Home » Your Guide to Secure Endpoint Management: Essential Microsoft Intune Features
Your Guide to Secure Endpoint Management: Essential Microsoft Intune Features
Learn how Microsoft Intune's cloud-based endpoint management solution helps secure and manage devices, identities, and applications in today's global and non-traditional workforce.
Explore the chapters:
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Today’s workforce is distributed globally and works in non-traditional ways, such as in a hybrid or remote setup. Additionally, they use multiple devices to access organizational resources, including personal devices. With a diverse range of access methods, security administrators face increasing challenges in protecting organizational data and providing access to it while allowing users to access it from anywhere.
Microsoft Intune, a cloud-based endpoint management solution, addresses these challenges while providing several other features that help you securely manage devices, identities, and applications. This article explains Microsoft Intune features and capabilities, including core features that are table stakes for the platform and advanced features that can help improve an organization’s security posture and reduce business risk.
Summary of key Microsoft Intune features and capabilities
The table below summarizes the key features and capabilities of Microsoft Intune that this article will explore in more detail.
| Feature | Description |
|---|---|
| Mobile Device Management (MDM) | Helps teams manage and secure mobile devices (smartphones, tablets, laptops) to protect organizational data and enforce compliance. |
| Mobile Application Management (MAM) | Protects organizational data within applications on both managed and unmanaged (personal) devices without requiring full device enrollment. |
| Endpoint Analytics | Provides insight into the status, health, and performance of all managed endpoints. |
| Microsoft Intune Tunnel for Mobile Application Management | A micro VPN solution for unenrolled devices. |
| Microsoft Intune management of specialty devices | Enables the managing, configuring, and protecting of special devices, such as AR/VR headsets, smart screens, and meeting devices. |
| Microsoft Intune firmware-over-the-air (FOTA) updates | Allows remote firmware updates on supported Android devices without physical access. |
| Microsoft Cloud PKI | A PKI solution to create and manage certificate authorities and manage the certificate lifecycle. |
| Microsoft Defender for Endpoint | A security platform that helps detect, investigate, and respond to endpoint threats. |
Learn About The First-Ever Monitoring and Rollback for Microsoft Intune
Overview of Microsoft Intune
Microsoft Intune is a cloud-based endpoint management solution that enables secure management of user access, devices, and applications to organizational data across multiple platforms and a diverse mobile workforce. Whether you are looking to add and manage devices at scale, enforce consistent security policies across teams, allow secure access to organizational applications and data from personal devices, support bring-your-own-device (BYOD) policies, or manage application deployment, Microsoft Intune has a feature that can meet the requirement. There are many more features that make it a comprehensive solution for endpoint management. It provides a compliant and consistent user experience for devices.
The following illustration provides a high-level overview of Microsoft Intune’s capabilities, many of which we will discuss later in the article.
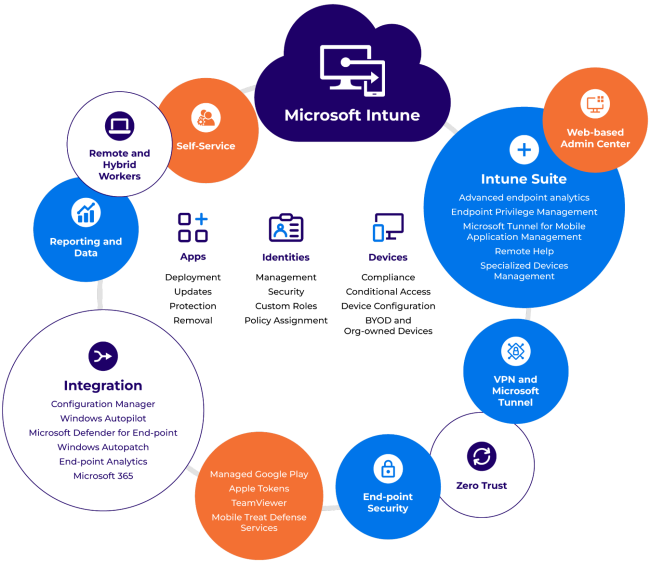
Microsoft Intune core features
Microsoft Intune’s primary objective is to provide a unified endpoint visibility, management, and security platform that protects organizational data while offering a productive work experience. Intune’s core features, like Mobile Device Management (MDM), Mobile Application Management (MAM), Endpoint Analytics, and built-in endpoint security, address these objectives.
