Built-in Domain Administrator Account Used Recently
Cayosoft Threat Definition CTD-000027
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
The built-in domain Administrator account is a high-value target for attackers. Recent use of this account may indicate compromise, as it bypasses many audit controls and provides unrestricted access to the domain.
- Severity: Critical
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Defense Evasion
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
The usage of a built-in domain Administrator account might be an indication that the account has been compromised. This account is a permanent, highly privileged identity in Active Directory and should not be used for daily administrative tasks. Frequent or unexplained use of this account can mask malicious activity and make attribution difficult.

Real-World Scenario
A malicious insider or external attacker obtains the credentials for the built-in domain Administrator account through phishing or credential dumping. They use the account to disable security tools, create hidden backdoor accounts, and exfiltrate sensitive data — all without raising immediate suspicion because activity appears to originate from a trusted, permanent admin identity. Regular IT audits fail to catch the activity due to the account’s elevated privileges and lack of normal usage patterns. Cayosoft Guardian detects this anomalous usage within the defined monitoring interval and alerts security teams before further compromise occurs.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
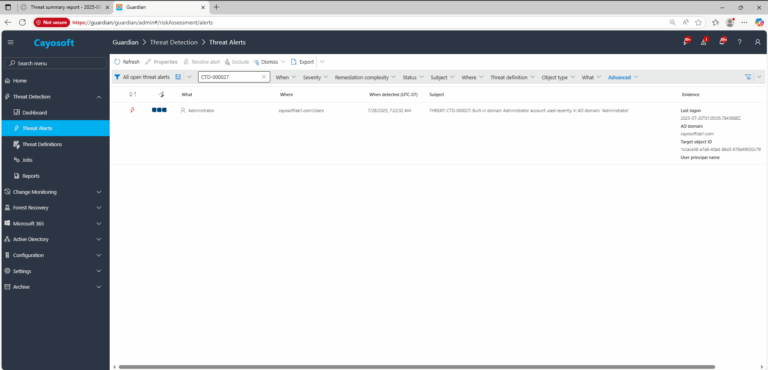
2.) View All Alerts and search for CTD-000027 or Built-in domain Administrator account used recently.
3.) Open any alert and Click for details (from Raise Threat Alert action).
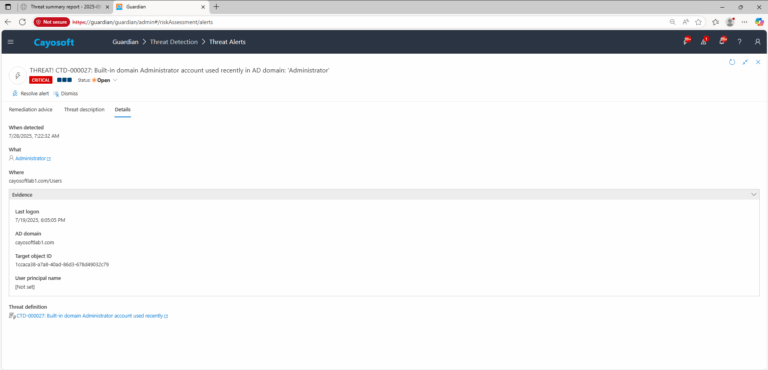
4.) Review Evidence:
- Last logon
- AD domain
- Target object ID
- User principal name
Remediation Steps
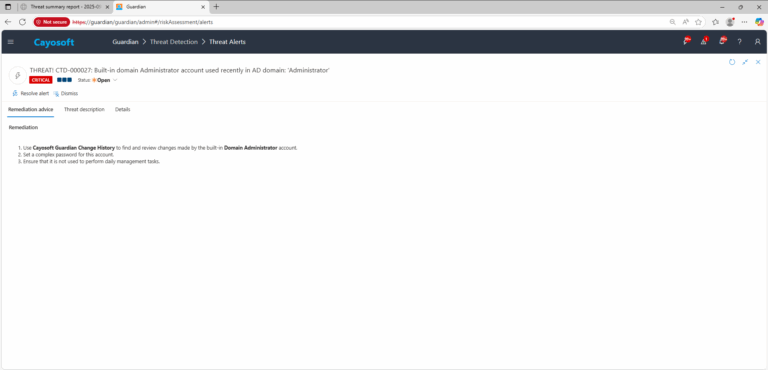
1.) Use Cayosoft Guardian Change History to review recent changes made by the built-in Domain Administrator account.
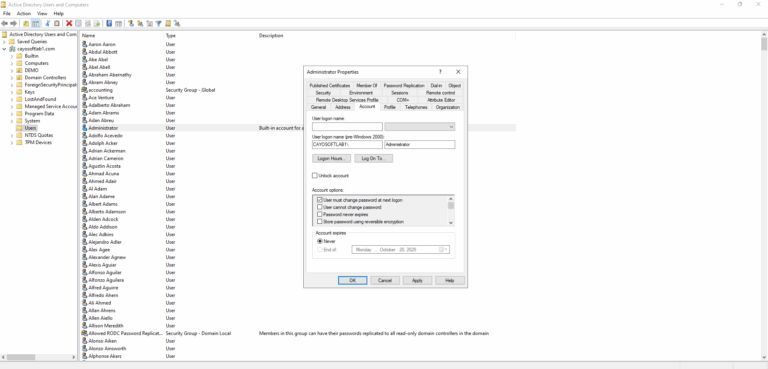
2.) Set a complex password for this account.
3.) Ensure the account is not used for daily management tasks — reserve it for break-glass or recovery scenarios only.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on suspicious use of the built-in domain Administrator account. Continuous monitoring and alerting help enforce least privilege principles, ensure the account is only used when absolutely necessary, and reduce the risk of undetected domain-wide compromise.
FAQ
It has unrestricted access to the domain, is always present in AD, and its use can bypass normal monitoring and change-control processes.
Only for emergency recovery or critical maintenance that cannot be performed with delegated accounts.
Use a complex password, store it securely offline, monitor all logons, and disable interactive logons where possible.
Final Thought
Limiting and monitoring the use of the built-in domain Administrator account is essential for reducing your organization’s attack surface. Detecting and responding to unusual activity on this account can prevent complete domain compromise.