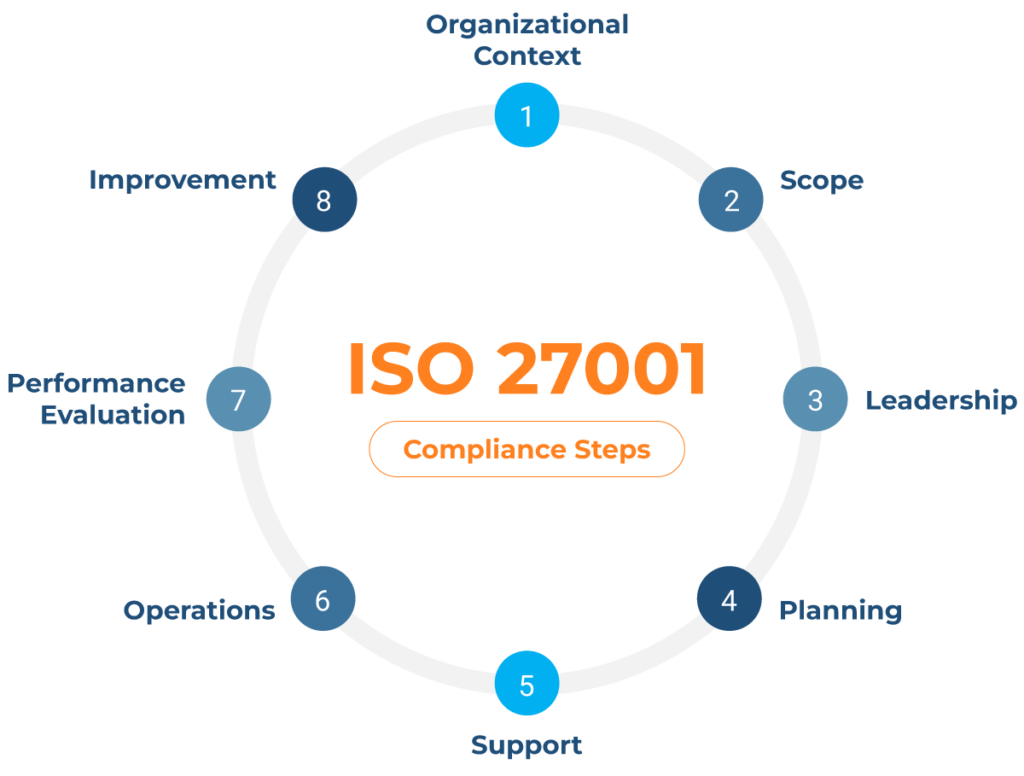
ISO 27001 framework components (source)
Conformity with ISO/IEC 27001 means that an organization has put in place a system to manage risks related to the security of data owned or handled by the company and that this system follows all the best practices and principles outlined by the framework. This standardization also makes audits more predictable and promotes consistent expectations across departments and regions.
ISO/IEC 27014
The new version of ISO/IEC 27014 is a key companion to ISO/IEC 27001, fundamental to the information security governance activities embedded in the scope of an ISMS and in the context of overall organizational governance. The standard has recently been updated to improve clarity and structure, and it features new information. It has been aligned with ISO/IEC 27001 requirements while also remaining relevant to the broader scope of governance requirements of an organization.
NIST Cybersecurity Framework (CSF)
CSF provides guidance to industry, government agencies, and other organizations that focuses on managing cybersecurity risks. It offers a taxonomy of high-level cybersecurity outcomes that can be used by any organization—regardless of its size, sector, or maturity—to better understand, assess, prioritize, and communicate its cybersecurity efforts. The CSF does not prescribe how outcomes should be achieved. Rather, it links to online resources that provide additional guidance on practices and controls that could be used to achieve those outcomes.
