Home » Best Practices for Robust Identity and Access Governance
Best Practices for Robust Identity and Access Governance
Learn about the key concepts of identity and access governance, including IAM vs. IAG, identity lifecycle management, authentication and authorization, and governance and compliance.
Explore the chapters:
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
- Chapter
- Identity and Access Governance
- Privileged Access Management Best Practices
- Identity Lifecycle Management
- Identity Governance and Administration
- Identity Governance Solutions
- Automated User Provisioning
- Access Governance Tools
- Federated Identity Access Management
- Vendor Privileged Access Management
- Identity Governance Framework
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
The last few years have seen the traditional corporate perimeter largely disappear. Data, applications, and services now span on-premises data centers, public clouds, and SaaS platforms. Users are also no longer just employees at their desks; they are remote workers, international contractors, and even APIs, all requiring access to critical resources from anywhere.
One thing that has remained constant in this new domain is identity. Managing identities was simpler when everything resided within the organization’s four walls, but that changed as organizations transitioned to hybrid environments. Some users hold multiple identities across multiple domains, and without a unified governance strategy, it becomes nearly impossible to maintain a clear, consistent, and secure view of who has access to what across the entire digital estate.
Identity and access governance is a strategic framework of policies, processes, and technologies that answer the fundamental questions of security and compliance:
- Who has access to what?
- Is that access appropriate for their role?
- How did they get it?
- What are they doing with it?
- Who is attesting that this access remains necessary?
This article explores key concepts of identity and access governance, providing a clear, structured understanding of its core pillars and going beyond the usual buzzwords.
Summary of foundational identity and access governance concepts
This table provides a concise overview of the key concepts explored in this article.
| Key concept | Why it matters |
|---|---|
| IAM vs. IAG | Understanding the difference between simply managing identities and access (IAM) and the bigger picture of governing how that access is used (IAG) is the first step toward truly comprehensive security and compliance. |
| Identity lifecycle management | Automating the entire journey of an identity—from when someone joins to when they leave—ensures that access is always secure, efficient, and appropriate throughout that entity’s time with an organization. |
| Authentication and authorization | Knowing who someone is (authentication) and what they’re allowed to do (authorization) are the core principles that protect all your digital interactions and keep sensitive data safe. |
| Access control (RBAC/ABAC) | Setting up permissions based on roles (like “manager”) or attributes (like “department” or “location”) allows you to grant precise, secure access to resources. |
| Governance and compliance | Making sure your identity and access practices follow all the rules—including both external regulations and internal policies—is absolutely critical for meeting legal obligations and maintaining trust. |
| Audit, reporting, and identity intelligence | Having clear logs, detailed reports, and deeper insights into all identity and access activities helps you spot security issues, prove your compliance, and constantly improve your security posture. |
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
IAM vs. IAG
Identity and access management (IAM) and identity and access governance (IAG) are related but distinct. They are best understood as two core components of a comprehensive Identity Governance and Administration (IGA) framework. The framework acts as a modern, integrated solution that combines IAM and IAG into a single, cohesive system. The purpose of IGA is to fundamentally bridge the gap between day-to-day administrative tasks and high-level governance requirements.
- Administration (The “A” in IGA): This is the operational side, handling the provisioning, workflows, and lifecycle events.
- Governance (The “G” in IGA): This is the oversight side, handling policy enforcement, access reviews, auditing, and reporting.
IAM covers the nuts and bolts of managing user identities, including authentication methods, account provisioning and de-provisioning, single sign-on, and enforcement of access controls. IAG, by contrast, provides a higher-level oversight and policy framework that ensures that those IAM processes operate securely and compliantly.
You can think of it this way. IAM is the locksmith and the security guard. It’s responsible for forging the keys (provisioning accounts), checking IDs at the door (authentication), and unlocking specific doors based on the key presented (authorization). It is the enforcement and operational layer.
IAG, on the other hand, is the building’s security policy office. It doesn’t forge the keys itself, but it writes the policies that determine who is allowed to have which keys, for how long, and under what conditions. It conducts audits to check that the locksmith is following the rules, reviews security camera footage to spot suspicious activity, and requires department heads to periodically rejustify why their team members still need access to certain secure floors. It is the oversight, policy, and compliance layer.
