AD domain account with Kerberos pre-authentication disabled
Cayosoft Threat Definition CTD-000052
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Disabling Kerberos pre-authentication exposes the account to offline password attacks (AS-REP roasting). An attacker can request a TGT without prior proof of key ownership and brute-force the returned ciphertext to recover the password.
- Severity: Medium
- Platform: Active Directory
- Category: Account Protection, Kerberos
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Domain Account Monitoring, Application Configuration Hardening
Description
Kerberos pre-authentication requires clients to prove knowledge of the account’s key (password) by encrypting a timestamp that the KDC validates before issuing a ticket. When pre-authentication is disabled, anyone can request an encrypted AS-REP for the account and attempt offline cracking, greatly increasing credential exposure risk.

Real-World Scenario
An attacker finds a service user with Do not require Kerberos preauthentication enabled. From an external system, the attacker requests an AS-REP for that account, captures the encrypted blob, and runs GPU-accelerated cracking to recover the password. The cracked credentials unlock additional systems and stored secrets, enabling lateral movement. Cayosoft Guardian would raise CTD-000052 when any account is detected with pre-authentication disabled, allowing admins to re-enable pre-auth before the account is harvested.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
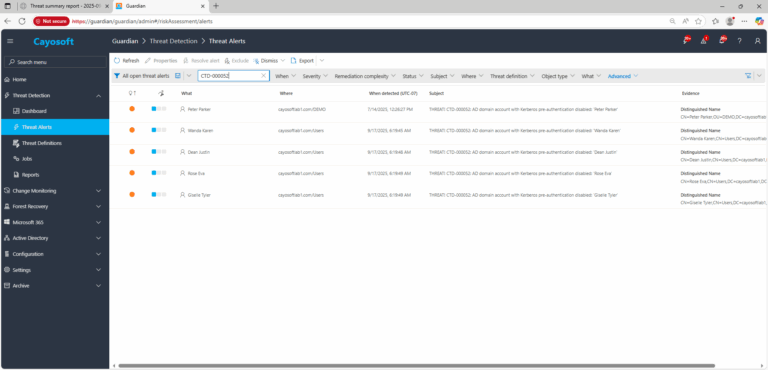
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000052 or AD domain account with Kerberos pre-authentication disabled.
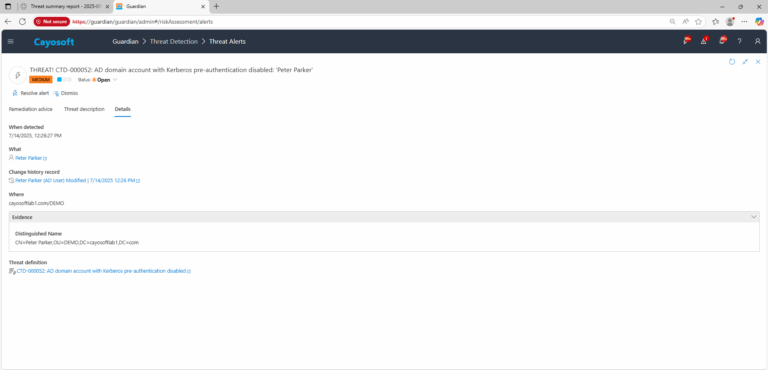
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- Distinguished Name – the exact DN of the affected account.
Remediation Steps
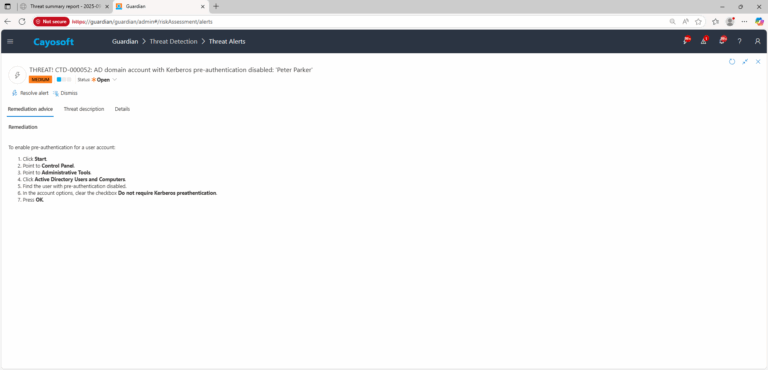
To enable pre-authentication for a user account:
- ) Click Start.
- ) Point to Control Panel.
- ) Point to Administrative Tools.
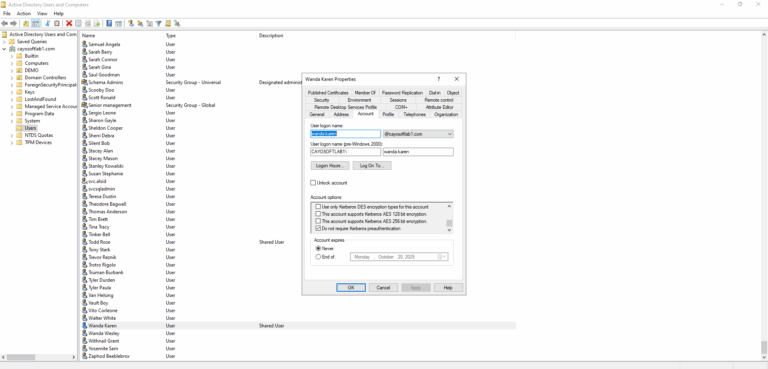
- ) Click Active Directory Users and Computers.
- ) Find the user with pre-authentication disabled.
- ) In the account options, clear the checkbox Do not require Kerberos preathentication.
- ) Press OK.
How to Prevent It
- Enforce Kerberos pre-authentication enabled for all users; create tightly scoped exceptions only when absolutely required.
- Use strong, unique, and regularly rotated passwords; prefer AES-only Kerberos encryption types.
- Continuously monitor for accounts with Do not require Kerberos preauthentication set and remediate immediately.
- Cayosoft Guardian can proactively detect and alert on AD domain account with Kerberos pre-authentication disabled. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
When Kerberos pre-authentication is disabled, anyone can request an encrypted authentication response (AS-REP) for the account without proving they know the password. Attackers can then take this data offline and attempt to crack it using powerful tools, exposing the account’s password and allowing unauthorized access.
Tools like Cayosoft Guardian can detect accounts with this misconfiguration and alert administrators. To remediate, administrators should re-enable Kerberos pre-authentication in the account’s properties within Active Directory Users and Computers (ADUC). After re-enabling, notify account owners, review recent activity for suspicious logins, and rotate the password to reduce potential exposure.
Strong, complex passwords reduce the likelihood of successful brute-force attacks, but they do not eliminate the risk. With pre-authentication disabled, attackers can make unlimited offline attempts to crack the password. The best defense is to re-enable Kerberos pre-authentication and ensure password policies are enforced.
References
- Kerberos pre-authentication — why it should not be disabled (TechNet Wiki): https://social.technet.microsoft.com/wiki/contents/articles/23559.kerberos-pre-authentication-why-it-should-not-be-disabled.aspx
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain account with Kerberos pre-authentication disabled, you reduce attack surfaces and strengthen your organization’s overall security posture.