Regular AD user account with permissions to modify DNS server objects
Cayosoft Threat Definition CTD-000080
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A regular user who is a member of DNSAdmins or has write permissions on DNS server objects can manipulate the DNS service and escalate privileges to Local System. An attacker can plant a malicious DLL and trigger a service restart to execute code with SYSTEM rights, gaining control paths into Active Directory.
- Severity: High
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Execution, Privilege Escalation
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
A regular user with membership in DNSAdmins or delegated write access on DNS server objects represents a high-risk misconfiguration. A threat actor may inject a malicious DLL into the DNS service and gain SYSTEM-level execution upon restart.
Note: Cayosoft Guardian evaluates both direct and nested group memberships. “Privileged users” in Active Directory are those with adminCount=1, an attribute used to protect members of administrative groups (Microsoft Open Specs). Guidance on AdminSDHolder/SDProp behavior and persistence is available in Microsoft Community Hub.

Real-World Scenario
A helpdesk user is temporarily delegated DNS change rights during a migration and is later added to DNSAdmins for “convenience.” Weeks later, the user uploads a crafted DLL and sets the DNS service parameter to load it. During a routine patch window, DNS restarts and the DLL runs as SYSTEM, allowing the attacker to create shadow admin accounts and modify GPOs while blending in with maintenance activity. The attacker avoids obvious detection by using scheduled restarts and standard admin tools. Cayosoft Guardian would detect the risky group membership or write permissions on DNS objects and raise an alert before the restart-triggered escalation
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
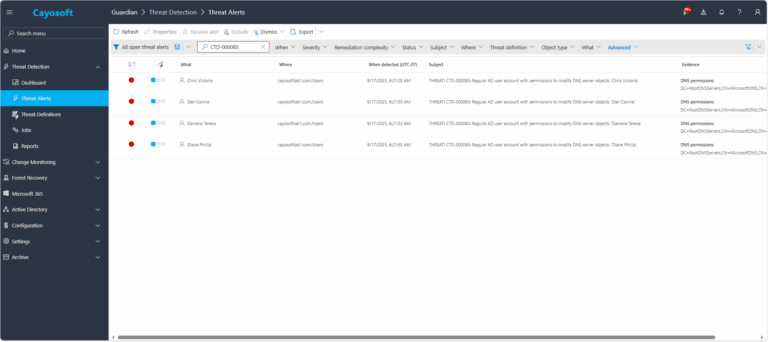
2.) View All Alerts and search for CTD-000080 or “Regular AD user account with permissions to modify DNS server objects.
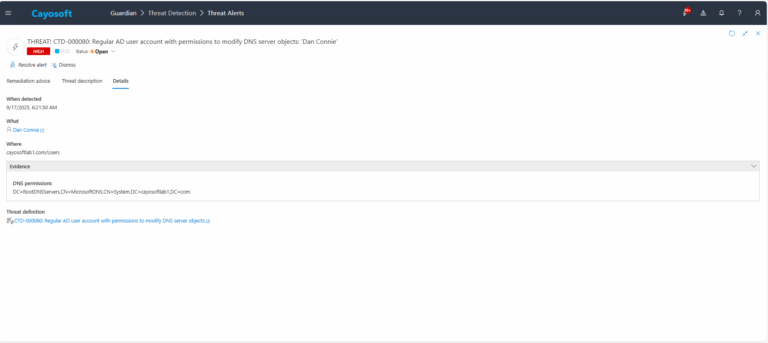
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- DNS permissions
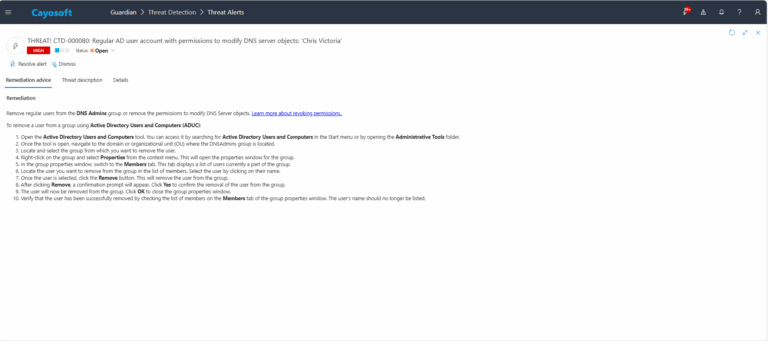
Remediation Steps
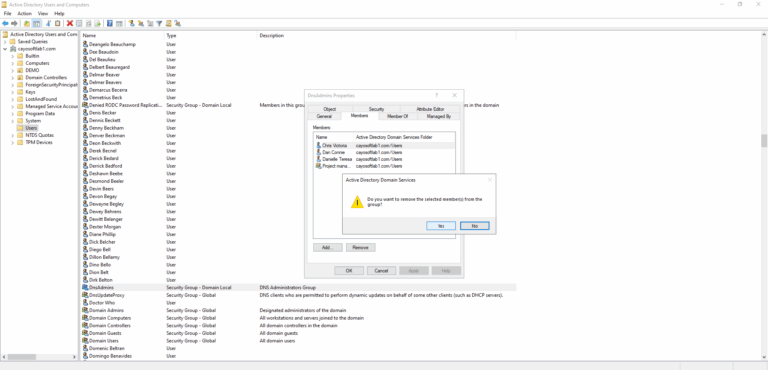
1.) Open the Active Directory Users and Computers tool. You can access it by searching for Active Directory Users and Computers in the Start menu or by opening the Administrative Tools folder.
