AD Computer Account That Is a Member of Privileged Groups
Cayosoft Threat Definition CTD-000104
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
If an Active Directory computer account is a member of privileged groups, it can be used by an attacker to gain administrative control across the domain.
This includes both direct membership and nested group membership
- Severity: Critical
- Platform: Active Directory
- Category: Account Protection, Privileged Access Management
- MITRE ATT&CK Tactics: Privilege Escalation, Persistence, Lateral Movement
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
Computer accounts in AD are often granted rights based on their group membership. If such an account is added to a privileged group (e.g., Domain Admins, Enterprise Admins, Administrators), it inherits powerful rights that can be abused for:
- Persistence – Keeping administrative access even if user credentials are changed or revoked.
- Lateral Movement – Using elevated privileges to pivot into other systems.
- Data Exfiltration – Accessing sensitive files and directories from high-value systems.
Cayosoft Guardian identifies these risks by checking both direct and indirect (nested) group membership and highlighting accounts with adminCount=1 (the AD marker for protected administrative accounts).

Real-World Scenario
An attacker compromises a workstation computer account that is accidentally added to the “Domain Admins” group.
From there, they can use tools like Pass-the-Hash or Kerberos ticket attacks to impersonate privileged users, deploy ransomware, and disable defenses across the environment.
Catch GPO Tampering & Role Abuse Live with Cayosoft Guardian
Detect mass group changes, risky roles, and policy edits—then roll them back.
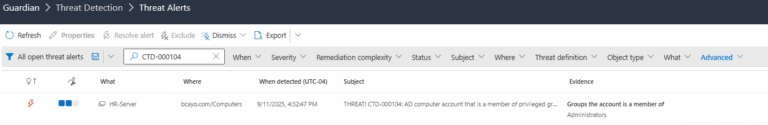
2.) View All Alerts and search for CTD-000104 or AD computer account that is a member of privileged groups.
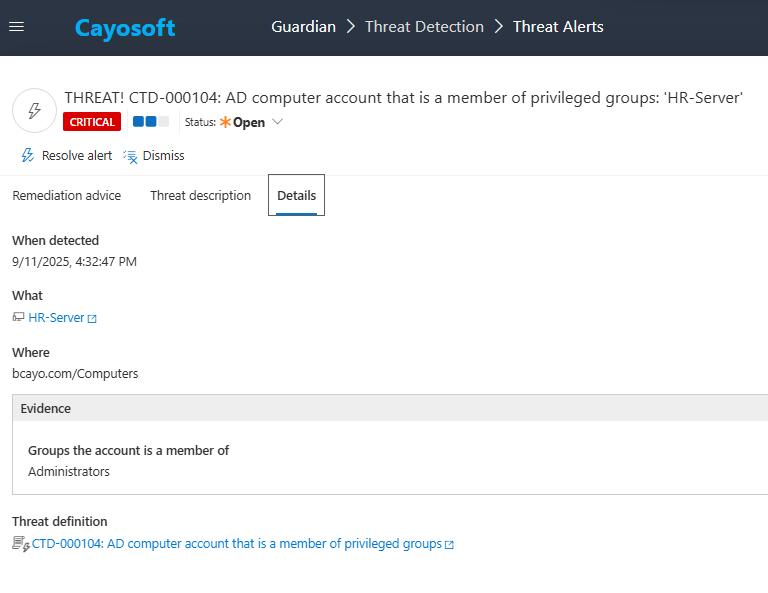
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- Groups the Account is a member of
Remediation Steps
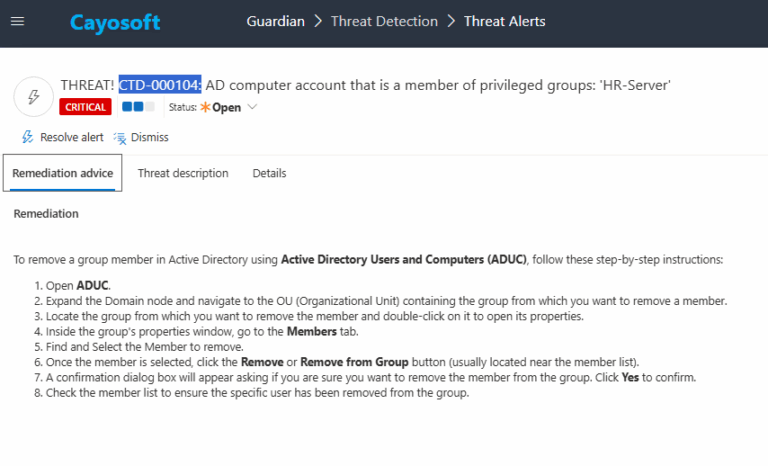
To remove a computer account from a privileged group using Active Directory Users and Computers (ADUC):
1.) Open ADUC.
2.) Expand the Domain node and navigate to the OU containing the group.
3.) Double-click the group name to open Properties.
4.) Go to the Members tab.
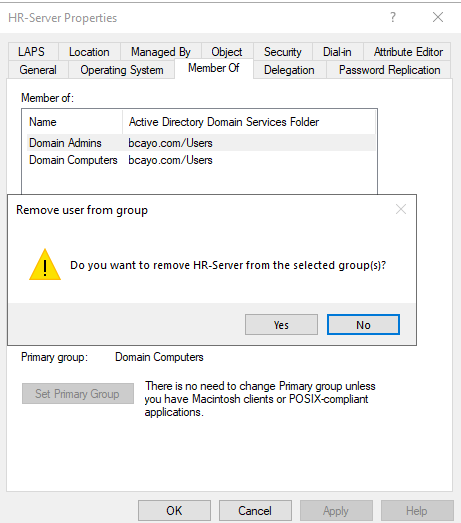
5.) Select the computer account you want to remove.
6.) Click Remove (or Remove from Group).
7.) Confirm the removal by clicking Yes.
8.) Verify that the computer is no longer listed as a group member.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on computer accounts that are members or privileged groups. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Privileged group membership grants elevated access to all processes running on the system. If the computer is compromised, attackers can leverage these privileges to move laterally, escalate access, or take control of domain resources.
• Immediately isolate the affected system from the network
• Revoke or reset credentials and group memberships
• Conduct a full forensic investigation
• Review logs for lateral movement or privilege escalation
• Reassess privilege assignment policies to prevent recurrence
Final Thought
A computer account with privileged group membership effectively grants elevated access to all processes running on that system. If compromised, it provides an attacker with broad control—not merely access to the network, but the ability to influence or command critical domain resources.