By Craig Birch, Technology Evangelist/Principal Security Engineer
Active Directory (AD) is not just another IT system, even though it is often overlooked by businesses. It is the backbone of enterprise identity, authentication, access to core applications, compliance controls, and cloud integration. During the Active Directory downtime, your entire business stops.
Operational Disruption:
Employees cannot log in, systems are inaccessible, and productivity grinds to a halt.
Financial Losses:
Every minute of downtime translates to lost revenue and escalating recovery costs. For many enterprises, the cost now exceeds $300,000 per hour, with 41% reporting losses of $15 million per hour.
Collateral Damage:
Customer trust erodes, reputational harm spreads quickly, and regulators take notice. If you are in healthcare, your risks are much greater as now patient safety is at stake.

AD is mission-critical infrastructure. That is why recovery must not only be measured in minutes vs hours or days, but also in the reliability that the recovery process will work when it’s needed.
Here is another way to think about the criticality of AD recovery and why it must always work when needed. Imagine you have car insurance, and then you are in a wreck, you have to call the insurance company, get the car towed to the repair shop, wait for the repairs, and hope that it is the same as it was before the accident. It’s not guaranteed, and there’s a high likelihood you’ll have issues with that car again in the future because of something missed. This is the same for AD recovery, whether using Windows Server backups, enterprise backups, or AD specific backup and recovery tools. Same steps and same hope. And there isn’t a guarantee it will work.
When AD goes down and everything halts, you cannot afford to bet on backups that may fail or recovery processes that may falter. Here’s why:
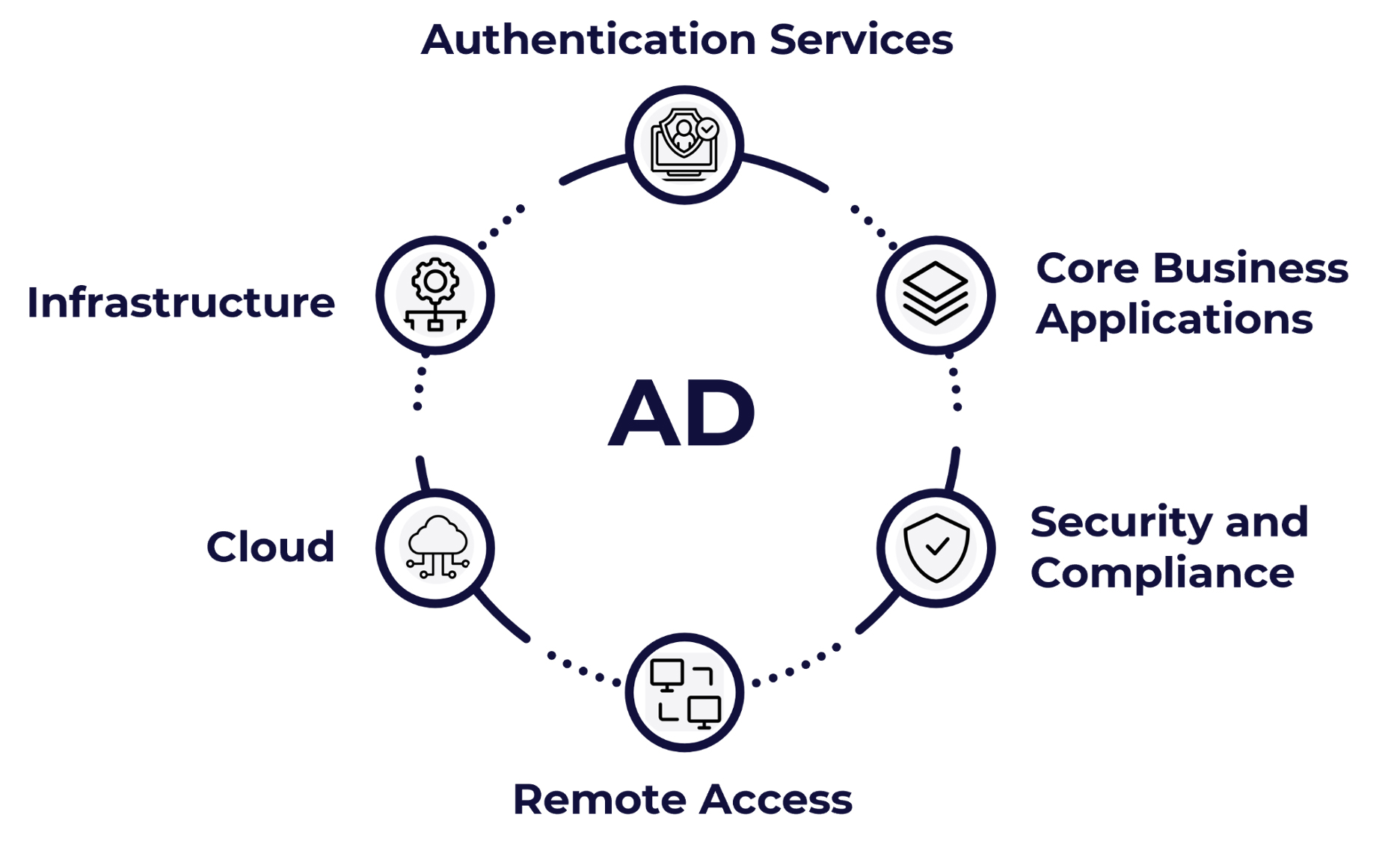
Identifying your Active Directory Dependencies
Executives often underestimate how many critical services and applications depend on Active Directory. When Active Directory downtime occurs, everything stops. Below are the key dependencies on AD:
- Authentication Services: Employees, partners, and customers are all locked out.