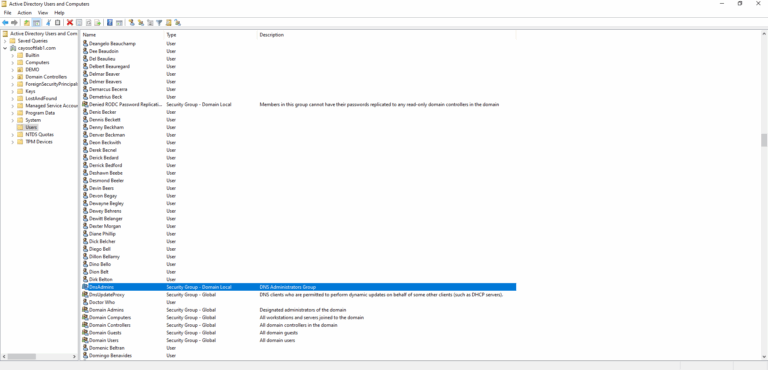
2.) Once the tool is open, navigate to the domain or organizational unit (OU) where the DNSAdmins group is located.
3.) Locate and select the group from which you want to remove the user.
4.) Right-click on the group and select Properties from the context menu. This will open the properties window for the group.
5.) In the group properties window, switch to the Members tab. This tab displays a list of users currently a part of the group.
6.) Locate the user you want to remove from the group in the list of members. Select the user by clicking on their name.
7.) Once the user is selected, click the Remove button. This will remove the user from the group.
8.) After clicking Remove, a confirmation prompt will appear. Click Yes to confirm the removal of the user from the group.
9.) The user will now be removed from the group. Click OK to close the group properties window.
10.) Verify that the user has been successfully removed by checking the list of members on the Members tab of the group properties window. The user’s name should no longer be listed.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Regular AD user account with permissions to modify DNS server objects. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
DNSAdmins can configure the DNS service to load arbitrary DLLs, leading to SYSTEM-level execution and potential domain compromise.
Confirm group membership, audit ACEs on DNS containers/zones, and verify no service parameters (e.g., DLL paths) were modified.
AdminSDHolder/SDProp periodically stamp protected ACLs onto admin accounts. If a user is or was protected, permissions may be reapplied; review the AdminSDHolder model and timing in this Microsoft article.
Yes. Prefer granular delegation on specific DNS zones/records with least-privilege write rights instead of broad DNSAdmins membership.
References
- Active Directory – View or delete delegated permissions: https://social.technet.microsoft.com/wiki/contents/articles/6477.active-directory-how-to-view-or-delete-delegated-permissions.aspx
- adminCount attribute (Microsoft Open Specs): https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- AdminSDHolder and SDProp (Microsoft Community Hub): https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Regular AD user account with permissions to modify DNS server objects, you reduce attack surfaces and strengthen your organization’s overall security posture.