Short-lived privileged AD object
Cayosoft Threat Definition CTD-000093
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An AD user who has been added to and then removed from a privileged group may indicate potential threat activities. Brief, high-privilege membership windows enable rapid abuse while evading routine reviews.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection, Privileged Access Management
- MITRE ATT&CK Tactics: Privilege Escalation; Defense Evasion
- MITRE D3FEND Tactics: Domain accounts monitoring
Description
A short-lived privileged AD object is an account that briefly gains membership in a built-in administrative group and is then removed. Built-in privileged groups are defined as those with adminCount=1 and well-known SIDs (protected by AdminSDHolder/SDProp). Attackers or rogue insiders may add an account to such a group just long enough to grant rights, plant persistence, or run privileged actions, and then remove the evidence of elevated membership. According to security best practices, administrative accounts should not be reused and should be de-provisioned when no longer needed to prevent lingering access paths.

Real-World Scenario
An attacker obtains a helpdesk operator’s delegated rights and briefly adds a standard user to Domain Admins to push a GPO that deploys a backdoor, then removes the user 90 seconds later. The attacker avoids obvious detection by limiting the elevation window and relying on nested group membership. The organization later sees file server tampering but no persistent admin membership. CTD-000093 surfaces the short-lived elevation with adminStart/adminEnd timestamps and the account name, allowing responders to trace actions in that precise window and revoke persistence.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
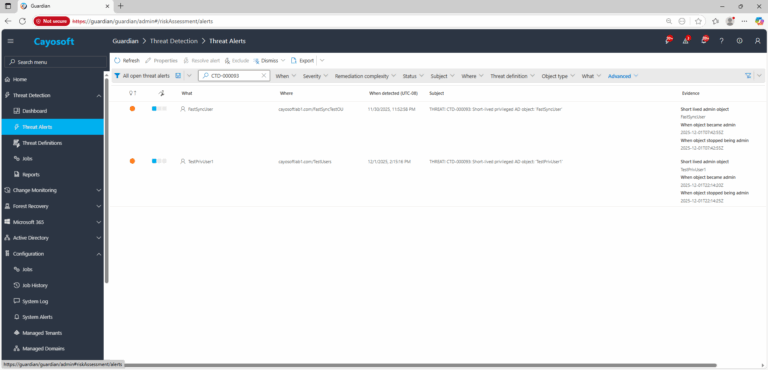
2.) Open All Alerts and search for CTD-000093 or Short-lived privileged AD object.
3.) Open any alert and Click for details (from Raise Threat Alert action).
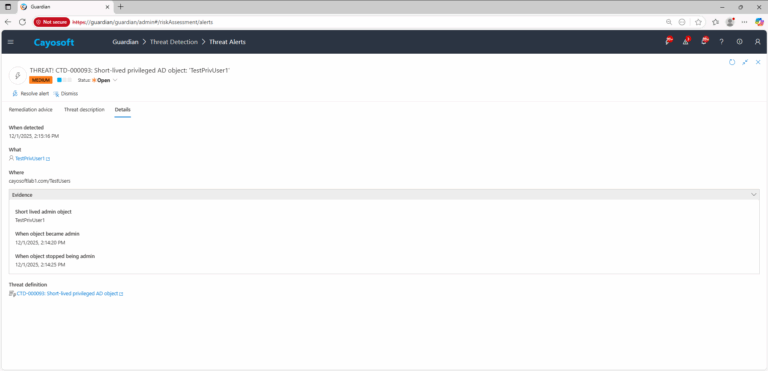
4.) Evidence:
- Short lived admin object
- When object became admin
- When object stopped being admin
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Short-lived privileged AD object. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Guardian continuously tracks group membership changes and correlates the adminStart/adminEnd timestamps with built-in privileged groups, alerting when an account enters and exits a privileged group within the configured interval.
Yes. Some workflows or scripts temporarily grant elevated rights. However, any unexpected or undocumented elevation should still be treated as a potential security incident until verified.
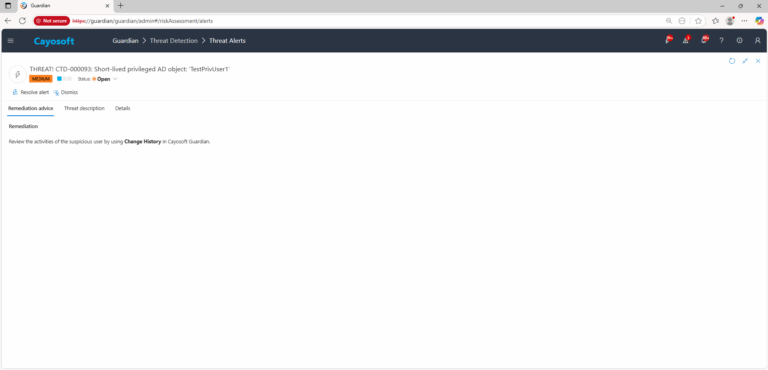
Start with the account’s Change History, validate whether the elevation was authorized, and check for privileged actions taken during the short time window.
Yes. Free tools such as built-in Active Directory auditing, PowerShell scripts to track group membership changes, and open-source AD security scanners can help identify unusual privilege changes — including rapid admin membership toggles.
Yes. Commercial solutions like Cayosoft Guardian provide continuous monitoring, alerting on suspicious privilege changes, full audit trails (who, when, where), and guided remediation steps if a short-lived elevation is detected.
References
- Microsoft Open Specifications — adminCount attribute: https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- Microsoft Community Hub — AdminSDHolder and SDProp overview: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Short-lived privileged AD object, you reduce attack surfaces and strengthen your organization’s overall security posture.