- Core Business Applications: ERP, CRM, Finance, and HR systems fail
- Security and Compliance: Controls collapse, audits stall, and exposure grows
- Remote Access: VPN and secure connections break, leaving employees idle.
- Cloud Integrations: Office 365, Azure, and hybrid identity services are disrupted
- Infrastructure: DNS, File shares, and dependent workloads fail.
This is not your typical IT outage that only impacts a few users or applications. This is a business outage where nothing gets done, you’re hemorrhaging money, customer trust, and leadership confidence by the minute.
Minimal Viable Business Recovery
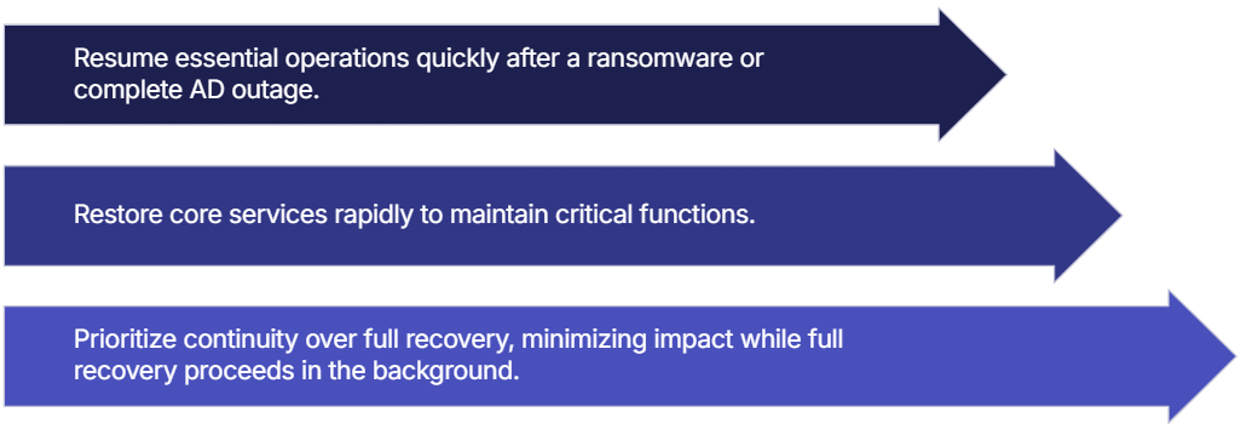
AD Recovery Methods
Most organizations still rely on one of the three legacy backup strategies or, in some cases, even an Active Directory Lag site as their safety net.
Windows Server Backup:
Enterprise Backup Tools:
Well-suited for normal workloads, and some have evolved to offer limited AD recovery, like attribute-level or domain controller–level restores. But they are heavily dependent on the operating system and hardware, which undermines trust in recovery results.