Mobile Device Management (MDM)
As the use of mobile devices increases in work environments, administrators are faced with device management challenges like:
- Ensuring consistent settings across the devices.
- Push applications to devices.
- Installing certificates, profiles, wi-fi configurations, etc on them.
- Deleting organizational data from the devices or wiping the entire device.
- Reducing the risk of insider threats using mobile devices as an attack vector.
- Tracking, reporting, and measuring compliance across the devices.
Microsoft Intune provides a comprehensive device management solution that addresses these challenges across multiple platforms, including Windows, macOS, iOS, and Android. It also supports multiple cloud-connected endpoint types, including mobile, desktop, laptop, and virtual devices, making it a comprehensive cross-platform endpoint management solution.
Using MDM, organizations can address requirements such as:
- Issuing and managing corporate-owned devices, for example, locking them down to access only approved apps, disabling access to app stores, or wiping a device when lost or stolen.
- Enforcing compliance for use cases such as when dealing with healthcare data by implementing features such as encryption, device lock, or performing updates.
Teams can manage both organization-owned and personal devices with Microsoft Intune MDM.
Mobile Application Management (MAM)
Mobile applications are the general norm these days, and it’s common for Organizations and their employees to rely on them for day-to-day work. These apps can be found in private or public app stores, such as those from Microsoft, Google, and Apple. Additionally, organizations allow BYOD to enable flexibility and improve productivity. This creates various security, compliance, and management challenges, such as:
- Deploying, configuring, updating, and removing applications to users.
- Protecting data access and sharing, especially on personal devices.
- Deleting data from the applications.
- Implementing compliance policies for regulatory needs.
Microsoft Intune MAM allows organizations to overcome these challenges and more at the app level. Administrators can deploy a managed app to users and devices, automatically update apps to stay compliant, create policies that meet organizational security and compliance requirements, such as data sharing, and monitor application metrics, including usage, unauthorized apps, and licenses. Teams can also use Microsoft Entra’s Conditional Access Policies to control application access.
Intune MAM can be used on devices enrolled with Intune MDM and those not enrolled with Intune.
Watch a 15-minute Demo of Microsoft Intune Change Monitoring and Recovery
Endpoint Security
Microsoft Intune dashboard provides an Endpoint Security section where you can view, manage, monitor, and configure security settings. Some are built into Intune, while others require an add-on license (e.g., Endpoint Privilege Management).
Security operations Microsoft Intune Endpoint Security supports include:
- Review and manage devices, view their compliance status, and perform device-level operations such as scanning a device, changing BitLocker encryption keys (Windows only), restarting a device, etc.
- Apply security baselines to device profiles.
- View and manage security policies such as Antivirus, Disk Encryption, and Firewall policies to improve device security.
- Endpoint security management managing Endpoint Privilege Management, Endpoint Detection and Response (EDR), and conditional access policies.
- Integration with Microsoft Defender for Endpoint is supported directly from Microsoft Intune.
- Manage security tasks from Microsoft Defender for Endpoint and take actions like remediating them.
Endpoint Analytics
Endpoint Analytics provides insights into the user experience, highlighting issues that impact user productivity. The problems could range from hardware issues to software problems and everything in between, such as configuration settings, updates, and policies. With Endpoint Analytics, organizations can proactively identify and resolve problems, optimizing policies and configurations to reduce the effort and cost of IT support.
Integrations with other Microsoft Products
Microsoft Intune integrates with Microsoft Entra ID, providing identity and access control capabilities to Intune for authenticating devices and users that use them, device enrollment and management, enabling conditional access enforcement for compliance and device security, and other features such as support for role-based access control (RBAC) to improve overall identity governance and administration.
It integrates with Microsoft Purview Information Protection, allowing administrators to implement endpoint data loss prevention (DLP) policies on managed devices.
Microsoft Intune can enhance productivity for M365 apps when used in conjunction with Microsoft 365. It can also be used with on-premises Exchange and Active Directory (AD) to connect to external services with Intune connectors.
