Credential stuffing attacks are one of the most common and successful forms of identity-based cyberattacks. That’s why we’re excited to introduce a major enhancement to Cayosoft Guardian Audit & Restore: Password Hash Analysis with Breached Password Detection. This feature helps security teams identify and address compromised credentials inside Active Directory before attackers exploit them.
How Cayosoft Guardian Audit & Restore Detects Breached Passwords
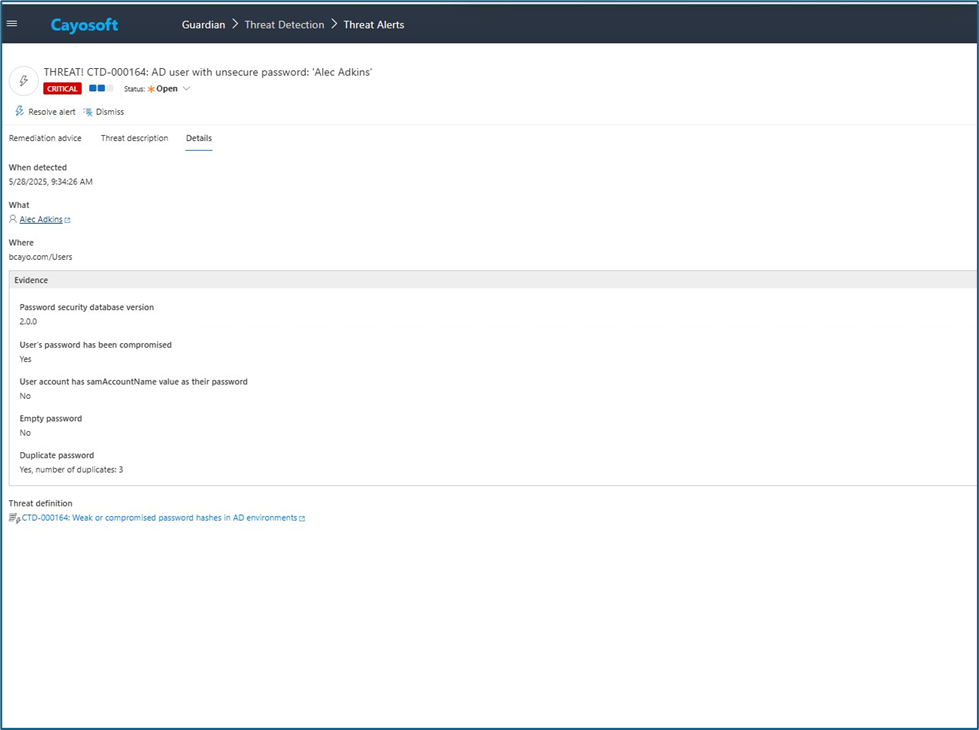 The new Password Hash Analysis feature in Cayosoft Guardian Audit & Restore compares Active Directory password hashes against a dynamic list of known breached credentials without decrypting them.
The new Password Hash Analysis feature in Cayosoft Guardian Audit & Restore compares Active Directory password hashes against a dynamic list of known breached credentials without decrypting them.
With this feature, security teams can:
- Identify compromised passwords in Active Directory
- Detect reused credentials in user and service accounts
- Detect blank and weak passwords
- Gain visibility into password hygiene and credential risks across hybrid identity systems
This allows for proactive Active Directory security, helping teams prevent attacks tied to password reuse and credential leaks.
Why is Password Hash Analysis important?
MFA Doesn’t Stop Credential Stuffing-Especially for Service Accounts
Many organizations rely on Multi-Factor Authentication (MFA) to protect user identities. But MFA isn’t a complete defense, especially when it comes to service accounts. These non-human accounts:
- Usually don’t support MFA
- Often use static passwords that go unchanged for years
- Frequently hold elevated or domain-level privileges
- Are excluded from regular security reviews
- Are therefore ideal targets for credential stuffing attacks and a major blind spot in hybrid Active Directory environments.
Strengthen Your Hybrid Active Directory Security with Cayosoft Guardian Audit & Restore™
Monitor and protect your Active Directory with real-time change tracking and instant recovery. Enhance your password policies and safeguard privileged accounts effectively.
Real-World Breaches Power Credential Stuffing Campaigns
Credential stuffing relies on real usernames and passwords exposed in previous data breaches. Attackers compile massive lists and automate login attempts across platforms like Microsoft 365, VPNs, and Active Directory.
Recent breach data highlights the scale of the problem:
- RockYou2024: The largest password leak in history. This file includes 9.9 billion unique passwords, aggregated from over 4,000 data breaches.
- 23andMe Breach (2023): Attackers used credentials from earlier breaches to take over 14,000 accounts accessing personal and genetic data for 6.9 million users through credential stuffing.
- Cybernews Analysis (2024): More than 19 billion passwords analyzed. Only 6% were unique—the rest were reused. The password “123456” appeared over 338 million times.
With usernames often tied to Microsoft 365 email addresses, which are publicly available on LinkedIn and company websites, attackers don’t need to guess, only test.
Implement Fine-Grained Password Policies.
Discover how to apply fine-grained password policies to secure privileged accounts in Active Directory environments.
Strengthen Your AD Security Against Credential-Based Threats
Credential stuffing doesn’t require sophisticated malware, it only needs reused credentials. MFA doesn’t protect service accounts. Traditional monitoring doesn’t catch password reuse. And breach data continues to grow every day.
With Cayosoft Guardian Audit & Restore’s new breached password detection, you gain real-time insights into password risk and Active Directory exposure across both human and non-human accounts.
Don’t wait for a reused password to cause an incident. Schedule a demo to learn more about how Cayosoft can strengthen your hybrid identity defense now.
FAQs
A password hash is an encrypted representation of a password, used to verify a user’s identity without storing the actual password. By comparing password hashes instead of plaintext passwords, systems can detect compromised or reused credentials securely—without exposing sensitive data.
Cayosoft Guardian Audit & Restore compares password hashes from Active Directory against a dynamic list of known breached credentials. This allows it to detect reused, weak, or compromised passwords—without decrypting them—helping to maintain secure authentication in hybrid environments.
Yes, password hash analysis is especially useful for securing service accounts, which often use static passwords and don’t support MFA. By identifying weak or reused password hashes, Cayosoft Guardian Audit & Restore can flag credential risks that traditional monitoring tools may miss.security controls aren’t impeding business functions.
Absolutely. Cayosoft Guardian never decrypts or exposes actual passwords. Instead, it securely compares password hashes using industry-standard cryptographic methods, making it a compliant and non-invasive way to detect credential exposure.
Traditional audits often rely on password policies or manual reviews. Password hash analysis, by contrast, enables automated, real-time detection of breached or weak credentials—making it far more effective for identifying security threats before they’re exploited.