Concept | Identity and Access Management (IAM) | Identity and Access Governance (IAG) |
Primary Focus | Operational execution and enforcement. | Oversight, policy, and compliance. |
Role in Identity Governance and Administration (IGA) | The Administration component (“A”). | The Governance component (“G”). |
Core Activities | Provisioning, de-provisioning, authentication, single sign-on, and enforcement of access controls. | Policy and role management, access reviews/attestation, auditing, and compliance reporting. |
Analogy | The locksmith and security guard (forging keys, checking IDs). | The security policy officer (writing rules, conducting audits). |
Goal | To manage who can access what and how. | To ensure that IAM processes operate securely and comply with regulations. |
Within the comprehensive IGA strategy, the Governance (IAG) module builds on the foundation of the Administration (IAM) to provide strategic oversight, risk management, and compliance. It ensures that the operational activities of IAM align with business policies and regulatory requirements. Here are some of the key functions of IAG:
- Policy and role management involves creating and managing roles that bundle specific access entitlements.
- Access requests and approvals involve providing a structured workflow for users to request new access and a formal approval process from designated personnel.
- Access certification and attestation entail the formal, periodic process of reviewing and revalidating user access rights to ensure that they are still necessary and appropriate.
- Auditing and reporting include logging all identity-related events and generating comprehensive reports to demonstrate compliance and identify security risks.
A true IGA solution ensures that the administration tools automatically enforce the rules set by governance. This is the framework where Cayosoft Administrator operates.
Identity lifecycle management
Every identity within an organization—whether it belongs to a full-time employee or a non-human service account—has a lifecycle. Identity lifecycle management (ILM) is the process of managing this entire journey from creation to eventual deletion.
When a new employee joins an organization, the ILM process kicks in immediately. The goal is to provide the employee with the necessary access to be productive from day one but without granting excessive permissions.
Employees rarely remain in the same role for their entire careers: They get promoted, change departments, or move to new projects. These transitions represent some of the most common points where security vulnerabilities arise. Finally, when an employee leaves an organization, their access must be terminated completely and immediately. An orphaned account is a critical security vulnerability, a prime target for attackers, and a major compliance red flag.
This entire lifecycle, often called “joiner-mover-leaver,” cannot be handled manually, especially for organizations with hundreds or thousands of users. It becomes slow, error-prone, unproductive, and insecure, which is why most organizations rely on automation to address these issues.
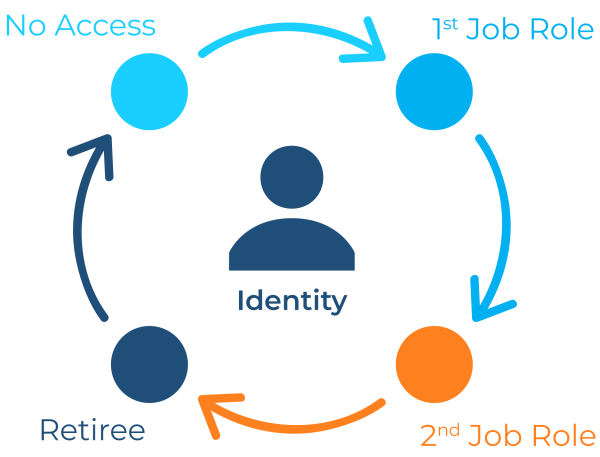
Modern IGA solutions integrate with HR systems, triggering a workflow the moment an employee joins an organization. As that employee moves through the different phases of the identity lifecycle, automated workflows route events through the proper checks and approvals and then execute the necessary steps (provisioning/deprovisioning) across on-prem and cloud systems. This entire lifecycle is managed by the IAM and Administration functions of the IGA solution.
Cayosoft Administrator is one such platform that is designed to specifically handle these challenges. Connecting seamlessly to HR systems, it provides a unified admin console for both on-prem AD and Entra ID and delivers features for rule-based provisioning, customizable workflows, and self-service portals.
For example, when a new employee joins, Cayosoft Administrator can be configured to automatically provision their AD account, assign security group memberships according to their role, and even send a welcome notification. When an employee departs, Cayosoft can automatically deactivate the account and revoke all licenses in a single workflow. Similarly, if an employee changes role, Cayosoft can adjust group memberships and roles to match. This not only reduces administrative overhead by up to 60% but also ensures consistent, error-free execution of joiner-mover-leaver processes.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Authentication and authorization
Once an identity is created and provisioned, the system requires a secure way to interact with it. This is handled by two distinct but sequential processes: authentication and authorization.
Authentication is the process of verifying a claimed identity. It answers the question: “Are you really who you say you are?” For decades, the primary method was a simple password (“something you know”). However, the endless cycle of data breaches has proven that passwords alone are woefully insecure.
