Home » Implementing Zero Trust Security with Microsoft Entra » Deploying Entra PIM Effectively: Strategies for Enhanced Security
Deploying Entra PIM Effectively: Strategies for Enhanced Security
Learn practical strategies for deploying and managing Microsoft Entra PIM to reduce vulnerabilities and prevent data breaches and compliance violations.
Explore the chapters:
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Unmanaged privileged access makes organizations more vulnerable to both external threats and insider misuse. The concept of least privilege, which dictates that users should only have the access necessary to perform their duties, is undermined leading to data breaches, system disruptions, and compliance violations.
Microsoft Entra PIM (Privileged Identity Management) is specifically designed to address the challenges of managing privileged access in the modern enterprise. As a core service within the Microsoft Entra ID Governance suite, it enables organizations to manage, control, and monitor access to critical resources across their Microsoft ecosystem.
This article discusses practical strategies and insights for effectively deploying and managing Microsoft Entra PIM in your organization.
Summary of key Microsoft Entra PIM best practices
This table outlines six recommended practices to keep in mind when implementing Microsoft Entra Privileged Identity Management (PIM):
| Best Practices | Description |
|---|---|
| Reduce the number of permanent admins | Minimize the reliance on standing privileged access by adopting JIT and other PIM features. |
| Enable Just-In-Time (JIT) access | Grant privileged access only when needed and for a limited duration, instead of permanent assignments. |
| Require multi-factor authentication (MFA) | Require MFA for all privileged role activations to enhance security and verify user identity. |
| Use approval workflows | Implement approval processes for privileged role activations to ensure oversight and prevent unauthorized access. |
| Regularly review access assignments | Conduct periodic access reviews to ensure privileged access is still necessary and appropriately assigned. |
| Monitor and audit privileged activity | Monitor and audit PIM events to detect and respond to suspicious or unauthorized activities. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Six best practices when implementing Microsoft Entra PIM
#1 Reduce the number of permanent admins
Having numerous permanent administrator accounts poses substantial security risks. These accounts are attractive targets, as they can grant extensive and immediate control over an organization’s resources. Additionally, even authorized users with permanent privileged access can unintentionally compromise sensitive resources.
To effectively reduce the number of permanent administrators, undertake a thorough review of the current access assignments.
Inventory existing permanent admin roles
Admins can use the Microsoft Entra admin center or solutions like Cayosoft Administrator to identify accounts directly assigned permanent administrative roles, including both Microsoft Entra and Azure resource roles. Complementing these methods, admins can also use the Microsoft Graph API to enumerate various PIM configurations, including listing requests for privileged access, such as activations, assignments, renewals, and extensions, by querying the unifiedRoleAssignmentScheduleRequest resource.
Map administrative responsibilities
For each identified permanent admin account, carefully analyze the user’s responsibilities and tasks requiring elevated privileges.
Leverage granular roles
Instead of assigning broad administrator roles like Global Administrator, explore using more specific, less privileged roles that align precisely with users’ responsibilities. Microsoft Entra ID offers a wide range of built-in roles, and organizations can also define custom roles where necessary.
#2 Enable Just-In-Time (JIT) access.
Microsoft Entra PIM utilizes Just-In-Time (JIT) access to grant users temporary, elevated permissions only when necessary. Instead of permanent active role assignments, users are assigned roles as “eligible”. This allows them to activate admin roles for a specified period when necessary to perform privileged tasks. Privileged access is automatically revoked once the activation period ends.
To configure JIT access in Microsoft Entra PIM, you primarily work with role assignments:
- Navigate to Microsoft Entra roles and select ‘Assignments’, then ‘Add Assignment‘.
- Choose the desired administrative role and the users, groups, service principals, or managed identities to whom it should be assigned.
- Select ‘Eligible’ as the Assignment Type.
- Justify the assignment.
- Click ‘Assign’
Administrators can further refine JIT access by configuring the role settings. These policies allow you to:
- Set the maximum activation duration for eligible roles. Eligibility can be permanent (always eligible to activate) or time-bound (eligible to activate only within a specific start and end date).
- Multi-factor authentication (MFA) is required on activation.
- Require approval to activate privileged roles.
- Require users to justify role activation.
- Configure notifications to be sent when privileged roles are activated.