Third Party AD Backup Tools:
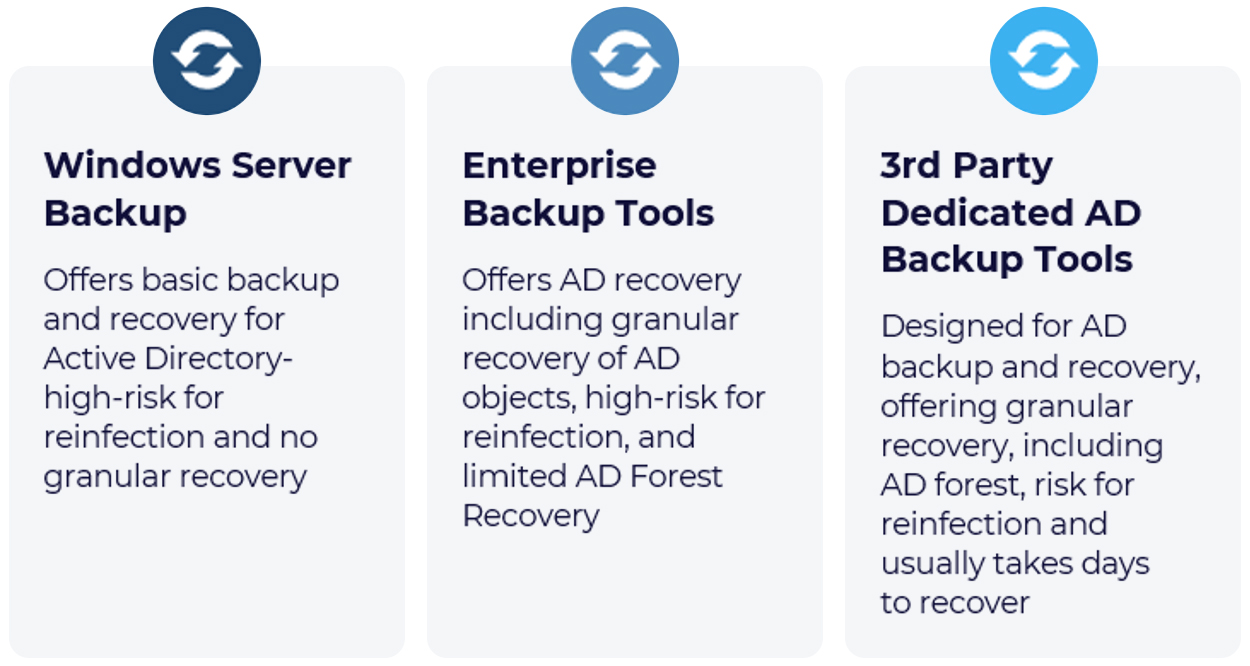
Threat actors have evolved their techniques and often target backups as part of their attack surface, whether that is deleting the backups, embedding malware, or creating persistence in Active Directory. All these solutions require you to perform the recovery post-outage and have low assurance that the recovery will succeed.
The Recovery Problem
Most organizations have built out business continuity and disaster recovery plans on paper, but they are rarely executed unless it is done in a very controlled exercise that takes weeks or months to prepare for. Trust me in this one. I was an AD architect and director at a large organization, and this is how the process goes.
We gather multiple teams to develop this plan, and then we build out this isolated environment and run through this massive exercise, and guess what, we fail to execute the plan, or the plan takes way longer than is acceptable by the business, sound familiar? I bet it does.
The other truth is that the plan is only on paper and never tested, and we are hoping that we get it right, or we are never in a situation where it is necessary.
The Biggest Challenges with AD Recovery
- Unvalidated backups: AD backups can fail for a number of reasons, including data corruption, embedded malware, or, more commonly these days, persistence mechanisms such as Golden Tickets, AdminSDholder, or GPO malware.
- Lack of regular testing: Most organizations have not run a full forest AD recovery, and the ones that have do it only a few times a year in a controlled environment.
- All-at-once recovery: Most traditional backup solutions force you into performing a full recovery, cascading failures that lead to extended downtime.
- Infrastructure gaps: DNS failures, missing domain controllers, and replication breakdowns halt the recovery process.
The result is confusion, high stress, delayed recovery, and rising business costs.
Reinfection: The Silent Failure
Attackers design persistence to survive your traditional recovery processes.
Below are the common hidden footholds:
- Golden and Silver Tickets
- SID History abuse
- AdminSDHolder tampering
These hidden threats ensure that Active Directory downtime is not only prolonged but potentially recurring. They often reappear the moment backups are restored.
No, this isn’t science fiction. I witnessed this firsthand when an organization claimed that they were breached three times in six months, but they soon found out that wasn’t the case. The attacker had created hidden persistence, and they were just restoring to what I call a compromised state that can never be trusted.
