AD Domain Controller with Non-Admin Owner
Cayosoft Threat Definition CTD-000098
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
If a Domain Controller (DC) computer object in Active Directory has an owner who is not a member of Domain Admins, Enterprise Admins, or the Built-in Administrators group, that user could elevate their privileges to full administrative control of the domain.
- Severity: Critical
- Platform: Active Directory
- Category: Account Protection, Privileged Access Management
- MITRE ATT&CK Tactics: Privilege Escalation, Persistence, Defense Evasion
- MITRE D3FEND Tactics: System Configuration Permissions
Description
In Active Directory, the owner of an object has the ability to change its permissions—even if they aren’t currently granted explicit rights.
If a non-admin becomes the owner of a DC computer account, they can grant themselves Full Control permissions, enabling them to perform dangerous actions such as:
- Modifying security policies
- Installing backdoors or malicious software
- Extracting sensitive credentials
- Disabling security monitoring
This creates a serious pathway for privilege escalation, persistence, and defense evasion.

Real-World Scenario
An attacker compromises a mid-level IT support account that is incorrectly listed as the owner of a DC computer object.
Using this ownership, they change the object’s permissions to give themselves full administrative rights.From there, they use DCSync to extract password hashes for all users, including domain admins, and maintain persistent access, evading detection for months.
Cayosoft Guardian would have detected the non-admin owner and raised an alert before privilege abuse occurred.
Fix Group/Policy Mistakes in Seconds with Cayosoft Guardian
Reverse misconfigurations instantly—no scripts, no downtime.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
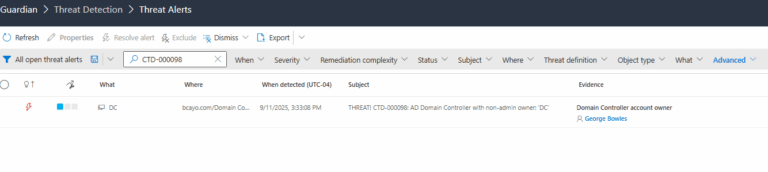
2.) View All Alerts and search for CTD-000098 or AD Domain Controller with non-admin owner
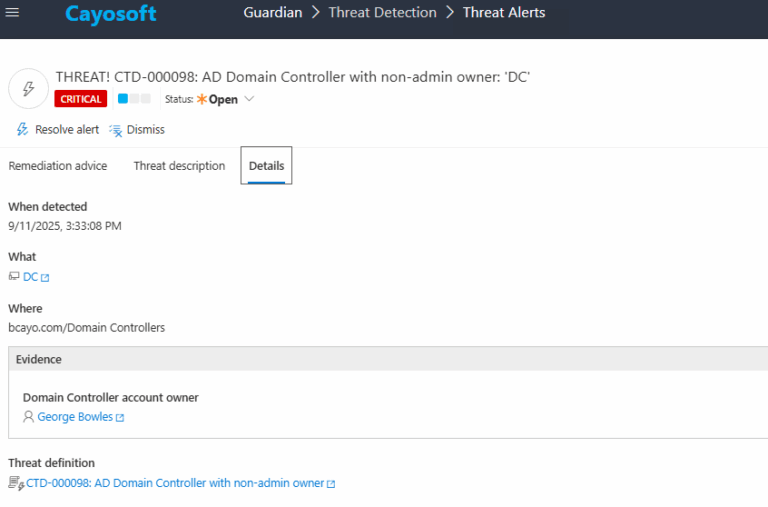
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- Domain Controller Account Owner
Remediation Steps
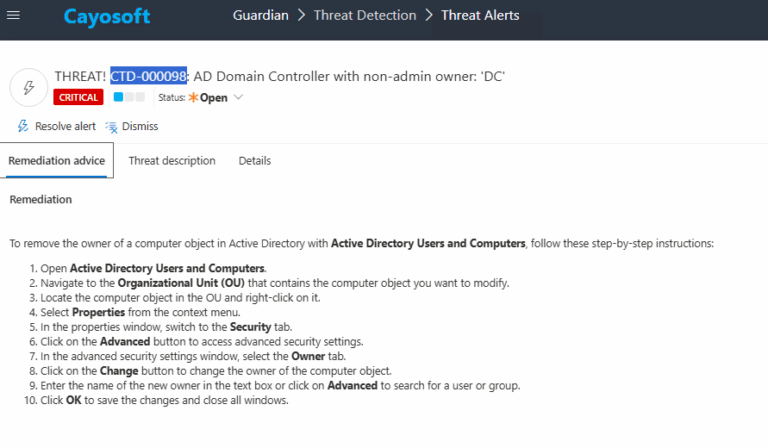
To change the owner of a DC computer object:
1.) Open Active Directory Users and Computers.
2.) Navigate to the Organizational Unit (OU) containing the DC computer object.
3.) Right-click the DC computer and select Properties.
4.) Go to the Security tab.
5.) Click Advanced.
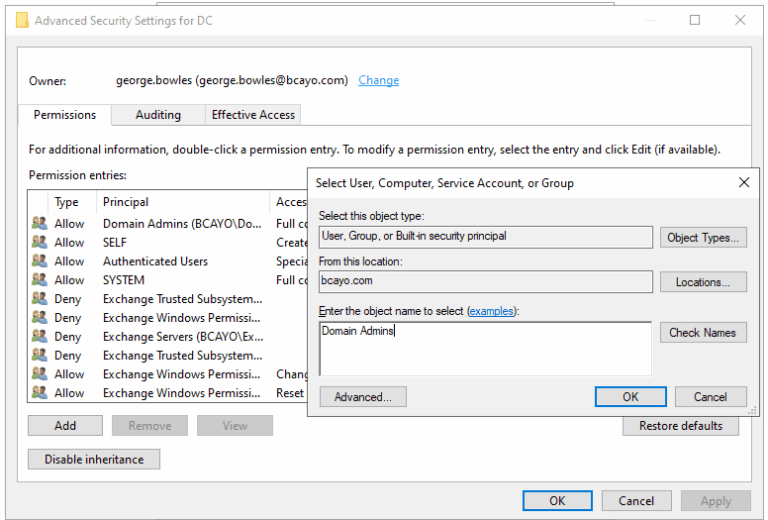
6.) In the Advanced Security Settings window, go to the Owner tab.
7.) Click Change and select m Domain Admins.
8.) Click OK to save and close all dialogs.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on domain controllers not owned by Domain Admins. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
The owner can always change permissions, even if they don’t have current access rights
Through misconfiguration, delegation errors, or intentional insider changes
Yes, ownership is an attribute in AD and can be changed remotely by an authorized account
Final Thought
A non-admin owning a Domain Controller allows the owner to change permissions on the object that can lead to a domain compromise.