AD User with Compromised Password
Cayosoft Threat Definition CTD-000178
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A compromised password — one that appears in known data breaches — can be used by attackers to gain unauthorized access. These credentials are often sold, shared, or used in automated credential-stuffing attacks, putting all linked systems and accounts at risk.
- Severity: Critical
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: D3-PR (Password Rotation)
Description
Passwords that appear in known data breaches are considered compromised and highly vulnerable to exploitation.
Attackers often reuse leaked credentials in automated attacks across multiple environments.
Cayosoft Guardian detects such risks by comparing password hashes against a curated database of breached credentials sourced from Have I Been Pwned.
This database is first filtered in the Cayosoft cloud to keep only the most frequently used compromised passwords.
Your Cayosoft Guardian server then downloads this filtered list and performs local hash comparisons directly on your domain controllers.
Cayosoft Guardian does not store or transmit password hashes. All comparison operations happen within your secure environment, ensuring that hashes are never exposed to the internet or external systems.

Real-World Scenario
An employee reuses their personal email password — which was leaked in a recent data breach — for their corporate AD account.
An attacker obtains the breached password and attempts to log in to corporate resources.
Because the account uses the same password, the login succeeds, granting the attacker immediate internal access.
They quickly escalate privileges and access sensitive files before security teams notice unusual behavior.
Cayosoft Guardian would have flagged the account as having a breached password during its scheduled scan, allowing the password to be reset before compromise.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
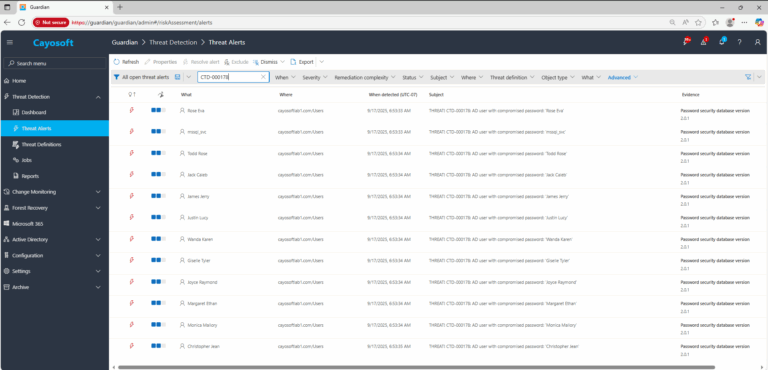
2.) View All Alerts and search for CTD-000178 or AD user with compromised password.
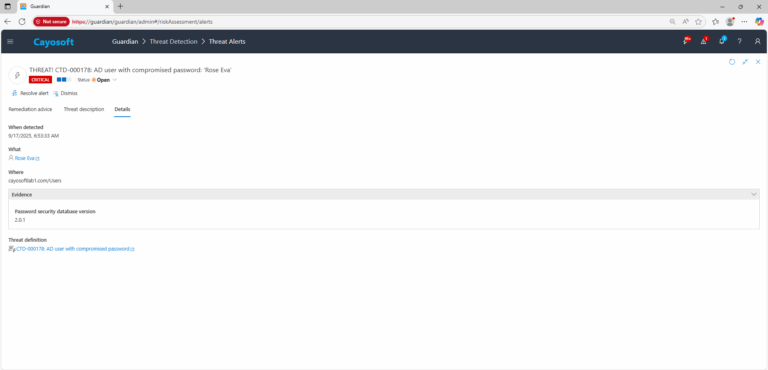
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- Password security database version
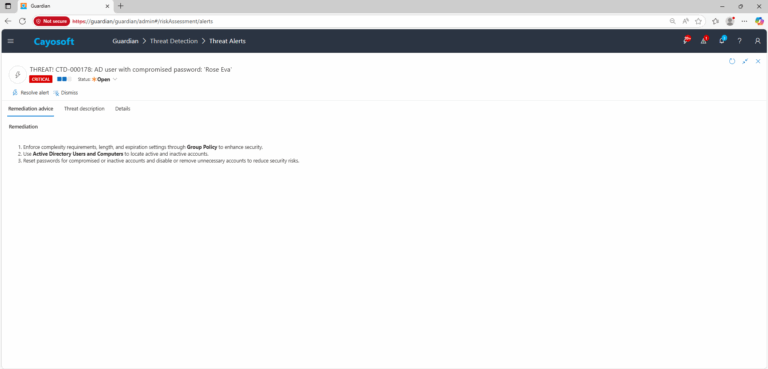
Remediation Steps
- ) Notify and contact user and inform them of the password vulnerability and have them either manually reset the password or use following steps
- ) Enforce complexity requirements, length, and expiration settings through Group Policy to enhance security.
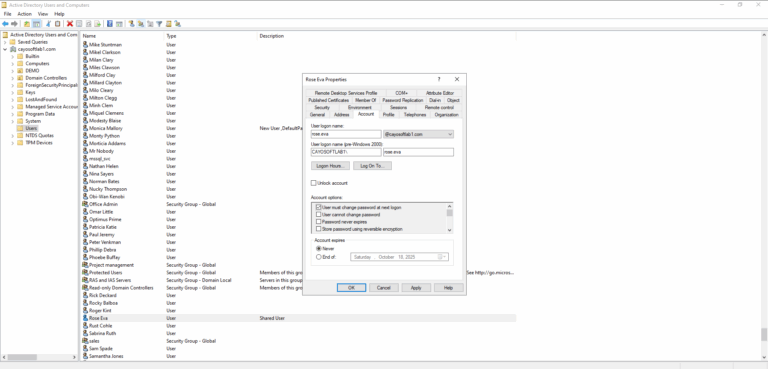
- ) Use Active Directory Users and Computers to locate active and inactive accounts.
- ) Reset passwords for compromised or inactive accounts and disable or remove unnecessary accounts to reduce security risks.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD users with compromised passwords.
By continuously monitoring account credentials against known breach data, it helps enforce password rotation and complexity requirements before attackers can exploit them.
FAQ
MFA only protects services where it is enforced. If the same password is reused in systems without MFA, attackers can leverage it for lateral movement or integrated service attacks. MFA reduces risk but does not eliminate the need for strong and unique passwords.
Reset the password immediately, enforce stronger complexity rules, audit logs for suspicious logons, and consider temporarily restricting or isolating the account until investigation is complete.
Enforce regular password screening against breach lists, prevent password reuse with filters, deploy controls that block weak or compromised passwords during creation, and strengthen user awareness training to reduce risky behavior.
Final Thought
Proactively detecting and remediating compromised passwords greatly reduces the likelihood of credential-based attacks. Regular rotation, complexity enforcement, and breach monitoring are essential for defending Active Directory accounts.