Privileged group members with weak password policy
Cayosoft Threat Definition CTD-000070
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Privileged accounts with weak password policies are highly susceptible to compromise through brute-force or credential theft techniques. Without strong length, complexity, and rotation requirements, attackers can gain and maintain elevated access for extended periods.
- Severity: Critical
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Privilege Escalation, Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
A threat actor might use various techniques to obtain a password of a privileged account. To reduce risks of compromising a password, a policy to rotate and to set lengthier passwords must be implemented. The password should consist of a minimum of 12 characters, though a length of 14 characters or more is even more preferable. Periodic password expiration is a defense against the probability that a password will be compromised during its validity interval and will be used by a threat actor.
NOTE: Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1. By design, Active Directory uses this attribute to protect members of administrative groups.
According to security best practices, it is not recommended to re-use admin accounts. Instead, these accounts must be de-provisioned. If an account has administrative permissions, it might also obtain access to other resources using these permissions and keep this access even after removal from administrative groups. Learn more about AdminSDHolder and SDProp – Microsoft Community Hub.

Real-World Scenario
An attacker gains a foothold in an organization through a phishing campaign and compromises a standard user account. Scanning the environment, they discover privileged accounts with a 12-character password requirement but no enforced rotation or complexity settings. Using offline password cracking tools, the attacker breaks a weak privileged