AD domain account with unconstrained delegation
Cayosoft Threat Definition CTD-000049
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An Active Directory account with unconstrained delegation can impersonate any authenticated user and access any service in the domain, creating a high-risk opportunity for attackers to escalate privileges and move laterally without restriction.
- Severity: Critical
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Credential Transmission Scoping
Description
Unconstrained Kerberos delegation allows a service account to receive user credentials and delegate them to any service in Active Directory. Modern applications may use this to forward credentials from authenticated users to other services like SMTP, file, database, or additional web servers. Because the delegation is “unconstrained,” a compromised account can impersonate high-privilege users (including domain admins), perform unauthorized actions such as modifying enterprise admin groups, extract sensitive account hashes (e.g., KRBTGT), or access confidential files.

Real-World Scenario
A threat actor gains control of a web server service account configured for unconstrained delegation. When a domain administrator logs into the web application, the attacker captures the delegated Kerberos ticket. Using this, they impersonate the admin and connect to a domain controller, adding their own account to the Enterprise Admins group.
They then export the KRBTGT hash to generate Golden Tickets for persistent domain access. Cayosoft Guardian could have detected the misconfiguration during continuous monitoring, generating an alert before the account was exploited.
Fix Group/Policy Mistakes in Seconds with Cayosoft Guardian
Reverse misconfigurations instantly—no scripts, no downtime.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
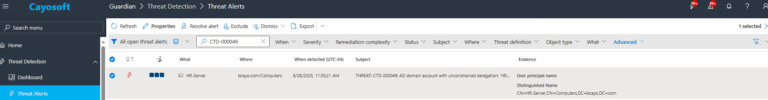
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000049 or AD domain account with unconstrained delegation
3.) Open the alert and click Click for details from the Raise Threat Alert action.
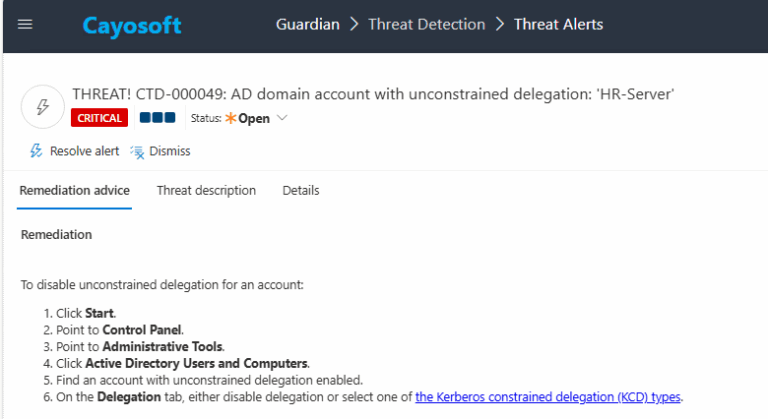
4.) Review Evidence:
- User principal name
- Distinguished Name
Remediation Steps
1.) Using the remediation advice in Cayosoft Guardian, follow these steps to remove the vulnerability:
If changes occurred before Cayosoft Guardian was installed, consider restoring default permissions
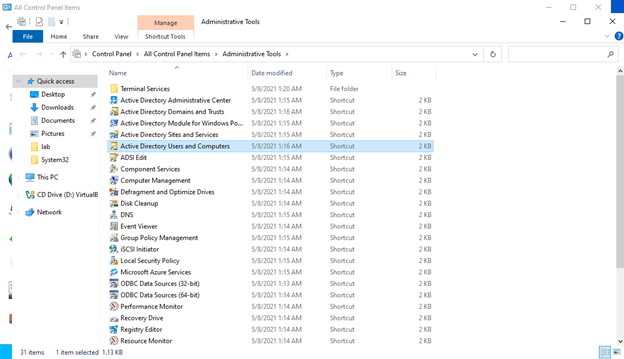
2.) Click Start
3.) Open Administrative Tools
4.) Launch Active Directory Users and Computers
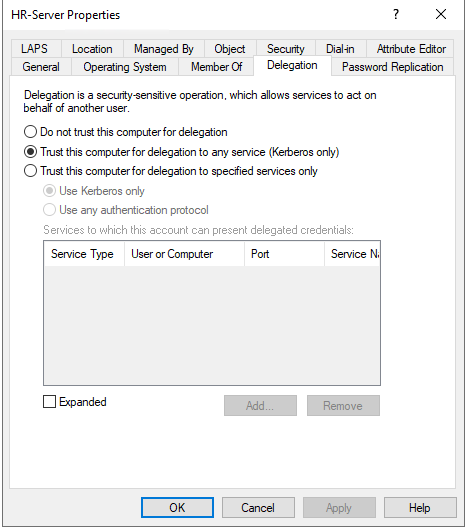
5). Locate any account with unconstrained delegation
6.) On the Delegation tab, either disable delegation or configure one of the Kerberos constrained delegation (KCD) types
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain accounts with unconstrained delegation. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
If an attacker gains access to such an account, they can access confidential data and act on behalf of any user.
- Open Active Directory Users and Computers.
- Find the account with unconstrained delegation enabled.
- Go to the Delegation tab.
- Either disable delegation or select a Kerberos constrained delegation type.
Using tools like Cayosoft Guardian can simplify detection and remediation of such accounts.
Final Thought
AD domain accounts with unconstrained delegation represent a critical vulnerability because an attacker who gains access to such an account can impersonate any user, including administrators, and access confidential data. To protect against this, delegation should be limited only to truly important service accounts, with a preference for constrained delegation, and these accounts should be regularly reviewed to remove any unnecessary privileges. Using tools like Cayosoft Guardian helps quickly detect and remediate such vulnerabilities.