Microsoft Entra role with permanent active members
Cayosoft Threat Definition CTD-000016
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
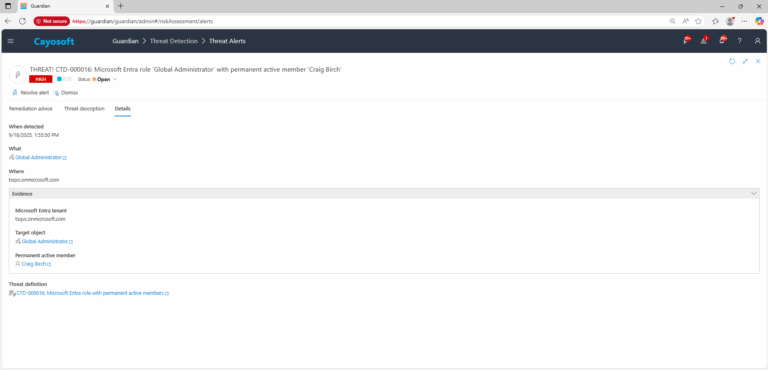
Permanent active role assignments might indicate threat activity. If a permanently active privileged account is compromised, an attacker gains immediate and continuous administrative access without just-in-time controls.
- Severity: High
- Platform: Entra ID
- Category: Privileged Access Management
- MITRE ATT&CK Tactics: Persistence, Privilege Escalation, Defense Evasion
- MITRE D3FEND Tactics: User Account Permissions
Description
Permanent active role assignments might be an indication of threat activities. If an account with permanent active role membership is compromised, a threat actor immediately gets access to administrative privileges. Using only time-limited role assignments for administrators increases security posture in your tenant because role activation can be protected with MFA at activation time or approval.

Real-World Scenario
An attacker phishes a helpdesk engineer who has a permanently active Privileged Role Administrator assignment. Because the role is always active, the attacker immediately creates a new global admin, adds a backdoor app role assignment, and disables alerting mailboxes to avoid detection. With continuous privileges, the attacker exfiltrates data and establishes persistence via additional permanent role assignments. Cayosoft Guardian detects the existence of permanent active members and raises CTD-000016 before or during the change review, enabling rapid removal and investigation.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
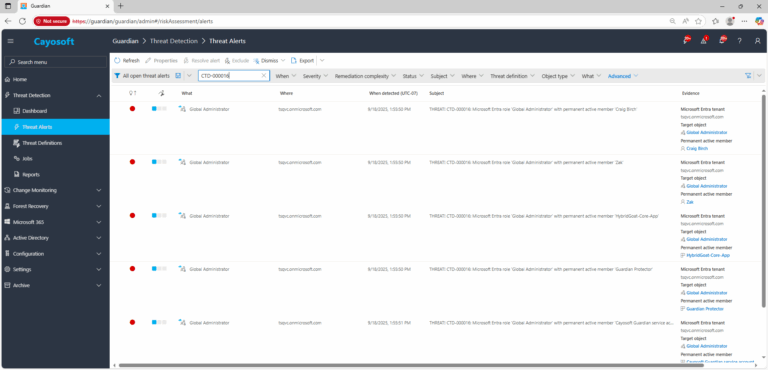
2.) View All Alerts and search for CTD-000016 or Microsoft Entra role with permanent active members.
3.) Open any alert and Click for details (from Raise Threat Alert action).
Remediation Steps
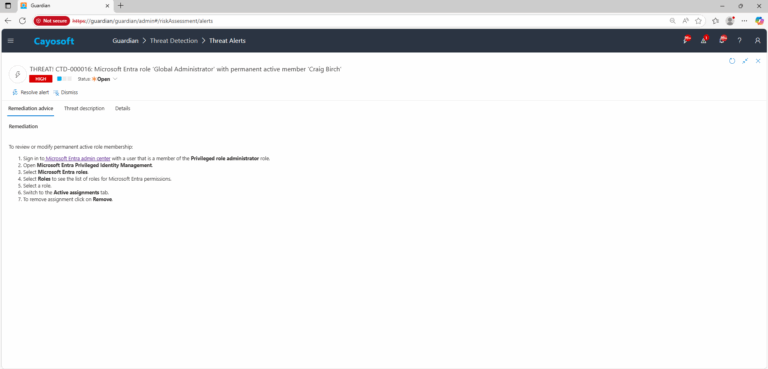
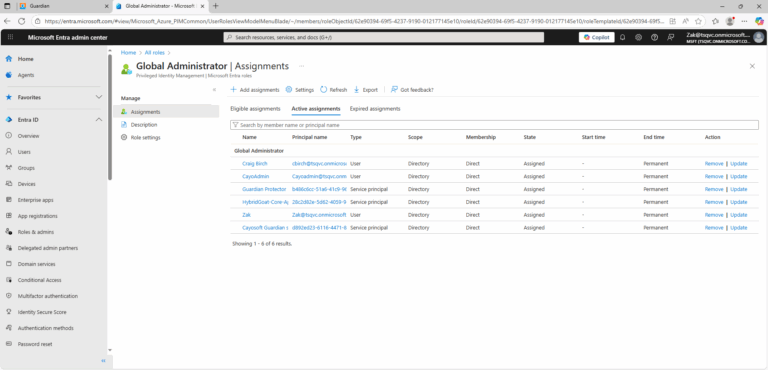
- ) Sign in to Microsoft Entra admin center with a user that is a member of the Privileged role administrator role.
- ) Open Microsoft Entra Privileged Identity Management.
- ) Select Microsoft Entra roles.
- ) Select Roles to see the list of roles for Microsoft Entra permissions.
- ) Select a role.
- ) Switch to the Active assignments tab.
- ) To remove assignment click on Remove.
How to Prevent It
- Enforce PIM: require eligible, time-limited role assignments with approval and MFA on activation.
- Prohibit permanent active assignments for privileged roles; allow exceptions only for break-glass accounts with strict controls.
- Run periodic access reviews for privileged roles and remove inactive or unnecessary assignments.
- Monitor for newly created permanent assignments and alert immediately (Cayosoft Guardian policy CTD-000016).
FAQ
A user or service principal assigned to a role that is always active (not eligible or time-limited), granting continuous privileges.
Yes, but limit them to the minimum, store credentials securely, exclude from conditional access where appropriate, and audit frequently.
Eligible users must activate the role just-in-time, often with approval and MFA, reducing persistence and privilege abuse risk.
References
- Microsoft Entra admin center: https://entra.microsoft.com/
- PowerShell wildcards reference (used in role matching masks UI): https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_wildcards
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra role with permanent active members, you reduce attack surfaces and strengthen your organization’s overall security posture.