Microsoft Entra tenant with unsecure access to Azure management
Cayosoft Threat Definition CTD-000038
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
If access to Azure management tools (Entra admin center, Azure PowerShell, Azure CLI) isn’t protected with MFA, a compromised account can be used to reach highly privileged resources immediately.
- Severity: High
- Platform: Entra ID
- Category: Tenant-wide, Conditional Access
- MITRE ATT&CK Tactics: Execution, Command and Control
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Organizations use many Azure services and manage them from Azure Resource Manager–based tools like Microsoft Entra admin center, Azure PowerShell, and Azure CLI. These tools provide highly privileged access to resources. To protect these privileged resources, Microsoft recommends requiring multifactor authentication (MFA) for any user accessing these resources. Without MFA enforced, a threat actor might compromise an account and immediately get access to the privileged resources.

Real-World Scenario
A phishing campaign captures the password of a helpdesk user who has occasional Azure access. Because the tenant doesn’t enforce MFA for Azure management, the attacker signs into the Entra admin center and uses Azure RBAC to grant themselves Owner at subscription scope. They deploy a new app registration, add a secret, and exfiltrate data via scripted automation. Activity blends with normal admin traffic, enabling persistence and rapid impact. Cayosoft Guardian would flag the missing Conditional Access (require MFA for Azure management) control before the privilege abuse spreads.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
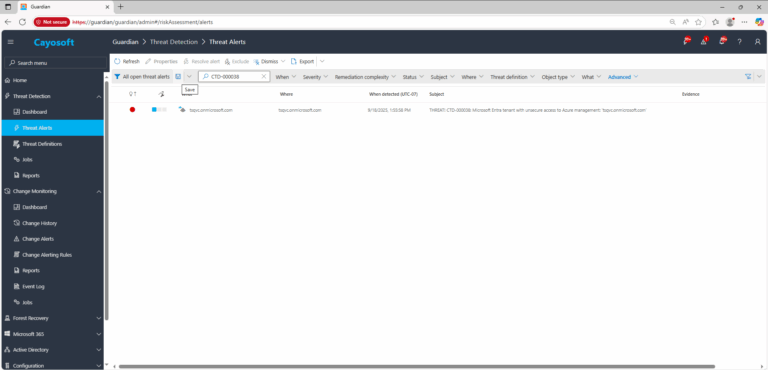
2.) Open All Alerts and search for CTD-000038 or Microsoft Entra tenant with unsecure access to Azure management.
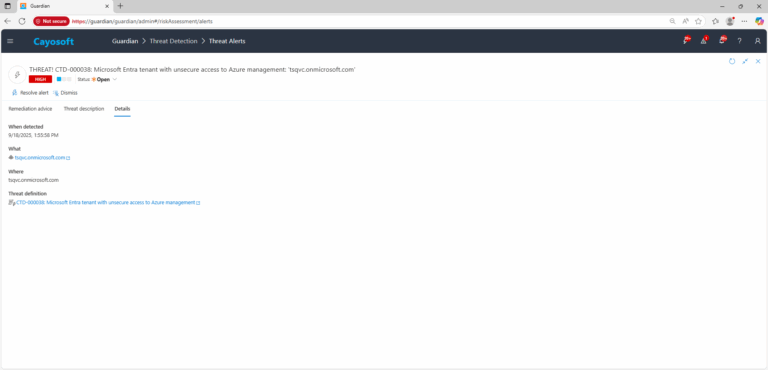
3.) Open any alert and Click for details (from Raise Threat Alert action).
Remediation Steps
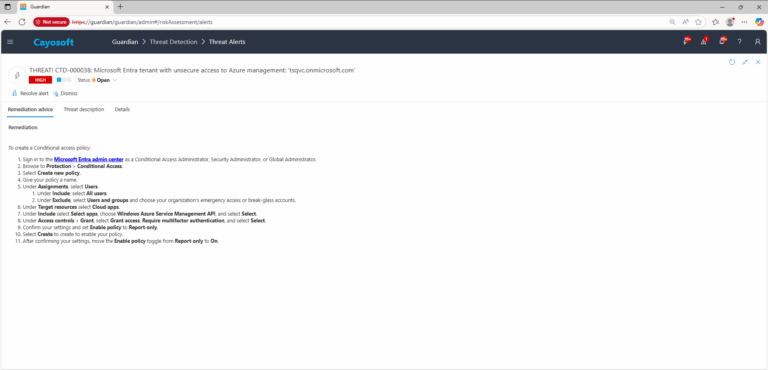
To create a Conditional access policy:
- ) Sign in to the Microsoft Entra admin center as a Conditional Access Administrator, Security Administrator, or Global Administrator.
- ) Browse to Protection > Conditional Access.
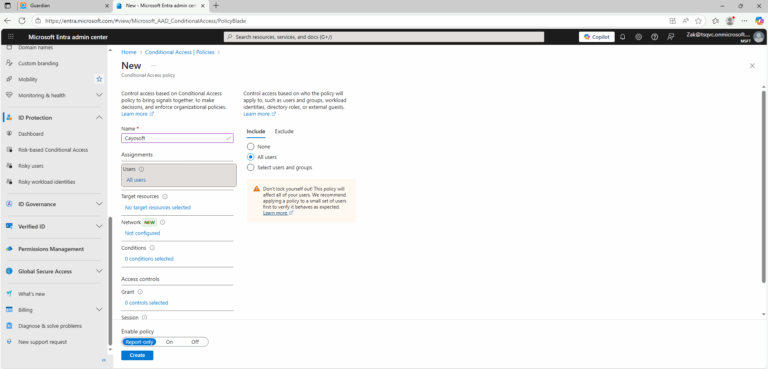
- ) Select Create new policy.
- ) Give your policy a name.
- ) Under Assignments, select Users.
- ) Under Include, select All users.
- ) Under Exclude, select Users and groups and choose your organization’s emergency access or break-glass accounts.
- ) Under Target resources select Cloud apps.
- ) Under Include select Select apps, choose Windows Azure Service Management API, and select Select.
- ) Under Access controls > Grant, select Grant access, Require multifactor authentication, and select Select.
- ) Confirm your settings and set Enable policy to Report-only.
- ) Select Create to create to enable your policy.
- ) After confirming your settings, move the Enable policy toggle from Report-only to On.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on unsecure access to Azure management. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
These tools (Entra admin center, Azure PowerShell, Azure CLI) provide privileged access to resources. Without MFA, an attacker with a stolen password can immediately assign themselves Owner roles or create hidden apps to exfiltrate data.
It is the service principal that represents all Azure management endpoints. By including it in a Conditional Access policy, you ensure that any administrative actions via ARM portals and CLI require MFA.
Create a new Conditional Access policy, include all users, and exclude only emergency (break-glass) accounts. Start in Report-only mode, validate sign-in results, remediate exceptions, then switch the policy to On.
Final Thought
- Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like unsecure access to Azure management, you reduce attack surfaces and strengthen your organization’s overall security posture.