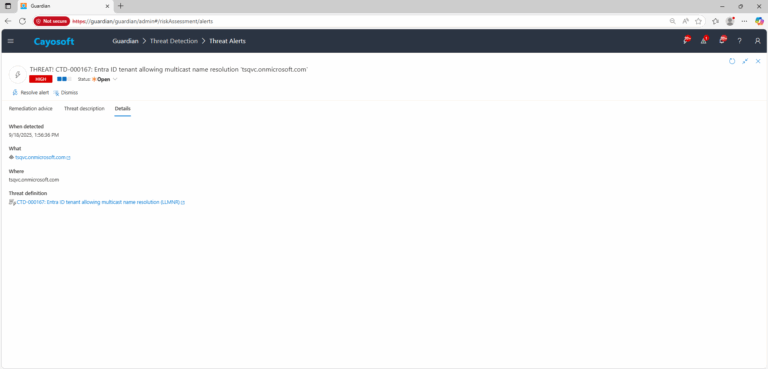
Entra ID tenant allowing multicast name resolution (LLMNR)
Cayosoft Threat Definition CTD-000167
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Multicast Name Resolution (LLMNR) is a legacy protocol that enables spoofing and credential-harvesting (e.g., responder/relay) when DNS fails, exposing users to NetNTLM hash capture on untrusted networks.
- Severity: High
- Platform: Entra ID
- Category: Intune, Infrastructure
- MITRE ATT&CK Tactics: Credential Access, Collection
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Multicast Name Resolution (LLMNR) is a legacy protocol for name resolution in networks without DNS servers. In an Active Directory domain, LLMNR can expose the environment to spoofing and credential-harvesting attacks, such as responder attacks. Attackers can intercept and manipulate LLMNR requests to gain user credentials or redirect traffic.

Real-World Scenario
An attacker on a conference Wi-Fi runs a rogue LLMNR responder. A user mistypes a server name; Windows falls back to LLMNR and queries the subnet. The attacker replies as the “server,” triggers an authentication attempt, and captures the user’s NetNTLMv2 hash. The hash is cracked offline or relayed to an SMB/HTTP service to obtain session tokens, leading to data access and lateral movement. Cayosoft Guardian identifies that the tenant lacks a control to disable LLMNR via Intune and raises an alert before more devices are exposed.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
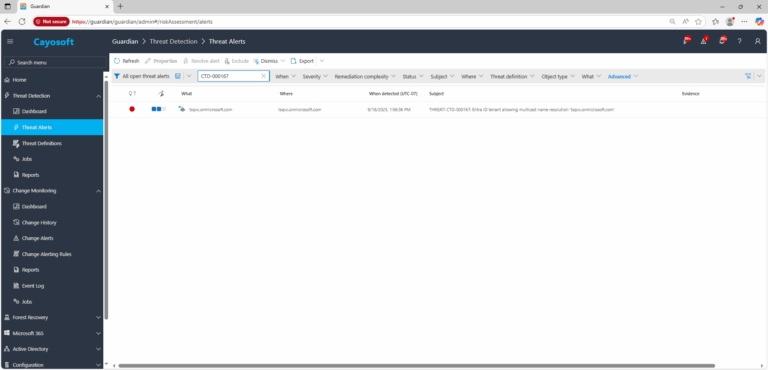
2.) View All Alerts and search for CTD-000167 or Entra ID tenant allowing multicast name resolution (LLMNR).
3.) Open any alert and Click for details (from Raise Threat Alert action).
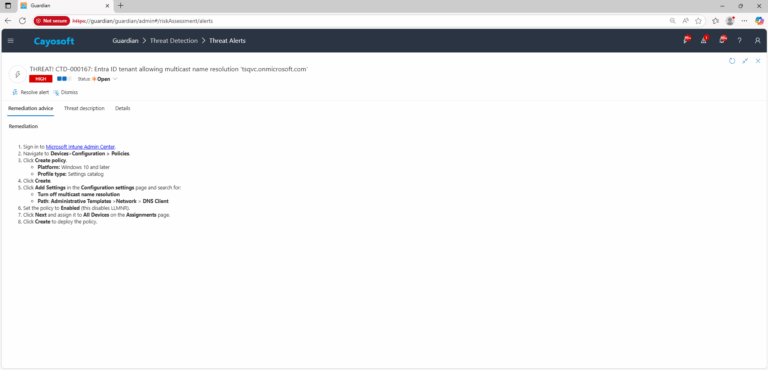
Remediation Steps
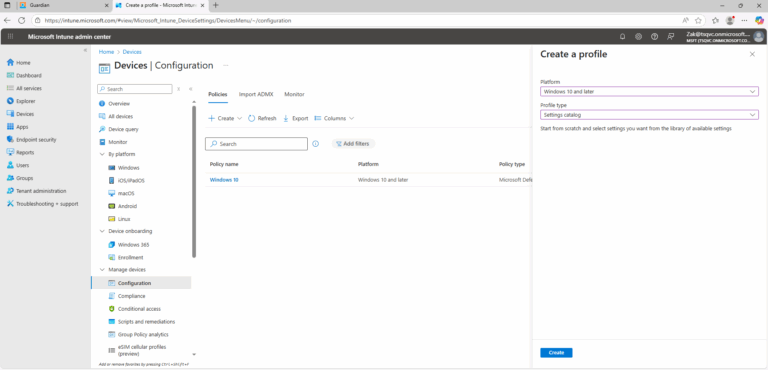
- ) Sign in to Microsoft Intune Admin Center.
- ) Navigate to Devices>Configuration > Policies.
- ) Click Create policy.
- Platform: Windows 10 and later
- Profile type: Settings catalog
- ) Click Create.
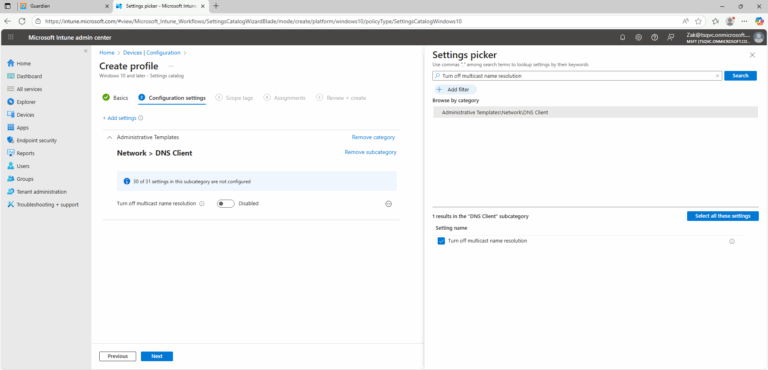
5. ) Click Add Settings in the Configuration settings page and search for:
- Turn off multicast name resolution
- Path: Administrative Templates >Network > DNS Client
6. ) Set the policy to Enabled (this disables LLMNR).
7. ) Click Next and assign it to All Devices on the Assignments page.
8. ) Click Create to deploy the policy.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on LLMNR allowed in the tenant. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
No. Modern domain environments rely on DNS for name resolution. LLMNR is an insecure legacy fallback used only when DNS fails. Disabling it removes risk without affecting normal name resolution.
Yes, if there are no legacy systems depending on it. Disabling NBNS further reduces the spoofing and relay attack surface.
Check that the registry value HKLM\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient\EnableMulticast = 0 is set, and confirm no LLMNR (UDP/5355) traffic appears in a packet capture during failed DNS lookups.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like allowing LLMNR, you reduce attack surfaces and strengthen your organization’s overall security posture.