Microsoft Entra Global Administrator with elevated access to Azure Resources
Cayosoft Threat Definition CTD-000013
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
After compromising a helpdesk user, an attacker laterally moves and obtains Global Administrator. Using the elevate access capability, the attacker assigns self User Access Administrator at the root scope (/). The attacker then grants a backdoor Owner role on a hidden app registration and spins up costly services. Even if the GA account is remediated in Entra ID, the Azure RBAC backdoors persist. Cayosoft Guardian detects the Global Administrator with elevated Azure access and raises an alert before the attacker can entrench further.
- Severity: Critical
- Platform: Entra ID
- Category: Azure resources , Account protection
- MITRE ATT&CK Tactics: Privilege Escalation
- MITRE D3FEND Tactics: User Account Permissions
Description
By design, Microsoft Entra ID and Azure resources are secured independently. Entra role assignments don’t grant access to Azure resources, and Azure role assignments don’t grant access to Entra ID. However, a Global Administrator can assign themselves access to all Azure subscriptions and management groups in the directory (root scope). Such a change may indicate a threat actor elevated permissions to access Azure resources. If the change was approved, remove elevated access once required tasks at root scope are complete.

Real-World Scenario
A phishing campaign convinces a project manager to grant consent to a look-alike “Docs Sync Assistant” app requesting Mail.Send, Files.ReadWrite.All, and Directory.ReadWrite.All. The attacker uses refresh tokens to persist and silently exfiltrate files and emails while creating hidden mailbox forwarding rules. With directory write permissions, the attacker modifies service principal properties to blend in and assigns additional app roles to expand access without creating new user accounts. Business impact includes unauthorized data sharing, regulatory exposure, and configuration tampering that survives password resets. Cayosoft Guardian flags the service principal for risky write permissions and raises an alert before further lateral movement.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
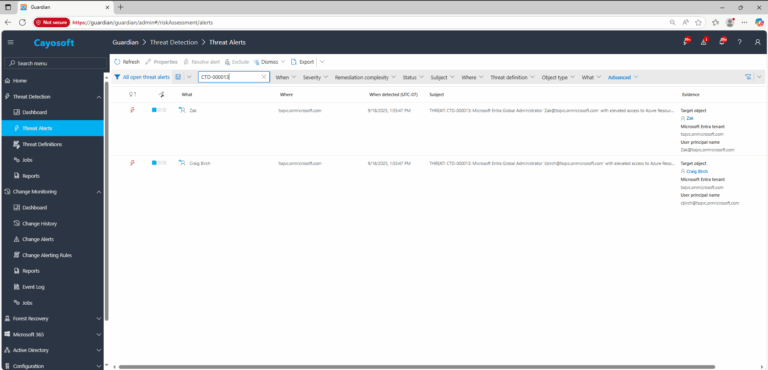
2.) Open All Alerts and search for CTD-000013 or Microsoft Entra Global Administrator with elevated access to Azure Resources.
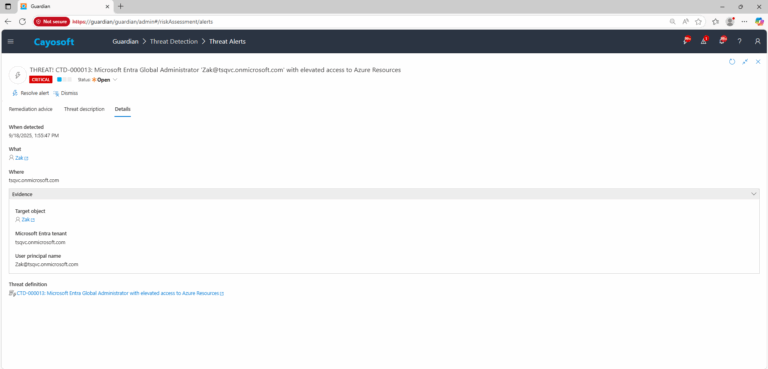
3.) Open any alert and Click for details (from Raise Threat Alert action).
3.) Review Evidence:
- Target object
- Microsoft Entra tenant
- User principal name
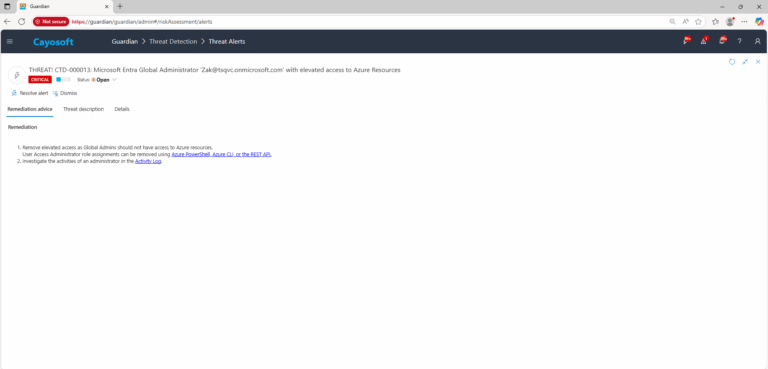
Remediation Steps
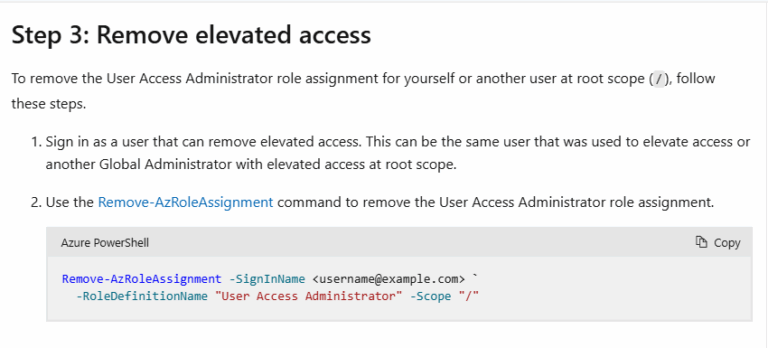
- ) Remove elevated access as Global Admins should not have access to Azure resources.
User Access Administrator role assignments can be removed using Azure PowerShell, Azure CLI, or the REST API. - ) Investigate the activities of an administrator in the Activity Log.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Global Administrators with elevated access to Azure resources. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
References
- Microsoft: Elevate access for a Global Administrator — https://learn.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin
- Entra portal: Activity Log — https://entra.microsoft.com/#view/Microsoft_Azure_Monitoring/AzureMonitoringBrowseBlade/~/activityLog
FAQ
It is the process where a Global Administrator assigns themselves the User Access Administrator role at the root scope (/), gaining the ability to manage RBAC across all Azure subscriptions and management groups.
Query role assignments at the root scope (/) to verify whether the Global Administrator holds User Access Administrator or Owner roles. Also review the Activity Log for elevation events and downstream RBAC changes.
Elevated access should remain only for the minimal time required to complete root-scope tasks. Once finished, the assignment must be removed immediately and documented in the change log.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Global Administrators with elevated access to Azure resources, you reduce attack surfaces and strengthen your organization’s overall security posture.