password and leverages the account’s elevated permissions to exfiltrate sensitive data and create backdoor admin accounts. Because the password policy was insufficient, the compromise went undetected for weeks. Cayosoft Guardian could have detected the weak policy and alerted administrators before the account was exploited
Catch GPO Tampering & Role Abuse Live with Cayosoft Guardian
Detect mass group changes, risky roles, and policy edits—then roll them back.
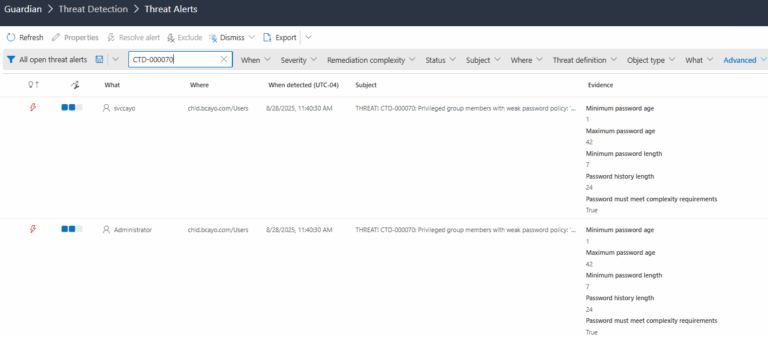
2.) View All Alerts and search for CTD-000070 or Privileged group members with weak password policy.
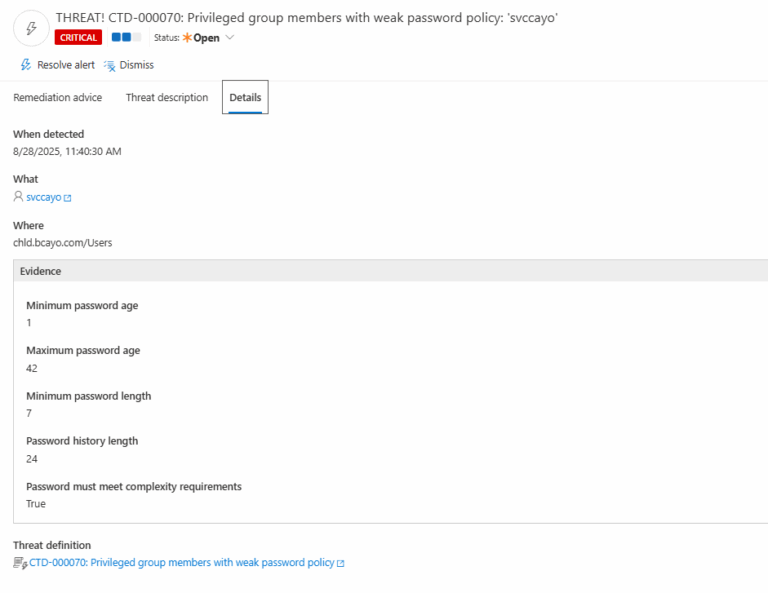
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- Minimum password age
- Maximum password age
- Minimum password length
- Password history length
- Password must meet complexity requirements
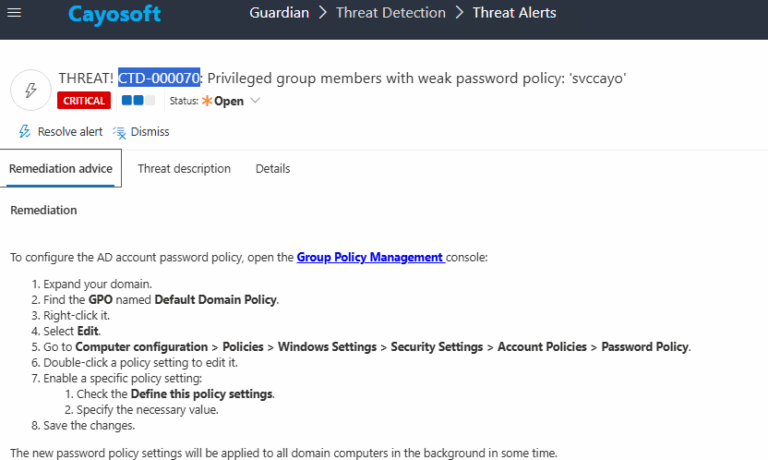
Remediation Steps
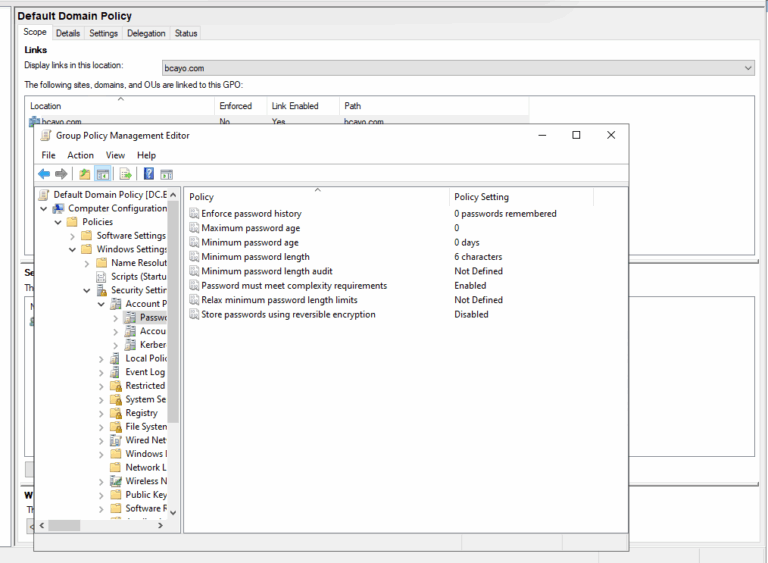
1.) Open the Group Policy Management console.
2.) Expand your domain.
3.)Find the GPO named Default Domain Policy.
4.) Right-click it and select Edit.
5.) Navigate to Computer Configuration → Policies → Windows Settings → Security Settings → Account Policies → Password Policy.
6.) Double-click a policy setting to edit it.
7.) Enable the policy:
- Check Define this policy setting.
- Specify the necessary value.
8.) Save the changes.
The updated policy will be applied to all domain computers in the background
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Privileged group members with weak password policy. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
A password should have a minimal password length of 14
The new guidance is to not enforce password rotation focus more on password length and enforce MFA
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged group members with weak password policy, you reduce attack surfaces and strengthen your organization’s overall security posture..