Privileged AD account password set to never expire
Cayosoft Threat Definition CTD-000033
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A privileged account with Password never expires allows indefinite credential reuse and persistence. If the password is stolen, an attacker can authenticate until the password is changed.
- Severity: High
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Credential Rotation
Description
The privileged user account whose password never expires poses a threat to your environment. A password obtained by a malicious actor will be valid until the password is changed. In the meantime, the malicious actor will be able to log in to Active Directory, access resources, and inflict damage. Regular password rotation reduces the risk and effectiveness of password-based attacks by shortening the timeframe during which a compromised password may be valid.
NOTE: Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1. By design Active Directory uses this attribute to protect members of administrative groups. Learn more about AdminSDHolder and SDProp in Microsoft guidance.

Real-World Scenario
A contractor’s legacy admin account was granted temporary rights months ago and marked Password never expires. After a phishing campaign, the attacker obtains the password and starts authenticating to AD and privileged systems at will. Because the account is privileged (adminCount=1), AdminSDHolder protections preserve elevated ACLs even if the user is later removed from groups, enabling continued lateral movement. The attacker quietly creates shadow admin paths and exfiltrates data over weeks. Cayosoft Guardian would raise CTD-000033 as soon as the privileged account was found with a non-expiring password, giving responders time to rotate credentials and revoke access.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
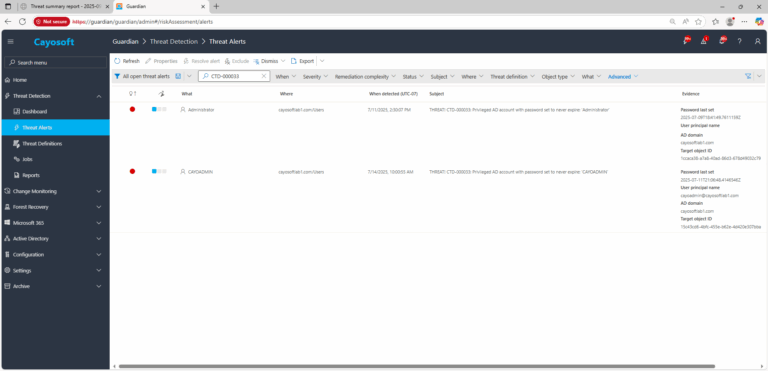
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000033 or Privileged AD account password set to never expire.
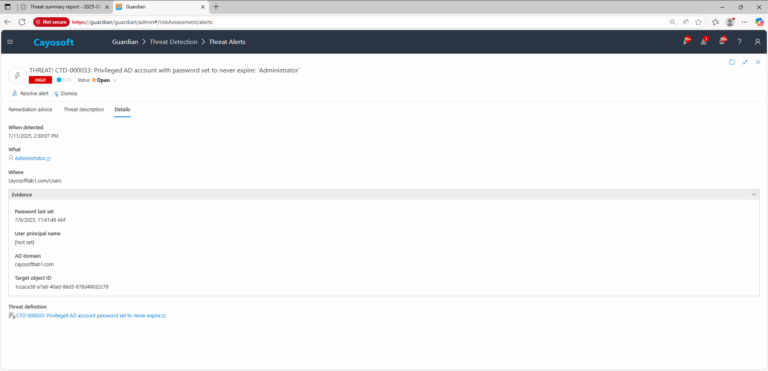
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- Password last set
- User principal name
- AD domain
- Target object ID (values may appear redacted; verify in native directory tools as needed).
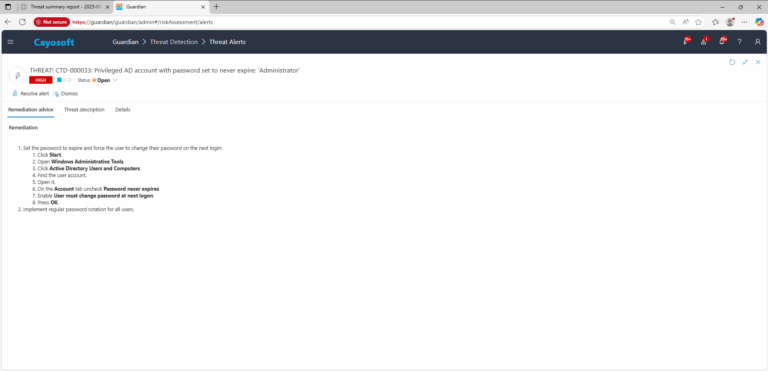
Remediation Steps
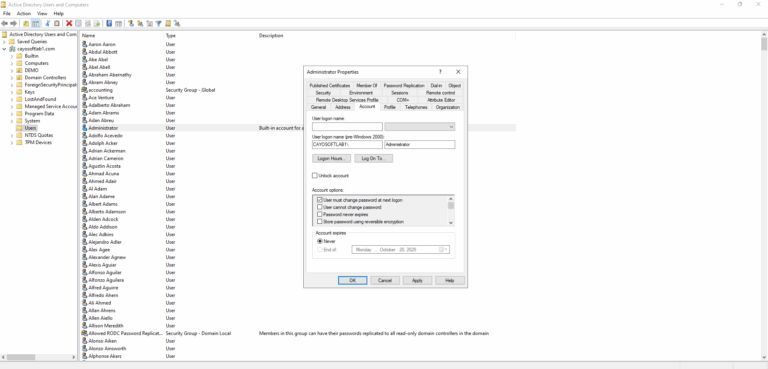
- ) Set the password to expire and force the user to change their password on the next login:
- ) Click Start.
- ) Open Windows Administrative Tools.
- ) Click Active Directory Users and Computers.
- ) Find the user account.
- ) Open it.
- ) On the Account tab uncheck Password never expires.
- ) Enable User must change password at next logon.
- ) Press OK.
- ) Implement regular password rotation for all users.
How to Prevent It
- Enforce rotation for all privileged accounts; prohibit Password never expires except for managed break-glass accounts with strict controls.
- Replace standing admin accounts with Just-In-Time (JIT) elevation and MFA.
- Regularly audit adminCount=1 users for risky flags (non-expiring password, delegation, unconstrained delegation).
- Cayosoft Guardian can proactively detect and alert on Privileged AD account password set to never expire. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Such an account creates a permanent attack vector. If the password is compromised, the attacker gains unlimited access to AD and can maintain control even after removal from admin groups due to the AdminSDHolder mechanism.
Simply unchecking the flag does not guarantee that the password will be changed. The account may remain vulnerable if the password is old and already compromised. It is necessary to enforce “ChangePasswordAtLogon” or initiate an immediate password rotation.
Running regular PowerShell audit scripts (with the filter adminCount=1), configuring Group Policy to prohibit setting this flag, and implementing SIEM/identity solutions (Cayosoft Guardian, Azure AD PIM) that automatically detect such misconfigurations.
References
- adminCount attribute (Microsoft Open Specifications): https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- Five common questions about AdminSDHolder and SDProp – Microsoft Community Hub: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged AD account password set to never expire, you reduce attack surfaces and strengthen your organization’s overall security posture.