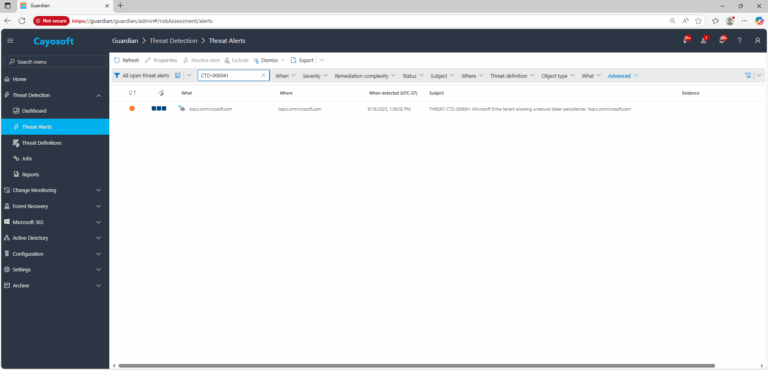
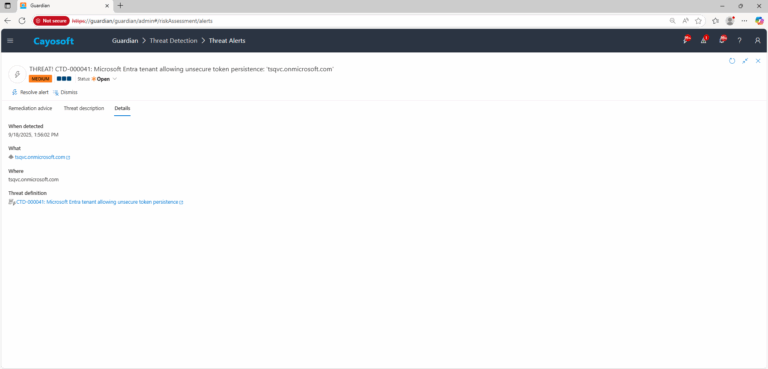
Microsoft Entra tenant allowing unsecure token persistence
Cayosoft Threat Definition CTD-000041
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Unsecure token persistence enables a stolen Primary Refresh Token (PRT) to be reused, bypassing MFA and Conditional Access and granting ongoing access to tenant resources.
- Severity: Medium
- Platform: Entra ID
- Category: Account protection, Tenant-wide, Privileged Access Management
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening, Credential Transmission Scoping
Description
A Primary Refresh Token (PRT) is a key artifact of Microsoft Entra authentication on Windows 10 or newer, Windows Server 2016 and later versions, iOS, and Android devices. It is a JSON Web Token (JWT) specially issued to Microsoft first party token brokers to enable single sign-on (SSO) across the applications used on those devices. After an administrator logs in on a device, PRT is cached on the client. If a device used by the administrator is left unattended or compromised, a threat actor might be able to extract PRT and use it to access your tenant bypassing MFA.

Real-World Scenario
An attacker compromises an admin workstation via a malicious browser extension, then dumps the device’s token cache to extract a valid PRT. Because browser sessions are persistent and sign-in frequency is lax, the attacker silently exchanges the PRT for fresh access tokens, bypassing MFA and Conditional Access prompts. They enroll a rogue device, create inbox rules for exfiltration, and add an app secret for persistence. Cayosoft Guardian raises CTD-000041 on unsecure token persistence so operators can enforce frequent reauthentication and disable persistent sessions for privileged roles before further abuse.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
2.) View All Alerts and search for CTD-000041 or Microsoft Entra tenant allowing unsecure token persistence.
3.) Open any alert and Click for details (from Raise Threat Alert action).
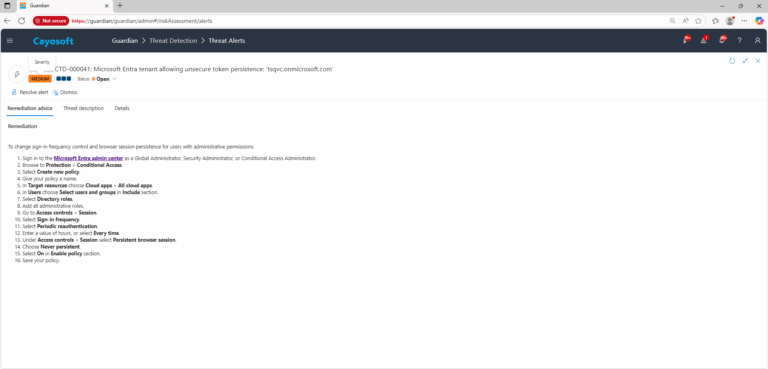
Remediation Steps
To change sign-in frequency control and browser session persistence for users with administrative permissions:
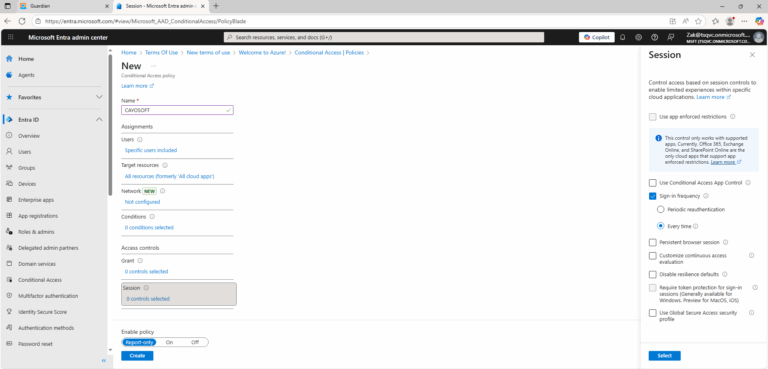
- ) Sign in to the Microsoft Entra admin center as a Global Administrator, Security Administrator, or Conditional Access Administrator.
- ) Browse to Protection > Conditional Access.
- ) Select Create new policy.
- ) Give your policy a name.
- ) In Target resources choose Cloud apps > All cloud apps.
- ) In Users choose Select users and groups in Include section.
- ) Select Directory roles.
- ) Add all administrative roles.
- ) Go to Access controls > Session.
- ) Select Sign-in frequency.
- ) Select Periodic reauthentication.
- ) Enter a value of hours, or select Every time.
- ) Under Access controls > Session select Persistent browser session.
- ) Choose Never persistent.
- ) Select On in Enable policy section.
- ) Save your policy.
How to Prevent It
- Apply Conditional Access session controls to all administrative directory roles: short Sign-in frequency and Never persistent browser sessions.
- Require compliant or hybrid-joined devices for admin access; enforce hardening and screen lock on privileged workstations.
- Use PIM for just-in-time activation of admin roles; avoid standing privileges.
- Monitor for policy drift with Cayosoft Guardian and review sign-in logs for unusual token refresh patterns.
FAQ
It is a configuration where administrators can maintain persistent browser sessions or infrequent reauthentication. This makes a stolen Primary Refresh Token (PRT) more valuable, since attackers can reuse it to access tenant resources while bypassing MFA and Conditional Access.
If attackers extract a PRT from a compromised admin device, they can continuously refresh access tokens without being challenged by MFA or reauthentication. This enables long-term unauthorized access, device enrollment, or creation of persistence mechanisms such as app secrets.
By monitoring with tools like Cayosoft Guardian or Microsoft Entra sign-in logs. Indicators include persistent sessions, infrequent reauthentication for privileged roles, and unusual token refresh activity across admin accounts.
References
- Microsoft Entra admin center: https://entra.microsoft.com/
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra tenant allowing unsecure token persistence, you reduce attack surfaces and strengthen your organization’s overall security posture.