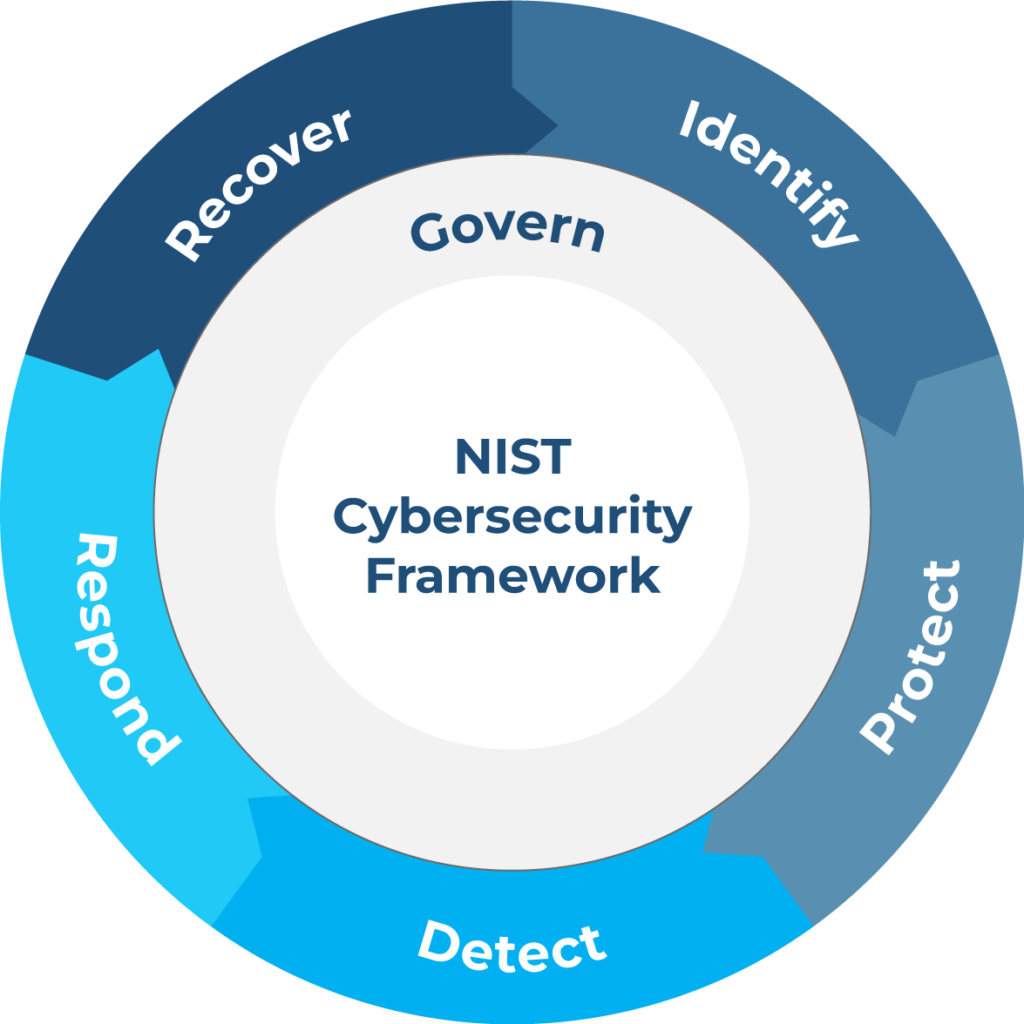
NIST CSF new version 2.0 framework model (source)
Control Objectives for Information and Related Technologies (COBIT)
COBIT provides a comprehensive and integrated enterprise framework that covers various aspects of IT governance and management. The COBIT framework establishes a common language for information technology professionals, compliance auditors, and business executives. It helps organizations define clear management objectives and establish a structured approach to achieve them. By implementing COBIT, organizations can effectively manage risks, ensure compliance with regulatory requirements, and optimize IT resources.
Comparison of standards
Many organizations choose one standard as their primary reference—perhaps ISO 27001 for its certification pathway, or NIST CSF for its risk orientation—and then map their identity governance controls to the relevant sections. Later, they may cross‑map those same controls to meet industry‑specific regulations or customer requirements. The mapping itself can reveal gaps in the identity governance framework.
To understand how the standards fare over others, the table below lists their primary focus area and relevance to identity governance.
| Standard / Framework | Primary Focus Area | Relevance to Identity Governance | How It Supports an Identity Governance Framework |
|---|---|---|---|
| ISO/IEC 27001 | Security controls and management systems | Defines user access controls, identity policies, and lifecycle processes | Helps standardize identity requirements and ensures policy-driven governance |
| ISO/IEC 27014 | Information security governance | Aligns identity governance with strategic security objectives | Reinforces decision-making structures, risk oversight, and policy consistency |
| NIST | Risk-based cybersecurity posture | Integrates identity into risk management processes | Provides structure for risk-informed access reviews, authentication controls, and privilege monitoring |
| COBIT | IT governance and accountability | Emphasizes ownership, metrics, and governance performance | Supports governance boards, defined responsibilities, and transparent decision-making |
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Final thoughts
A robust identity governance framework often comes down to an organization properly standardizing its processes with continuous refinement over time. While the technical capabilities of IGA solutions are important, the quality of your implementation through frameworks and mapped standards can be the major differentiators in improving efficiency and maintaining compliance over time.
In practice, executing a framework at scale can be challenging without the right tooling. If you are evaluating how to operationalize your policies, it is worth seeing how far you can get with automation rather than custom scripts and manual spreadsheets.
Cayosoft focuses on automating identity, group, and access management across complex Microsoft‑centric and hybrid environments. Book a demo to learn more about how Cayosoft supports identity governance in hybrid Microsoft environments.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Explore More Chapters
Next Chapter >