AD object with schema update permissions
Cayosoft Threat Definition CTD-000122
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An account with permissions to update the Active Directory schema can introduce malicious changes that compromise the entire forest or render it inoperable. Schema modifications are forest-wide, irreversible without restore, and often bypass typical administrative controls.
- Severity: Critical
- Platform: Active Directory
- Category: Forest-wide
- MITRE ATT&CK Tactics: Persistence, Impact
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
The Active Directory schema defines every object class and attribute that can exist in the forest. It acts as the blueprint for all directory data and is itself an AD object that can be modified.
If a threat actor gains schema update rights, they could:
- Add malicious attributes to user or computer objects.
- Alter existing definitions to weaken security controls.
- Disrupt authentication and application integration.
Because schema changes replicate to all domain controllers and cannot be easily undone, misuse can have severe, long-lasting effects on both security and operations.

Real-World Scenario
An attacker compromises an account with delegated rights to modify the AD schema. They add a hidden attribute to the user object class designed to store alternate credentials. These credentials allow the attacker to log in even if the original account is disabled.
The change propagates to all domain controllers, embedding persistence deep into the forest.
Cayosoft Guardian detects accounts with schema update permissions and raises an alert before such persistence mechanisms can be deployed.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Go to All Alerts and search for CTD-000122 or “schema update permissions”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
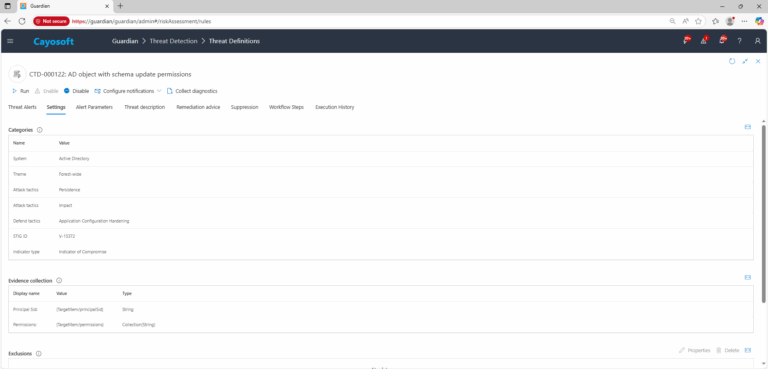
4.) Review Evidence:
- Principal Sid
- Permissions
Remediation Steps
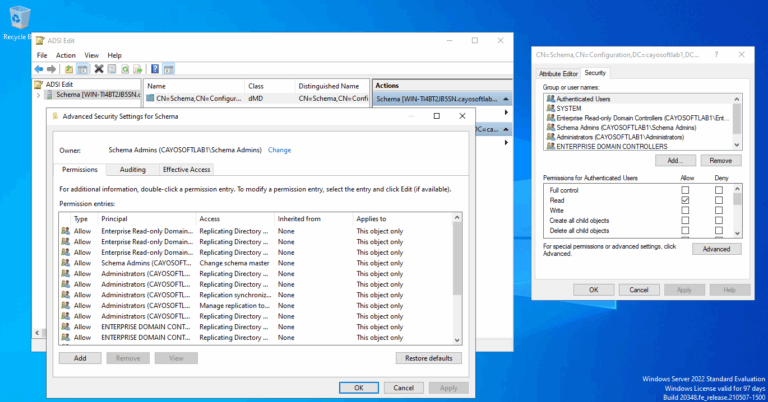
To review permissions on the schema object in Active Directory using ADSI Edit:
- ) Press Win + R to open the Run dialog.
- ) Type adsiedit.msc and press Enter.
- ) Right-click on ADSI Edit and select Connect to.
- ) Choose Select or type a domain or server.
- ) Enter the server/domain name where the schema is located.
- ) Select Select a well-known Naming Context and choose Schema.
- ) Click OK.
- ) Expand the Schema node.
- ) Find and click on CN=Schema,CN=Configuration.
- ) Right-click on CN=Schema,CN=Configuration and select Properties.
- ) Go to the Security tab to view permissions.
- ) Click the Advanced button to access advanced security settings.
- ) Click Edit to make changes.
- ) Add, remove, or adjust permissions for users/groups.
- ) Ensure changes align with your organization’s policies.
- ) Verify modifications before applying them.
- ) Click OK or Apply to save changes.
- ) Close ADSI Edit to complete the process.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on accounts with schema update permissions. Continuous monitoring of Active Directory security settings helps prevent persistence and destructive changes from being introduced into the forest.
FAQ
Schema changes affect the entire Active Directory forest, replicate to all domain controllers, and cannot be easily rolled back without a full restore. Unauthorized changes can introduce persistence, weaken security controls, or disrupt operations.
They can add malicious attributes to user or computer objects, alter object definitions to bypass security, or embed hidden credentials that survive account disablement.
Tools like Cayosoft Guardian monitor AD permissions and raise alerts whenever an account has delegated rights to modify the schema.
Final Thought
Proactive monitoring and control over who can modify the AD schema is critical. Addressing excessive schema update permissions reduces the risk of forest-wide compromise and long-term persistence.