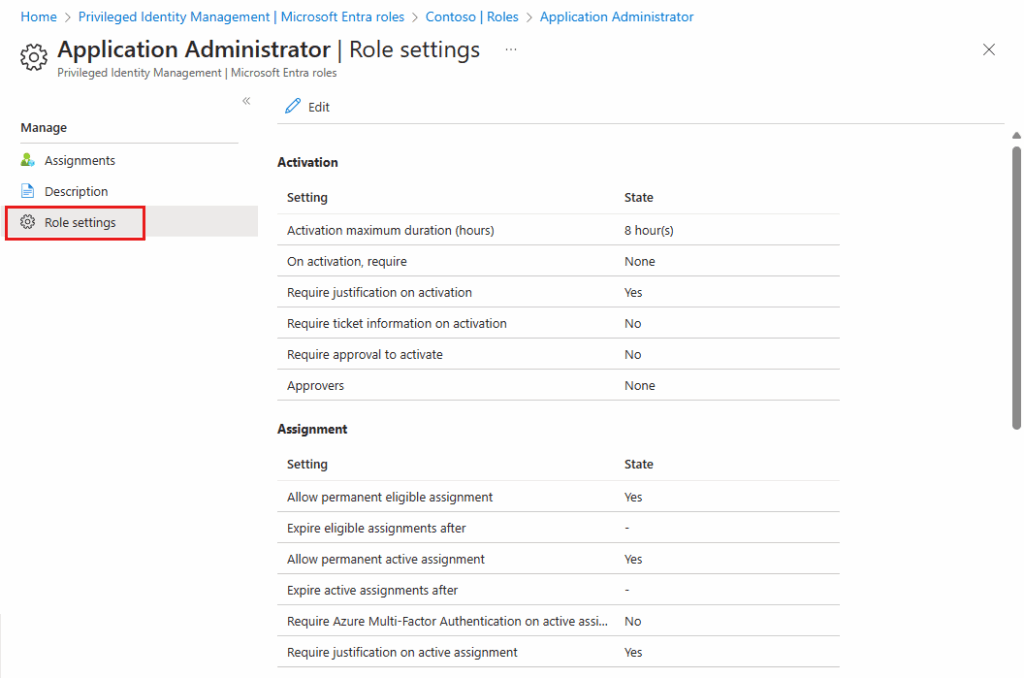
Configuring role settings in PIM (source)
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
#3 Require multi-factor authentication
MFA mitigates the risk of privileged accounts getting compromised by requiring users to provide at least two different verification forms before granting access or activating a privileged role.
MFA acts as a critical control to verify the user’s identity at the point of access or privilege elevation for privileged roles. It makes it more difficult for unauthorized actors to gain access to privileged accounts, even if they have obtained a password through techniques like phishing or password spraying.
You can enforce MFA for privileged role activations in Microsoft Entra PIM as follows.
PIM role settings
Administrators can require MFA for activation within the role settings for a specific role. Users who attempt to activate an eligible role with such configured settings will be prompted to perform MFA if they haven’t already done so within their current session.
Conditional Access Authentication Context
It’s important to note that by default, privileged roles in PIM often enforce Azure MFA on role activation. However, this might not always trigger a fresh MFA prompt if the user’s session already satisfies the requirement. Therefore, relying solely on the default policy might provide a false sense of security.
Conditional Access policies in Microsoft Entra PIM allow you to enforce different or additional MFA methods, specifically when activating a PIM role, even if the user has already performed MFA to start their session.
#4 Use approval workflow
Approval workflows are helpful in managing privileged access by adding a layer of oversight and verification before granting sensitive permissions. Organizations can ensure designated approvers explicitly authorize privileged role activation. Approval workflows also improve accountability by recording who approved the access and the justification for the request, crucial for audits and security incident investigations.
To configure approval workflows in Microsoft Entra PIM, you must modify the PIM policy settings for a specific role.
- Navigate to Microsoft Entra PIM.
- Select the role you want to manage and go to ‘Role settings’.
- Edit the settings for the relevant assignment type (e.g., Member or Owner).
- Under the Activation tab, locate the option related to approval requirements.
- Enable the option to require approval to activate the privileged role.
- Specify the designated approvers (users or groups).
- Save the PIM role settings.
