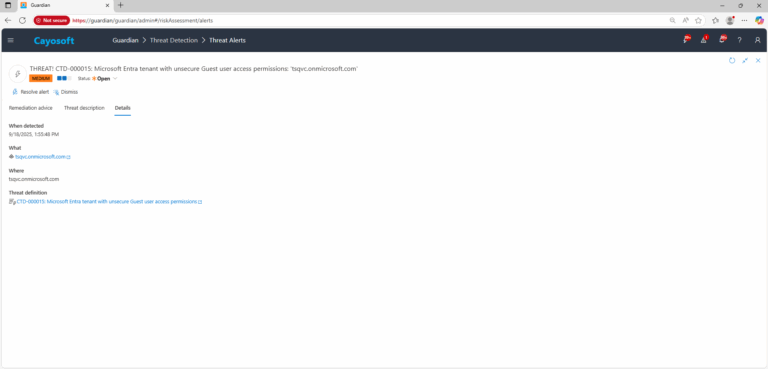
Microsoft Entra tenant with unsecure Guest user access permissions
Cayosoft Threat Definition CTD-000015
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A Microsoft Entra ID is configured with unsecure Guest user access permissions. With permissive defaults, a threat actor can enumerate users and groups (e.g., via AADInternals) with minimal audit visibility, aiding targeted attacks and data exposure.
- Severity: Medium
- Platform: Entra ID
- Category: Infrastructure, Guest management, Tenant-wide
- MITRE ATT&CK Tactics: Discovery
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
A Microsoft Entra ID is configured with unsecure Guest user access permissions. With the current setting value, a threat actor might enumerate groups and users using a tool such as AADInternals. The API calls to Microsoft Entra ID are not logged and therefore the actions of a threat actor cannot be easily detected.

Real-World Scenario
An external collaborator’s guest account is phished. Because tenant guest access is overly permissive, the attacker uses enumeration calls to map high-value groups, shared Teams, and target owners. The attacker pivots to request additional access, craft convincing spear-phish to group owners, and harvest files exposed to “All guests.” Since many enumeration calls aren’t centrally logged, the activity blends into normal collaboration. Cayosoft Guardian flags CTD-000015 so admins can lock down guest access before the mapping turns into compromise.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
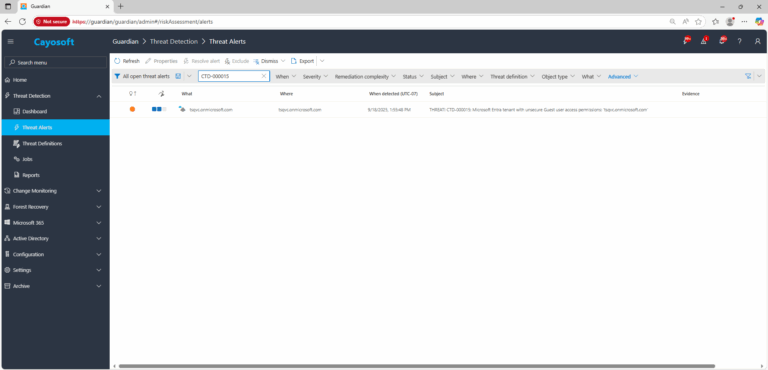
2.) View All Alerts and search for CTD-000015 or Microsoft Entra tenant with unsecure Guest user access permissions.
3.) Open any alert and Click for details (from Raise Threat Alert action).
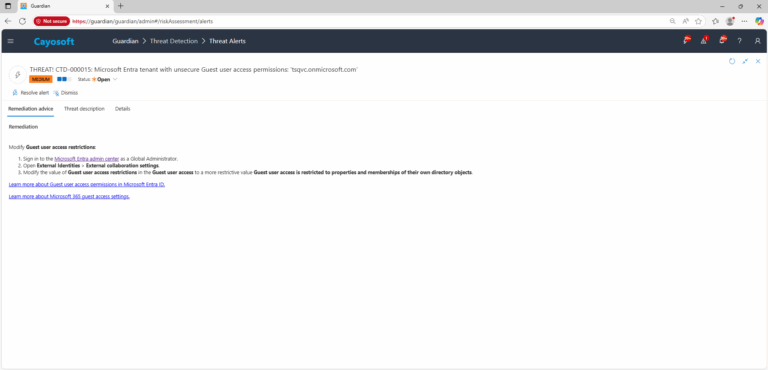
Remediation Steps
Modify Guest user access restrictions:
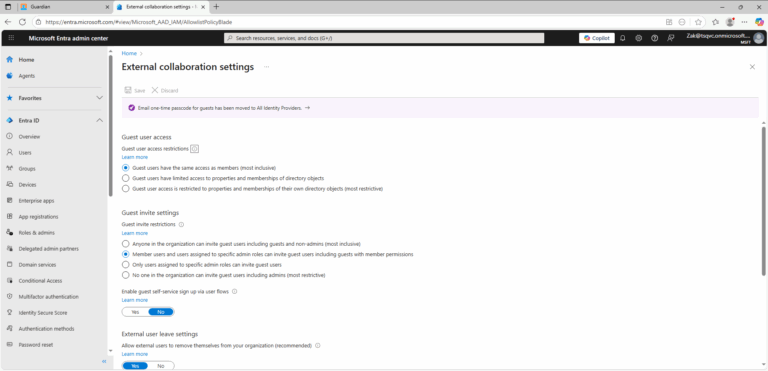
- ) Sign in to the Microsoft Entra admin center as a Global Administrator.
- ) Open External Identities > External collaboration settings.
- ) Modify the value of Guest user access restrictions in the Guest user access to a more restrictive value Guest user access is restricted to properties and memberships of their own directory objects.
Learn more about Guest user access permissions in Microsoft Entra ID.
How to Prevent It
- Enforce the most restrictive Guest user access setting across the tenant.
- Regularly review External collaboration settings and Teams/SharePoint guest sharing policies.
- Minimize tenant-wide groups/resources with guest visibility; scope sharing only to required teams or sites.
Monitor for drift with Cayosoft Guardian and audit new guest invitations and high-risk group memberships.
FAQ
It restricts guest visibility so guests can only see properties and memberships of their own directory objects, reducing tenant-wide enumeration risk.
In Entra admin center → External Identities → External collaboration settings for directory-level behavior, and in Microsoft 365 admin/SharePoint/Teams for workload-specific guest sharing.
Enforce the most restrictive guest user access setting tenant-wide, regularly review external collaboration settings, and minimize groups/resources with guest visibility.
References
- https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/users-default-permissions
- https://docs.microsoft.com/en-us/microsoft-365/solutions/microsoft-365-guest-settings?view=o365-worldwide
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra tenant with unsecure Guest user access permissions, you reduce attack surfaces and strengthen your organization’s overall security posture.