Modern, strong authentication is built on the concept of multi-factor authentication (MFA) and is no longer optional; it is an absolute requirement for organizations. It typically combines two or more of the following:
- “Something you know” (e.g., a password or a PIN)
- “Something you have” (e.g., a mobile device receiving a push notification or a hardware security key)
- “Something you are” (e.g., a fingerprint or facial scan)
Once a user has been successfully authenticated, the next step is authorization, which determines the authenticated user’s permissions. It answers the question: “Now that I know who you are, what are you allowed to see and do?”
Authorization involves the enforcement of access policy. When a user tries to open a file, run a report, or delete a record, the system performs an authorization check. It examines the user’s identity and associated attributes (such as their role, department, or group memberships), and compares them against the access control list (ACL) or policy defined for that resource.
If the policy allows that user to perform that action, access is granted; if not, it is denied. This process directly implements the principle of least privilege, ensuring that users have only the minimum level of access required to perform their job functions and no more. Without effective authorization, even a perfectly authenticated user could wreak havoc.
Both authentication and authorization must be strong. Weak authentication can allow attackers to bypass the login phase, rendering authorization ineffective. Poor authorization (such as overly broad roles) can allow authenticated users to access sensitive data they shouldn’t. In a well-governed environment, even after a user is authenticated, their privileges are limited to exactly what their role and attributes allow. This tight coupling of strong authentication with granular authorization can help stop both external and insider threats.
Access control (RBAC/ABAC)
After establishing who someone is, organizations must enforce access control policies to govern every action. The traditional model is role-based access control (RBAC), where permissions are tied to roles rather than individual users. For example, an “accountant” role might be created that includes permissions to read and write in the finance system but be read-only in the CRM. All users with the job title of “accountant” are then assigned this single role.
This model simplifies administration; instead of managing permissions for thousands of users, you manage permissions for a few dozen roles. It’s scalable and relatively easy to understand. However, RBAC can become rigid and potentially lead to “role explosion,” which is why organizations are moving toward more granular models, such as attribute-based access control (ABAC) and policy-based access control (PBAC).
ABAC looks beyond fixed roles; access decisions are made in real time based on a combination of attributes about the user (department, location), the resource (sensitivity, owner), the environment (time, risk level), and the action being requested. An ABAC policy could look like this:
Allow access if User.Role == "Doctor" AND
Action == "View" AND Resource.Type == "PatientRecord"
AND User.AssignedPatients contains Resource.PatientID.
PBAC advances the principle of granular permissions further by combining users’ business roles with detailed policies, ensuring that access privileges align precisely with organizational needs. When a user attempts to access a resource, the system evaluates these policies and grants or denies access based on specified criteria.
However, a significant risk in many organizations arises from standing privileges. These accounts are highly desirable targets for attackers because they always have administrative rights. To address this vulnerability, many organizations have adopted just-in-time (JIT) access, which eliminates the need for permanent administrative rights. With JIT, no user holds permanent elevated privileges unless they have formally requested and received temporary approval for a specific task. Once the work is complete or the approved time window ends, those privileges are automatically revoked, significantly reducing the attack surface and strengthening the overall security posture.
An important point to note here is that the goal of access control in IAG is to use robust access models and modern controls like JIT and delegation to ensure least privilege. The idea is that a policy governs every access decision, and privileged roles are carefully scoped and time-limited.
To complement JIT, Cayosoft’s delegated administration models enable organizations to move away from granting broad, risky permissions, such as “domain admin” in Active Directory. Instead, they can create highly specific, delegated roles (e.g., a “help desk – password reset” role) and combine this with a JIT model.
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Governance and compliance
Everything we have discussed needs to operate within a structured framework of governance. This is the “G” in IAG and IGA, and it’s what transforms a collection of security tools into a cohesive, defensible program. It involves establishing rules, ensuring that they are followed, and providing evidence of compliance to auditors and stakeholders.