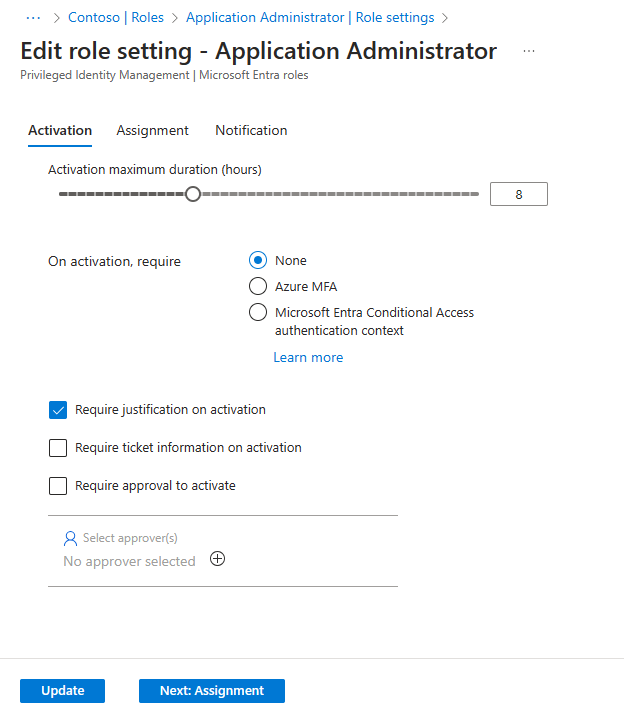
Configuring role settings to enable approval workflow (source)
You can often specify multiple approvers or groups of approvers. When a role request is awaiting approval, an email notification containing a direct link to the request is sent to the approvers. They can either approve or deny the request. The first approver resolves the request to respond, and all approvers are notified of the response to the approval request. Once an approved user becomes active in their role, Microsoft Entra PIM automatically notifies Global Administrators and Privileged Role Administrators.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
#5 Regularly review access assignments
Periodic reviews of privileged accounts ensure that the privileged access granted is still necessary and appropriately assigned. Over time, users’ roles and responsibilities may change and projects may conclude. Without regular reviews, privileged accounts accumulate unnecessary permissions, increasing the attack surface and potential for accidental or malicious misuse. Access reviews contribute to the principle of least privilege by identifying and removing excessive permissions. They also enhance accountability and help organizations meet regulatory compliance requirements by providing an auditable trail of who has access to what and why.
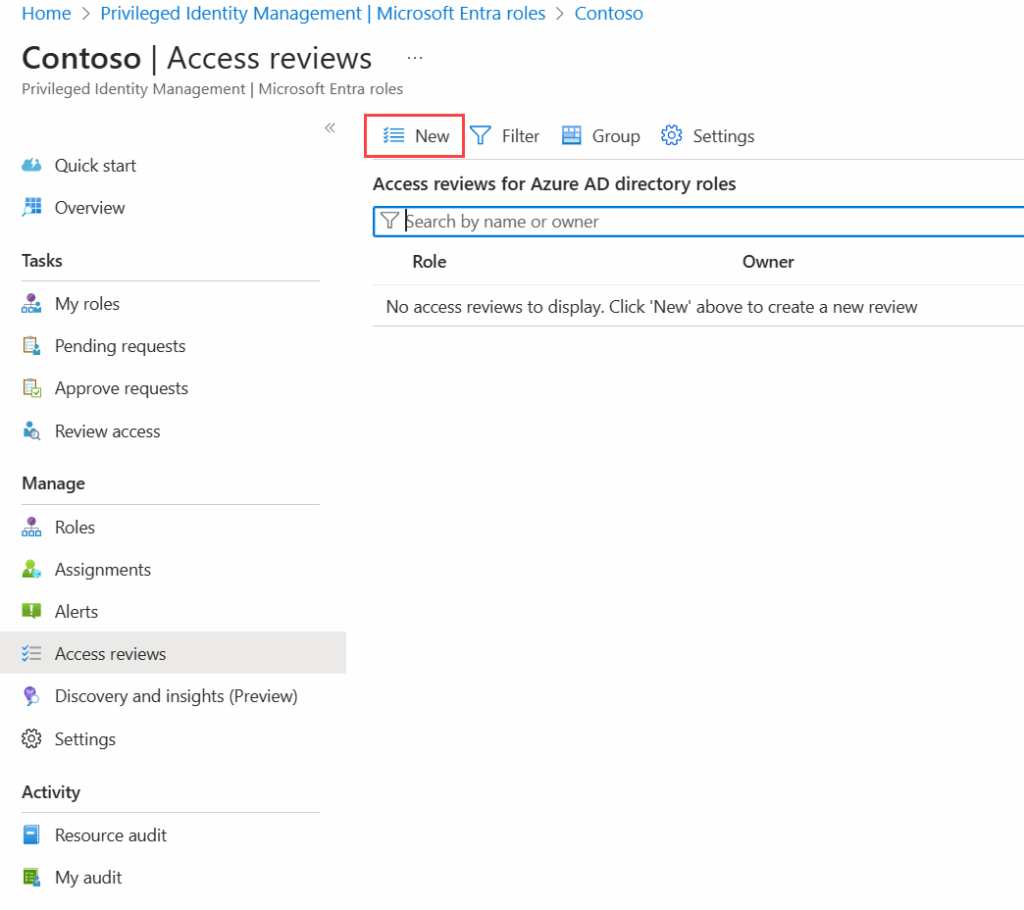
Microsoft PIM Access Review (source)
Microsoft Entra PIM automates reviewing privileged accounts and provides features to handle tasks like creating and managing access reviews for Microsoft Entra and Azure resource roles. An admin can:
- Define the scope of the review, such as specific roles or groups of users.