What this means for your business and teams
- Regulators call this negligence
- Customers see it as incompetence
- Boards see it as a leadership failure
Why the Instant Standy Environment Works Every Time
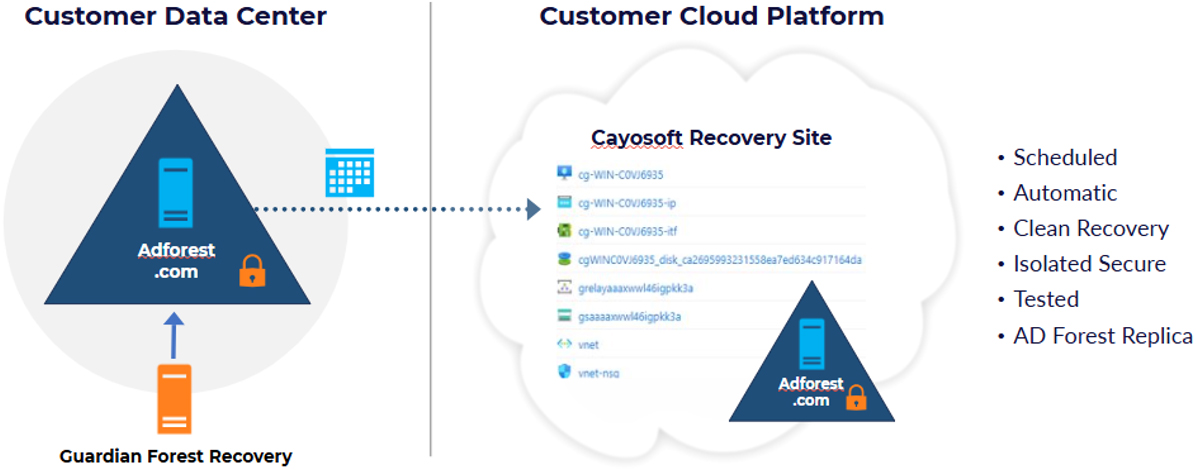
Cayosoft Guardian Forest Recovery™ changes the equation with a patented, isolated, clean standby AD forest.
Our patented, standby approach works every time because it is continuously prepared, verified, and waiting for instant activation.
- Your Active Directory components are protected in an isolated, cloud-based environment.
- Malware and ransomware are eliminated through trusted, clean, patched cloud virtual machine templates.
- Persistence tactics are identified and remediated before production is reconnected.
- Directory objects are validated for integrity and compliance
- Reinfection is prevented by rejecting old, compromised credentials.
If we return to the car wreck analogy, now, instead of going through the repair shop, waiting for the repairs, and then getting your car back with new creaks and moans, imagine that you call your insurance company and they hand you keys to your same exact car that is already proven, trusted, and ready to drive. This is what it’s like with Cayosoft instant standby forest recovery.
The difference is profound. No fragile backups to test, no chaotic theoretical playbooks, and no hope-based recovery. With Cayosoft, recovery is reliable, instant, and trusted. So, the business can move forward with confidence.
Don’t wait for Active Directory downtime to expose gaps in your recovery plan. Schedule a demo to see how Cayosoft Guardian delivers instant, trusted AD recovery.
Learn About Instant Forest Recovery and Why A Standby AD Forest is Superior to Traditional Backup
Monitor and protect your Active Directory with real-time change tracking and instant recovery. Enhance your password policies and safeguard privileged accounts effectively.
FAQs
Active Directory downtime can be triggered by ransomware attacks, misconfigurations, hardware failures, or even planned maintenance gone wrong. Because AD is the backbone of authentication, identity, and access, even short disruptions quickly cascade into business outages where employees, applications, and cloud integrations all fail simultaneously.
The best way to minimize Active Directory downtime risk is to have a recovery strategy that goes beyond traditional backups. Backups are often untested, vulnerable to malware, and can reintroduce persistence. Using an isolated, continuously validated standby environment provides a clean and trusted recovery path, ensuring downtime is kept to minutes rather than hours or days.
When Active Directory downtime occurs, the entire organization is affected. Employees can’t log in, ERP and CRM systems fail, VPNs collapse, and compliance controls break down. Financial losses can climb to hundreds of thousands of dollars per hour, and customer trust can erode permanently if recovery isn’t fast and reliable.
Reinfection often occurs because hidden persistence mechanisms, such as Golden Tickets, SID history abuse, or AdminSDHolder tampering, survive traditional backup-based recoveries. Organizations believe they’ve restored AD, but in reality, they’ve restored a compromised state. This is why trusted, validated recovery is critical to avoid repeated outages and ongoing Active Directory downtime.
Traditional backups may help restore files or servers, but they rarely guarantee a clean Active Directory recovery. They often fail during real incidents, lack granular recovery options, and can’t remove embedded malware or persistence. This leads to extended outages, increased costs, and the very real risk of further Active Directory downtime.