Microsoft Intune Advanced Features
Next, let’s examine the advanced Microsoft Intune features and capabilities that can help modern organizations address complex use cases.
Microsoft Intune Tunnel for Mobile Application Management
Tunnel for Mobile Application Management is a micro VPN solution for mobile devices that cannot be enrolled in Intune. This Microsoft Intune feature uses the Microsoft Tunnel VPN Gateway, which must have already been deployed.
Using Microsoft Intune Tunnel, organizations can enable use cases such as:
- Bring-your-own-device (BYOD) scenarios, where users use their own devices for both work and personal use and do not want the organization to control them.
- Secure access to an organizational app without device enrollment through the per-app VPN capability of Microsoft Intune Tunnel.
- Implementing conditional access on unmanaged devices for access to internal resources.
- Enabling Single Sign-on (SSO) based access to organizational resources.
The following platforms are supported:
- Android Enterprise version 10.0 or higher
- iOS version 14.0 or higher
Learn the best practices for Intune monitoring, security, and recovery
Specialty devices management
Through add-on licensing, Microsoft Intune can support device management for specialized devices, including AR/VR headsets, smart screens, and conference room devices. This brings unified endpoint management to purpose-built devices, ensuring consistent security across all devices. Specialty device management is particularly beneficial to frontline workers.
Some of the scenarios that organizations can enable include:
- Monitoring, deploying Microsoft Teams updates, and enforcing security baselines in meeting rooms with Microsoft Teams Rooms (MTR) systems.
- Restrict kiosk devices to one or a fixed set of apps using the Kiosk Mode configuration.
- Enable the sharing of a single device among multiple frontline workers, such as nurses, with the Shared Device Mode feature. You can provision these specialty devices with pre-configured profiles for ease of use and isolation.
The following devices are supported:
- AR/VR devices like the RealWear and HTC devices
- Apple Vision Pro device
- Smart screen devices like Microsoft Surface Hubs
- Conference room devices like Microsoft Teams Rooms devices
Microsoft Intune firmware-over-the-air (FOTA) updates
This feature enables firmware updates on devices remotely using a wireless connection. It can also address use cases such as performing updates during a maintenance window to minimize downtime, maintaining consistent versions across an entire fleet, and distributing security updates as soon as they become available.
FOTA can be performed on-demand or on schedule. The following devices are supported:
- Android Enterprise devices
- Zebra LifeGuard Over-the-Air (LG OTA) devices
- Samsung E-FOTA (Enterprise Firmware-Over-The-Air)
It is important to note that not all devices and OEMs support FOTA.
Microsoft Intune Security & Compliance Features
Intune offers organizations a breadth of mission-critical security and compliance capabilities, including policies, mobile threat defense, public key infrastructure (PKI), and privilege management. The sections below explore five of these Microsoft Intune features and capabilities related to security and compliance.
Microsoft Intune Policies
Policies are the primary methods Intune administrators will use to protect devices and applications. They are built-in capabilities already available that are implemented using one or more profiles that apply to a set of enrolled devices.
Using device protection policies, teams can manage security settings such as authentication methods, device encryption, software updates, virtual private networks (VPNs) profiles, set a security posture, and more.
With app protection policies, organizations can protect data at the application level. This does not require device management. Therefore, both managed and unmanaged devices can be protected. Additionally, when an app is used in a work context, you can implement protections like entering a PIN.
Mobile Threat Defense using Microsoft Defender for Endpoint
Microsoft Defender for Endpoint can integrate with Intune to provide a Mobile Threat Defense solution that enforces compliance and helps limit security breaches and their impact. The integration enables threat protection capabilities including:
- Deploying endpoint security policies such as antivirus and endpoint detection and response (EDR) to managed devices.
- Threat and vulnerability management through security tasks.
- Using Microsoft Defender for Endpoint as a client application for Microsoft Tunnel on Android devices.
Microsoft Defender for Endpoint can be deployed on Android and iOS devices using Microsoft Intune.
