Dangerous ACLs Expose GPOs Applied to Privileged Group Members
Cayosoft Threat Definition CTD-000151
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Misconfigured Access Control Lists (ACLs) on Group Policy Objects (GPOs) linked to privileged groups can allow attackers to inject or modify policy settings that execute code on privileged user workstations and servers. This can lead to privilege escalation and full domain compromise.
- Severity: Critical
- Platform: Active Directory
- Category: Privileged Access Management
- MITRE ATT&CK Tactics: Execution, Privilege Escalation
- MITRE D3FEND Tactics: Credential Hardening
Description
GPOs linked to privileged groups (such as DnsAdmins, Enterprise Domain Controllers, or Enterprise Read Only Domain Controllers) are highly sensitive because they often apply to accounts with elevated privileges.
If the GPO’s permissions allow unauthorized principals to modify it, attackers can insert malicious scripts, registry changes, or scheduled tasks.
When the GPO refreshes on privileged systems, the attacker’s payload executes with elevated rights.

Real-World Scenario
An attacker gains write access to a GPO applied to Enterprise Admins. They add a startup script that creates a new domain admin account.
When any privileged member logs in to a workstation or domain controller, the script runs and silently grants the attacker full domain control — without triggering typical login alerts.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
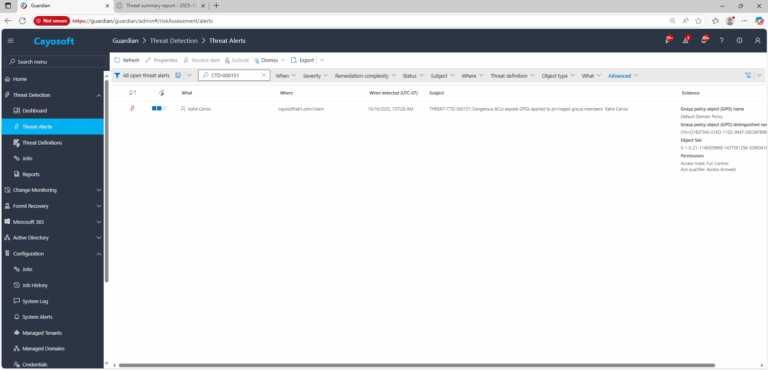
2.) Search for CTD-000151 or Dangerous ACLs expose GPOs applied to privileged group members.
3.) Open any alert and Click for details (from Raise Threat Alert action).
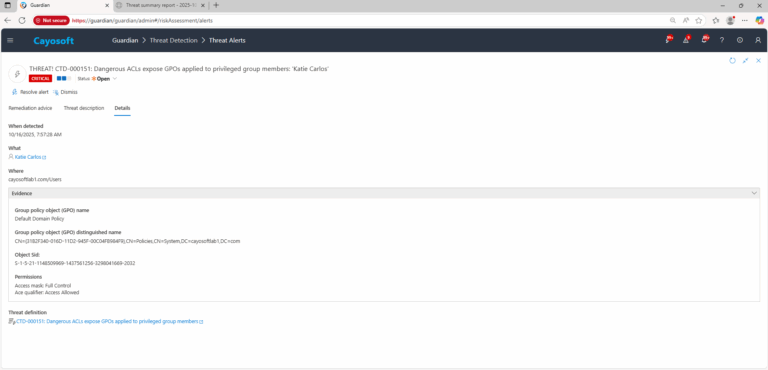
4.) For each alert, check the Evidence:
- GPO Name
- GPO Distinguished Name (DN)
- Object SID
- Permissions granted
Cayosoft Guardian uses the adminCount property to detect accounts marked as privileged and compares them against the privilegedAccounts list.
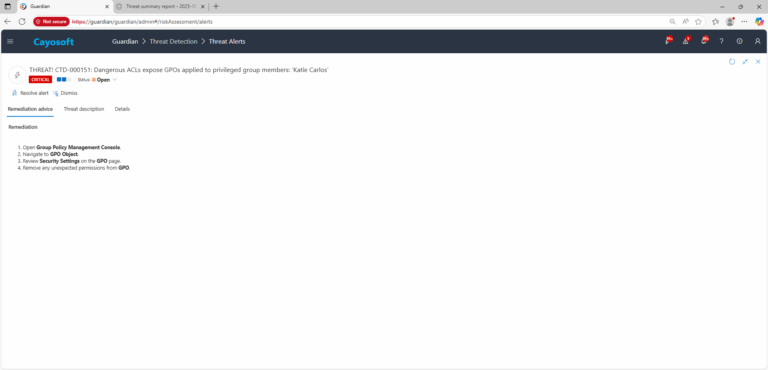
How to Prevent It
- Limit GPO modification rights to a minimal, well-audited group.
- Regularly audit GPO ACLs for privileged-linked policies.
- Enable Cayosoft Guardian continuous monitoring with alert suppression keys to avoid duplicate noise while tracking ongoing incidents.
FAQ
Because misconfigured permissions on Group Policy Objects (GPOs) linked to privileged accounts can allow attackers to inject malicious settings or scripts. When these GPOs apply to admin-level users or servers, the attacker’s payload executes with elevated privileges, potentially leading to full domain compromise.
In the Cayosoft Guardian Threat Detection Dashboard, search for CTD-000151 or the issue name. Review the evidence section, which lists the affected GPO name, distinguished name, object SID, and granted permissions. This helps identify GPOs where unauthorized principals have write or modify access.
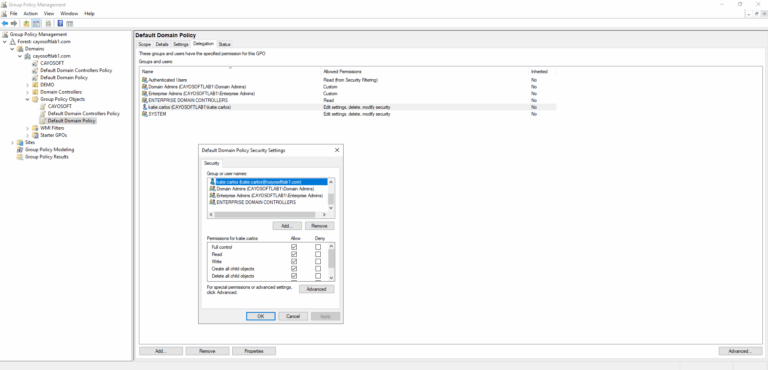
Open the Group Policy Management Console, locate the flagged GPO, and review its Delegation and Security tabs. Remove any unauthorized users or groups with Write, Modify, or Full Control rights. Ensure that only approved administrative groups retain modification permissions, and regularly audit all privileged GPOs.
Final Thought
A single misconfigured GPO on a privileged group is like leaving the keys to your kingdom on the doormat. By locking down ACLs and continuously monitoring with tools like Cayosoft Guardian, you prevent attackers from silently weaponizing policy infrastructure against your highest-value accounts.