AD Computer with Suspicious Change of sAMAccountName
Cayosoft Threat Definition CTD-000060
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Changing an AD computer account’s sAMAccountName can be an indicator of an exploit attempt for CVE-2021-42278 and CVE-2021-42287, which allow privilege escalation from a low-privilege user to full domain control.
- Severity: Critical
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Privilege Escalation, Credential Access
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
The Common Vulnerabilities and Exposures (CVEs) CVE-2021-42278 and CVE-2021-42287 are security flaws that can be exploited by a threat actor with access to low-privileged domain credentials. By changing the sAMAccountName of a computer account, the attacker can impersonate a Domain Controller, obtain a Kerberos Service Ticket (TGT), and escalate privileges within the domain.
This privilege escalation can allow complete compromise of the domain controller, enabling the attacker to manage security policies, control access to resources, exfiltrate sensitive data, and spread malware throughout the network. Organizations running unpatched systems are at high risk and should apply Microsoft’s security updates immediately.

Real-World Scenario
An attacker compromises a standard domain user account and identifies an unpatched AD environment vulnerable to CVE-2021-42278/42287. They change a workstation’s sAMAccountName to match a Domain Controller, request a Kerberos ticket, and gain full administrative privileges. With this access, they disable security tools, extract password hashes, and create persistent backdoor accounts. Cayosoft Guardian detects the suspicious sAMAccountName change in real time, enabling rapid rollback before the attacker can fully exploit the vulnerability.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
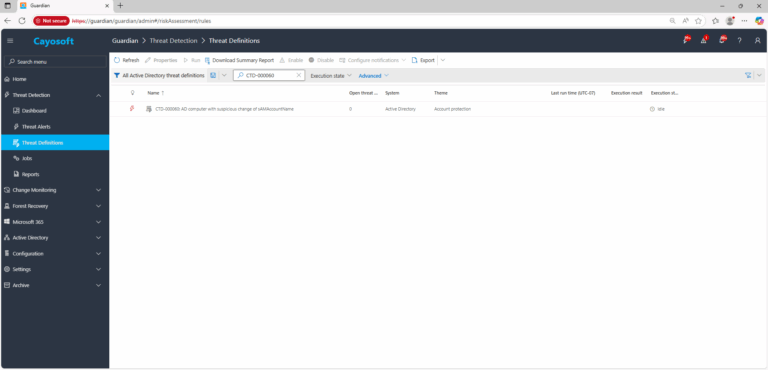
2.) View All Alerts and search for CTD-000060 or AD computer with suspicious change of sAMAccountName.
3.) Open any alert and Click for details (from Raise Threat Alert action).
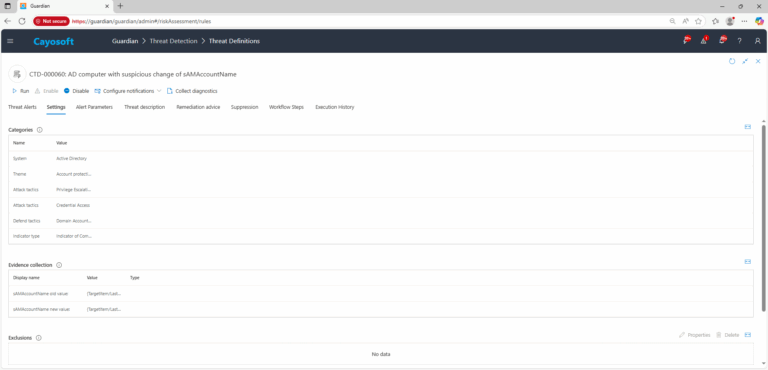
4.) Review Evidence:
- sAMAccountName old value
- sAMAccountName new value
Remediation Steps
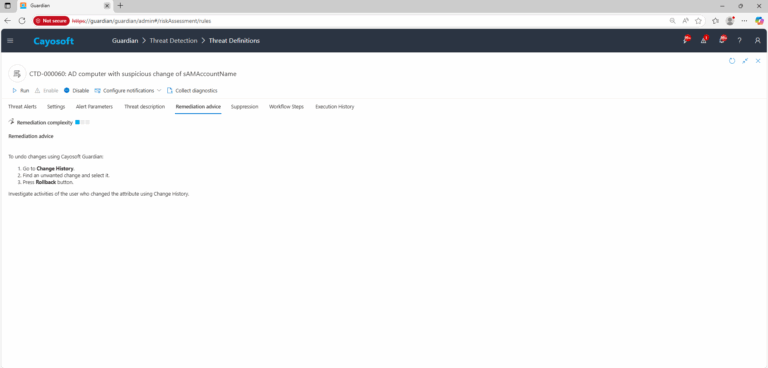
To undo changes using Cayosoft Guardian:
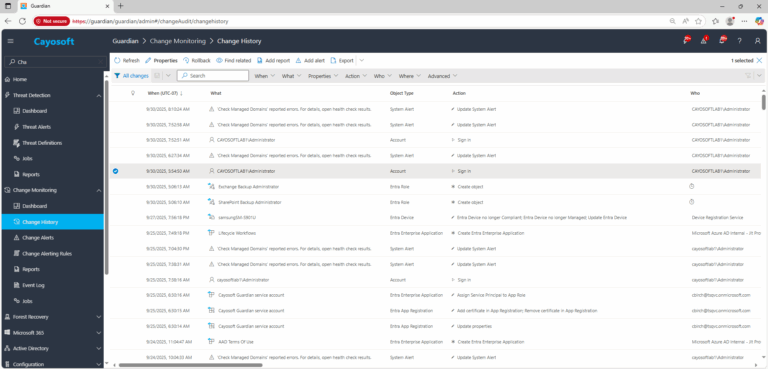
- Go to Change History.
- Find an unwanted change and select it.
- Press Rollback button.
Investigate activities of the user who changed the attribute using Change History.
How to Prevent It
Cayosoft Guardian can detect and alert on suspicious sAMAccountName changes in real time. To prevent exploitation:
- Apply Microsoft’s security patches for CVE-2021-42278 and CVE-2021-42287.
- Restrict who can modify computer account attributes in AD.
- Monitor for unusual Kerberos ticket requests.
FAQ
It may signal an exploitation attempt of CVE-2021-42278 and CVE-2021-42287. These vulnerabilities allow an attacker with low-privileged credentials to escalate rights by impersonating a Domain Controller.
The sAMAccountName is used by Kerberos for authentication. If an attacker modifies a computer account’s name to match a Domain Controller, they can request Kerberos tickets as if they were the DC, ultimately gaining full domain control.
An attacker could compromise the domain controller, disable security controls, extract password hashes, create backdoor accounts, exfiltrate sensitive data, and spread malware across the network.
References
- Microsoft Security Update Guide – CVE-2021-42278
- Microsoft Security Update Guide – CVE-2021-42287
Final Thought
Privilege escalation through sAMAccountName changes is a proven attack method that can lead to full domain compromise. Proactive monitoring, prompt remediation, and timely patching are essential defenses.