Manage, Monitor & Recover AD, Azure AD, Office 365

Unified Console
Use a single tool to administer and secure AD, Azure AD, and Office 365

Track Threats
Monitor AD for unwanted changes – detect for security or critical functions

Instant Recovery
Recover global enterprise-wide Active Directory forests in minutes, not days
Endpoint Privilege Management
This feature enables organizations to apply Zero Trust principles by enforcing least-privilege access. Users are always granted the lowest possible privileges without being provided with full administrative rights. To perform admin actions, such as installing a program, administrators can configure elevation policies that meet the organization’s security needs.
EPM supports automatic and user-confirmed elevation types. Automatic elevations are great for trusted applications where predefined rules allow admin privileges to run them. User-confirmed elevations are ideal for administrative tasks requiring additional validation through rules or business justification.
Additionally, all privilege elevations are reported by default for review and audit.
Microsoft Cloud PKI
The Microsoft Cloud PKI add-on enables organizations to quickly establish their own cloud-based public key infrastructure (PKI), simplifying and streamlining certificate lifecycle management. With Cloud PKI, administrators can create a certificate authority that can automatically deploy certificates to managed devices, revoke certificates, and provide detailed reports on issued certificates. Teams can also use the Microsoft Cloud PKI feature for certificate-based authentication use cases.
Zero Trust in Microsoft Intune
The Zero Trust security strategy recommends verifying explicitly, using least privilege access, and always assuming breach. Intune, along with the features discussed in this article, supports it.
Here’s a summary of key Zero Trust in Microsoft Intune features and capabilities:
- Intune policies and Conditional Access are evaluated during authentication and authorization, allowing you to verify explicitly.
- Features like Endpoint Privilege Management (EPM) limit user access while enabling users to perform privileged tasks, and Intune policy for Windows Local Administrator Password Solution (LAPS) secure the local administrator account on Windows devices, helping Intune administrators implement the least privilege access principle.
- Intune’s integration with Microsoft Defender for Endpoint and third-party threat defense services enables real-time monitoring, threat response, and automated remediation covering the assume breach principle.
Microsoft Intune plans
Many features discussed in this article are add-ons and require a license. They can be purchased as an add-on license or bundled. So, it is important to know the different licensing options.
Microsoft Intune is available in three plans: Plan 1, Plan 2, and Suite. The following table summarizes the add-on capabilities and their licensing requirements.
| Capability | Include in Plan 1 | Buy Standalone (Plan 1 Required) | Included in Plan 2 | Included in Suite |
|---|---|---|---|---|
Core Features:
| Yes | N/A | Yes | Yes |
| Endpoint Privilege Management | No | Yes | No | Yes |
| Enterprise App Management | No | Yes | No | Yes |
| Advanced Analytics | No | Yes | No | Yes |
| Remote Help | No | Yes | No | Yes |
| Microsoft Tunnel for Mobile Application Management | No | No | Yes | Yes |
| Microsoft Cloud PKI | No | Yes | No | Yes |
| Firmware-over-the-air update | No | No | Yes | Yes |
| Specialized devices management | No | No | Yes | Yes |
Microsoft Intune Plans
It is also available as an education plan known as Intune for Education.
Manage, Monitor & Recover AD, Azure AD, M365, Teams
| Platform | Admin Features | Single Console for Hybrid (On-prem AD, Azure AD, M365, Teams) | Change Monitoring & Auditing | User Governance (Roles, Rules, Automation) | Forest Recovery in Minutes |
| Microsoft AD Native Tools | ✓ | ||||
| Microsoft AD + Cayosoft | ✓ | ✓ | ✓ | ✓ | ✓ |
Conclusion
Microsoft Intune is a unified, robust, and versatile endpoint management solution that provides essential MDM and MAM capabilities and features for secure and compliant access to organizational resources. It also provides cross-platform support for managing and securing devices, applications, and data. The core capabilities include endpoint security, analytics, and compliance enforcement policies.
Through add-on features, Microsoft Intune also provides endpoint management capabilities that include Zero Trust principles such as endpoint privilege management and cloud PKI, firmware over-the-air, a micro VPN tunnel for mobile application management, support for specialized devices, mobile threat defense through integration with Microsoft Defender for Endpoint and advanced analytics to name a few.
From essential mobile device and application management to advanced and mission-critical capabilities, Microsoft Intune is a one-stop solution for endpoint management.
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content