- Set the frequency of reviews (e.g., monthly, quarterly, annually).
- Designate reviewers, who can be the account owners, managers, or delegated administrators.
- Receive recommendations based on user activity or inactivity to aid in the review process.
- Automate actions based on the review outcomes, such as removing access for users who no longer need it.
- Generate audit logs of the review process and decisions.
Cayosoft offers solutions that simplify access review processes by providing a unified platform for managing and securing hybrid environments. Cayosoft Administrator automates group membership management and dynamically updates it based on rules. It ensures that users have the proper access privileges at all times. It also reduces the number of individuals requiring privileged access through granular delegation, meaning there are fewer highly privileged accounts to review in the first place.
Cayosoft Guardian‘s continuous change monitoring and unified change history aid in access reviews by providing a clear audit trail of changes to permissions and group memberships. The trail allows reviewers to identify any anomalies or inappropriate access assignments quickly.
#6 Monitor and audit privileged activity
Monitoring and auditing privileged activity provides a record of actions taken by users with elevated permissions. Organizations can identify suspicious or unauthorized actions that could indicate a security breach or insider threat. Audit logs also provide valuable insights into who accessed what resources, when, and from where, enabling security teams to quickly detect anomalies, investigate potential compromises, and respond effectively to mitigate damage.
Microsoft Entra PIM provides an audit history feature that allows admins to view all role assignments and activations for all privileged roles within the past 30 days. This audit history contains records of privileged role activations, deactivations, tasks, and other PIM-related activities. PIM also sends notifications when privileged roles are activated, which can serve as immediate alerts and a basic form of monitoring. These notifications often include details such as the justification provided and who activated the role.
Cayosoft Guardian offers continuous change monitoring and real-time alerts for AD, Entra ID, and Office 365. It provides a unified change history that records up-to-the-minute changes across integrated Microsoft services, including on-premises Active Directory, hybrid Active Directory, Azure AD, and Office 365. This unified history allows admins to view and track changes made in and between Microsoft systems, which is difficult with native event logs or legacy auditing tools. Built-in or custom queries can show “who, what, when, and where” details.
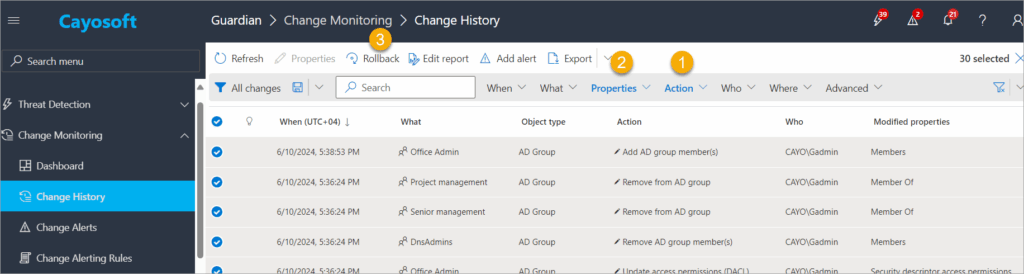
Cayosoft Guardian change monitoring (source)
Furthermore, it can detect threats by automatically identifying and reversing malicious changes. Cayosoft Guardian’s continuous monitoring and alerting proactively notify administrators of significant changes before they escalate into problems, helping to stop breaches and mistakes that could lead to outages or fines. The platform provides a more comprehensive and unified approach to auditing and monitoring than relying solely on native logs.
Learn why U.S. State’s Department of Information Technology (DOIT) chose Cayosoft
Conclusion
Microsoft Entra PIM is a critical component in the defense of modern IT environments. It directly addresses the significant risks posed by privileged accounts – often the primary targets of sophisticated cyberattacks – by fundamentally changing how administrative access is granted and managed.
It is worth noting that effectively implementing PIM also requires a strategic investment in planning, configuration, and ongoing operational effort, beyond simply leveraging Microsoft Entra ID P2 or Governance licenses. The return on this investment significantly reduces the risk of catastrophic breaches, improves compliance posture, and enhances control over critical assets in the long run.
You’re strongly encouraged to enhance your Entra PIM setup as an administrator! Don’t settle for basic configurations; implement these best practices to elevate your privileged access management and fortify your organization’s security posture.
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content