Entra ID Missing Conditional Access Policy for blocking access for untrusted locations
Cayosoft Threat Definition CTD-000162
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Without a Conditional Access (CA) policy that blocks sign-ins from untrusted locations, threat actors can authenticate from risky IP ranges or regions and bypass a critical control that limits where tenant access is allowed.
- Severity: High
- Platform: Entra ID
- Category: Account protection, Tenant-wide
- MITRE ATT&CK Tactics: Initial Access, Defense Evasion
- MITRE D3FEND Tactics: D3-APA (Access Policy Administration)
Description
The absence of a Conditional Access policy in Entra ID to block access from untrusted locations represents a significant vulnerability. Threat actors can exploit this gap by attempting unauthorized access from external and high-risk locations. Without a policy to deny such attempts, the environment is exposed to credential compromise, brute force, and other attack methods. Proper Conditional Access policies enhance defense mechanisms by ensuring only trusted locations can interact with critical services.

Real-World Scenario
An attacker steals a user’s password via phishing and signs in from a foreign VPS. Because no CA “block untrusted locations” policy exists, the sign-in succeeds and the attacker registers a managed device to blend into normal traffic. The attacker then sets mailbox forwarding and enrolls a malicious authenticator app to persist. Travel and VPN traffic mask the anomaly, allowing lateral movement and data exfiltration. Cayosoft Guardian detects the missing CA control at the tenant level and raises an alert before more accounts are abused.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
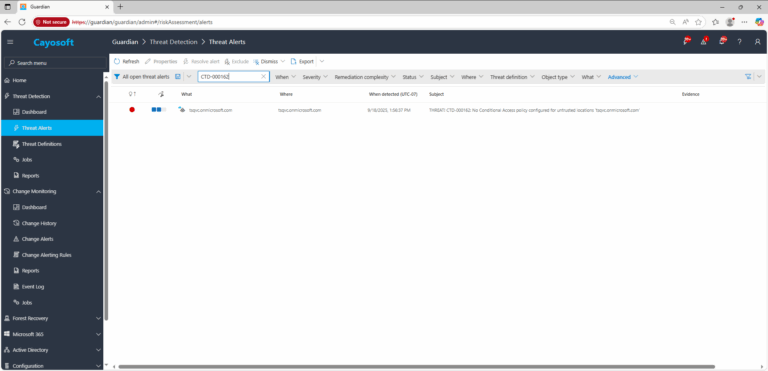
2.) Open All Alerts and search for CTD-000162 or Entra ID Missing Conditional Access Policy for blocking access for untrusted locations.
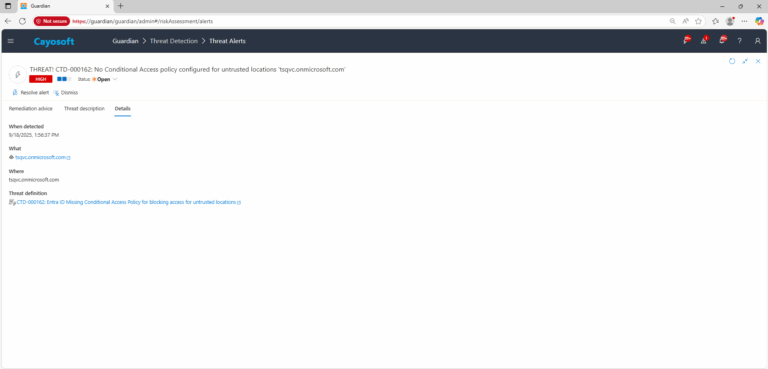
3.) Open any alert and Click for details (from Raise Threat Alert action).
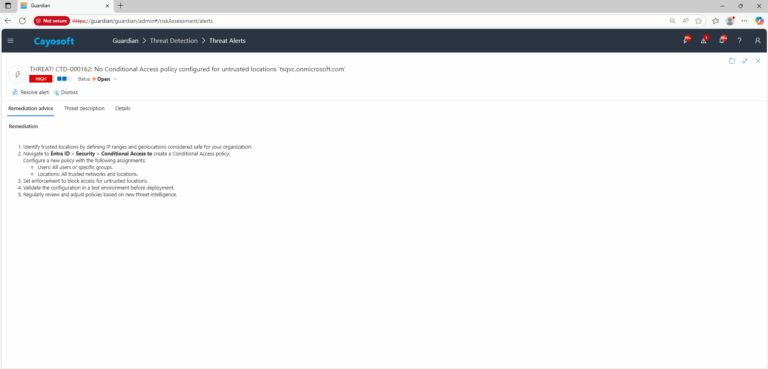
Remediation Steps
- ) Identify trusted locations by defining IP ranges and geolocations considered safe for your organization.
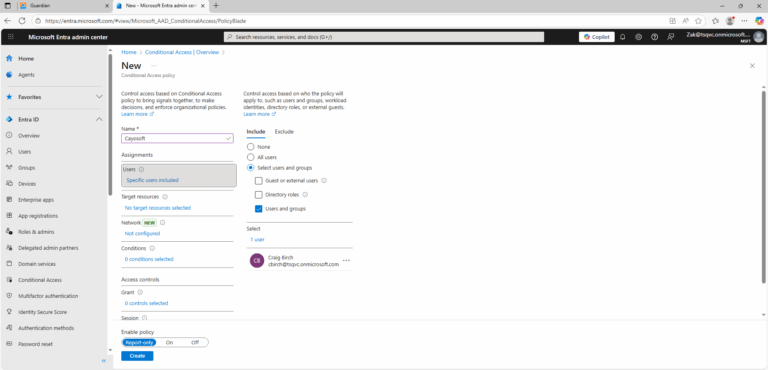
- ) Navigate to Entra ID > Security > Conditional Access to create a Conditional Access policy:
Configure a new policy with the following assignments:- Users: All users or specific groups.
- Locations: All trusted networks and locations.
- ) Set enforcement to block access for untrusted locations.
- ) Validate the configuration in a test environment before deployment.
- ) Regularly review and adjust policies based on new threat intelligence.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on missing Conditional Access policies for untrusted locations. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Untrusted locations are any IP ranges or regions not defined as trusted (named locations) for your organization. Examples include foreign regions, VPN egress points, anonymizers, or residential ISP addresses.
It is better to use trusted IP ranges for precision. Regional blocking can reduce broad risk but may impact traveling employees or remote staff.
Always exclude at least one break-glass account from the block policy and protect it with strong, offline-stored credentials. Start with Report-only mode or a pilot group, review sign-in logs, and only then enforce it for all users.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like missing Conditional Access policies for untrusted locations, you reduce attack surfaces and strengthen your organization’s overall security posture.