Setting up an IAG framework typically begins with the following:
- Policy definition: Identifying sensitive resources and critical applications and defining who should have access to them under what conditions
- Role and entitlement catalog: Mapping out existing roles, groups, and entitlements across systems; determining which are approved and which are outdated
- Risk assessment: Identifying the areas with the greatest identity risks (e.g., privileged accounts, third-party access, and stale accounts) and using this to prioritize controls, such as MFA enforcement or restricted service accounts
- Onboarding of owners/reviewers: Assigning business owners who will take part in access certifications and attestations for their teams or systems
Once this governance foundation is in place, specific activities ensure it is maintained over time, such as the following:
- Continuous monitoring: Effective monitoring and mitigation of identity risk require the ability to protect, monitor, and audit access to critical assets. In practical terms, this means capturing logs of logins, permission changes, role assignments, and policy violations, feeding the logs into SIEM systems or dashboards, and setting alerts for risky events.
- Access certifications and attestations: Managers or role owners will periodically “attest” whether each user’s access is still necessary. For example, each quarter, a database manager may review all users with access to a specific DBMS and approve or revoke each permission. This ensures that even if some change slips through, it will be caught.
- Secure credential management: Governance also covers how credentials (especially privileged ones) are managed. This involves using PAM solutions or hardened password managers for service accounts, enforcing certificate and key rotation, and applying MFA to all admin accounts. IAG policies should mandate that all privileged or service account credentials have an owner, be assigned an expiration date, and be stored securely.
- Policy enforcement and compliance tracking: Finally, ensure that there are automated checks for compliance policies. For example, require MFA enrollment for all employees, or ensure that no account remains inactive for more than a specified period. The system should automatically flag or remediate violations.
Manually conducting access certifications for thousands of users across dozens of systems is an impossible task. This is where the governance capabilities of an IGA platform is often critical. Solutions like Cayosoft’s Administrator address this challenge with automated policy enforcement, real-time compliance tracking, and continuous monitoring of identity activity across the hybrid environment. With policy-driven access certifications and attestations, Cayosoft Administrator ensures that managers and role owners regularly validate user access and group memberships. In addition, every critical identity change, such as logins, role assignment, and policy violations, is continuously monitored.
Audit, reporting, and identity intelligence
A mature IAG program doesn’t end with governance rules; it also requires thorough auditing and analysis of identity data. Effective auditing begins with comprehensive logging and reporting, as these are essential for proving compliance and uncovering hidden risks. You must capture a detailed record of every significant identity-related event, as follows:
- What to log: Record every login attempt (successful and failed), every access request and approval, every change to a user’s attributes, every modification to a group or role, every instance of privilege elevation (JIT), and every administrative action.
- Where to log from: It’s important to aggregate logs from all identity sources, including on-premises Active Directory and Microsoft Entra ID, into a central repository.
- How long to retain: The retention period for logs is often dictated by regulations. PCI-DSS, for example, requires logs to be kept for at least one year, with three months immediately available for analysis.
That said, raw logs are not enough. The data must be parsed, correlated, and presented in human-readable reports. These reports serve two main purposes. The first is demonstrating compliance by generating reports that show “who has access to what.” The second is enabling operational insight through reports that enable administrators to understand the state of their environment, identify users with excessive permissions, and assess the effectiveness of their security policies.
The most mature IAG programs go beyond standard reporting and embrace identity intelligence. This involves applying analytics and even machine learning to the vast sea of identity data to proactively identify risks and gain actionable insights. Instead of just reporting on who has access, identity intelligence can answer more complex questions like these:
- Are there users who have a dangerous combination of permissions that violate separation-of-duties policies?
- Which users have access patterns that are radically different from their peers? This could indicate privilege creep or a misconfigured account.
- Can we assign a risk score to each identity based on their level of privilege, the sensitivity of the data they can access, and any anomalous behavior?
The Cayosoft Management and Protection Suite offers powerful analytics engines and intuitive dashboards that transform raw log data into actionable intelligence, enabling administrators to visualize access relationships and provide security teams with the insights they need to prioritize their risk mitigation efforts, thereby shifting them from a reactive, audit-focused posture to a proactive, security-focused one.
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Conclusion
In a world where identity is the new perimeter, a proactive, intelligent, and continuous approach to governance is the only path forward. Throughout this article, we’ve covered some key concepts and looked at how rigorous audit logging, reporting, and identity intelligence give organizations the visibility needed to detect and respond to risks.
The takeaways are clear: Poor identity governance leads directly to breaches, data loss, and compliance fines. Conversely, strong IAG prevents unauthorized access, enforces separation of duties, and ensures compliance. For IT administrators, the message is not to wait for an incident to occur but to be proactive.
Plan your IAG strategy in advance, regularly review and refine policies, and invest in the right solution. Book a demo today to see how Cayosoft can help you streamline your identity and access governance.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Explore More Chapters
< Previous Chapter