AD Domain Controller with Enabled Print Spooler
Cayosoft Threat Definition CTD-000062
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Leaving the Print Spooler service enabled on a Domain Controller exposes credentials to any authenticated user on the network, creating a privilege escalation risk that could lead to full domain compromise.
- Severity: Critical
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Privilege Escalation
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
The Print Spooler service manages print jobs by queuing requests and interacting with printers. While harmless in most contexts, it poses a significant security risk when running on Domain Controllers or AD admin systems. Any authenticated user can remotely connect to the service and request updates on print jobs or trigger notifications using unconstrained delegation.
Because the Print Spooler runs under the SYSTEM account, these actions can expose the Domain Controller’s computer account credentials. Attackers can exploit this to perform lateral movement or escalate privileges within the domain. Microsoft recommends disabling the service on Domain Controllers to remove this attack surface

Real-World Scenario
A low-privileged domain user runs an automated script that connects to the Print Spooler service on a Domain Controller. By exploiting unconstrained delegation, the attacker captures the DC’s computer account credentials, then uses them to request a Kerberos ticket granting full administrative privileges. With this access, they create hidden admin accounts, deploy ransomware, and disable logging. Cayosoft Guardian detects the enabled Print Spooler configuration during scheduled scans, giving defenders time to disable the service before the attacker can act.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
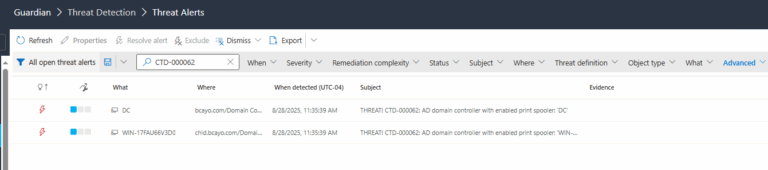
2.) View All Alerts and search for CTD-000062 or AD domain controller with enabled print spooler.
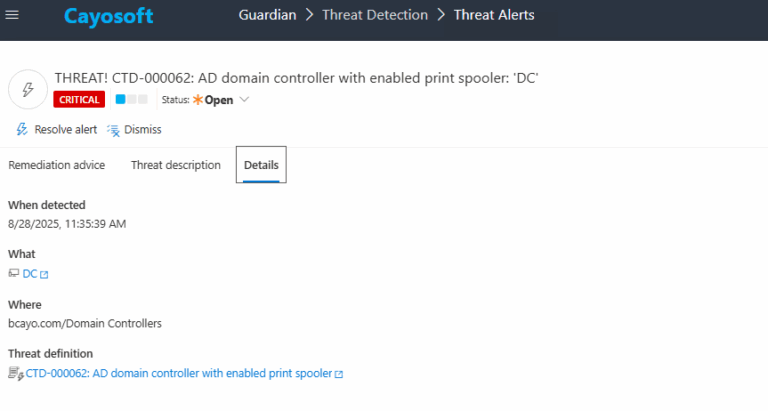
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- What
- When Detected
- Where
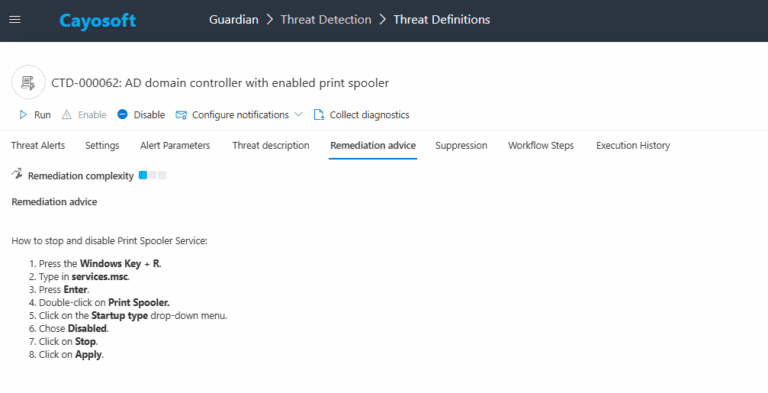
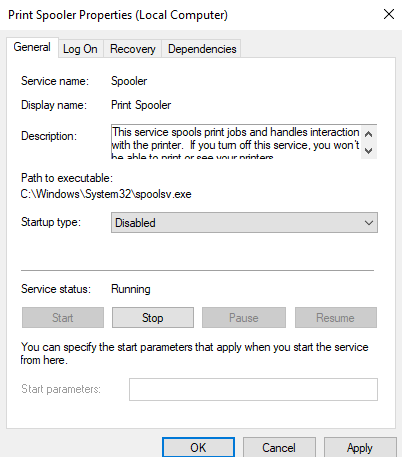
5.) Click Stop.
6.) Click Apply.
Close the Services console.
How to Prevent It
Cayosoft Guardian can proactively detect and alert when the Print Spooler service is enabled on Domain Controllers. To prevent abuse:
- Disable the Print Spooler service on all DCs and AD admin systems using Group Policy.
- Regularly audit services running on privileged systems.
- Restrict administrative access to service configurations.
FAQ
It can expose the DC’s credentials to any authenticated user, enabling privilege escalation attacks
It allows a service to impersonate a user to any other service, which attackers can abuse to gain elevated access
Final Thought
The Print Spooler service is unnecessary on Domain Controllers and represents a high-value privilege escalation target. Disabling it significantly reduces your AD attack surface.