Privileged AD user not protected from using unsecure authentication methods
Cayosoft Threat Definition CTD-000079
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
The Protected Users group reduces credential exposure for privileged accounts. When a privileged AD user is not in this group, legacy and weaker authentication paths (e.g., NTLM, RC4/DES) remain available, increasing the risk of credential theft and reuse.
- Severity: High
- Platform: Active Directory
- Category: Account protection, Privileged Access Management
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Members of the Protected Users group that authenticate to a domain controller are unable to authenticate with NTLM, use DES/RC4 in Kerberos pre-auth, be delegated (constrained or unconstrained), or renew TGTs beyond ~4 hours (600 minutes). Using Protected Users for privileged accounts limits attack surface by removing common theft and replay paths.
Note: Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1 (accounts protected due to membership in administrative groups). See Microsoft’s documentation for details about the adminCount attribute and AdminSDHolder/SDProp behavior (links in References).

Real-World Scenario
A helpdesk user was temporarily added to Domain Admins and later removed, but the account retained administrative privileges on some systems due to cached rights. Because the user is not in Protected Users, authentication falls back to NTLM on legacy servers. An attacker with network access performs pass-the-hash against that account, pivots to a management server, and dumps additional secrets while avoiding obvious Kerberos anomalies. The attacker escalates using legacy protocols that Protected Users would have blocked. Cayosoft Guardian detects privileged users not protected by Protected Users and raises alerts so remediation can be applied before credential theft succeeds.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
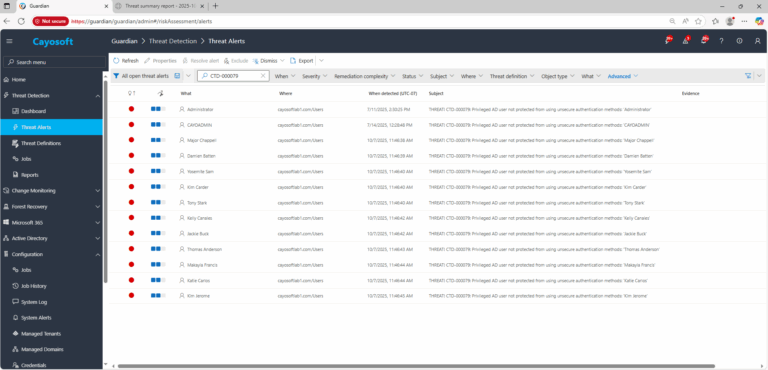
2.) View All Alerts and search for CTD-000079 or Privileged AD user not protected from using unsecure authentication methods.
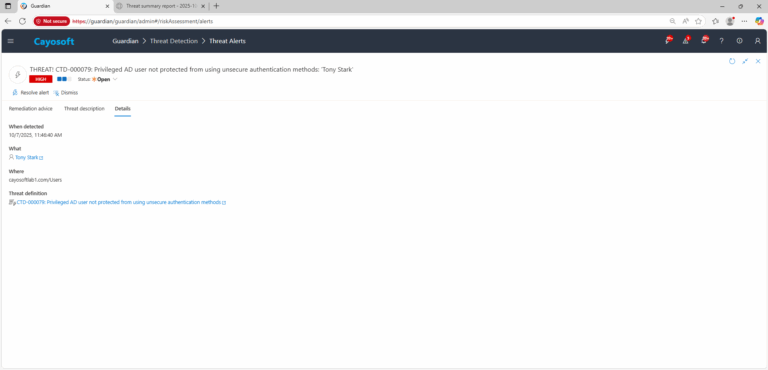
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review the list of privileged users (adminCount=1) and verify membership status in Protected Users.
Remediation Steps
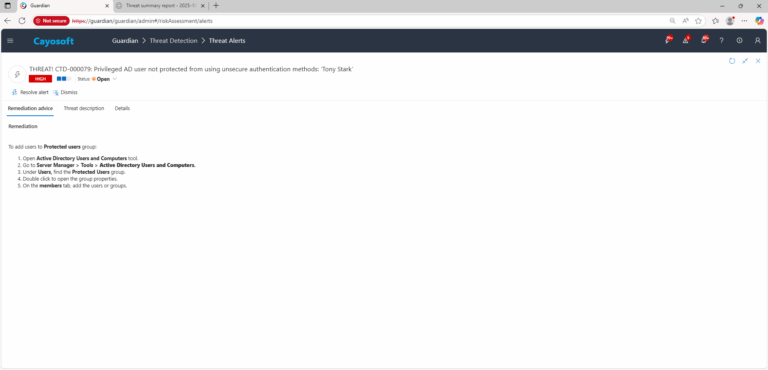
To add users to Protected users group:
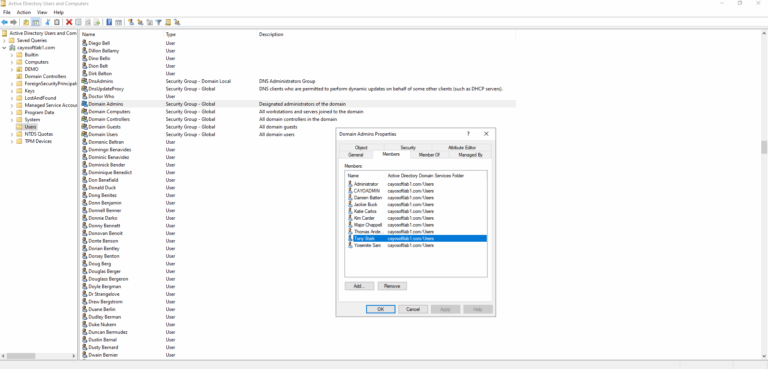
- ) Open Active Directory Users and Computers tool.
- ) Go to Server Manager > Tools > Active Directory Users and Computers.
- ) Under Users, find the Protected Users group.
- ) Double click to open the group properties.
- ) On the members tab, add the users or groups.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Privileged AD user not protected from using unsecure authentication methods. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
- Ensure all privileged users (adminCount=1) are members of Protected Users.
- Enforce tiered administration and dedicated admin accounts; de-provision temporary admin accounts promptly.
- Disable or restrict NTLM, and enforce modern Kerberos encryption types via domain policy.
- Regularly review AdminSDHolder/SDProp behavior to understand protected account handling.
- Monitor authentication logs for NTLM usage and weak cipher negotiation by privileged identities.
FAQ
When privileged Active Directory users are not members of the Protected Users group, they can still authenticate using weak or legacy protocols like NTLM or RC4/DES. These insecure methods are vulnerable to pass-the-hash and credential replay attacks, allowing threat actors to steal and reuse admin credentials for lateral movement or full domain compromise.
In the Cayosoft Guardian Threat Detection Dashboard, search for CTD-000079 or the issue name. The alert identifies privileged users (with adminCount=1) who are not members of the Protected Users group, helping administrators quickly locate accounts that remain exposed to insecure authentication mechanisms.
Open Active Directory Users and Computers, navigate to the Protected Users group, and add the privileged accounts listed in the alert. This enforces stronger authentication rules—disabling NTLM, RC4/DES, and delegation—and limits ticket lifetimes to reduce credential theft risks. Always verify that service or legacy accounts are excluded to avoid authentication failures.
References
- Microsoft Open Specifications — adminCount attribute: https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- Microsoft Community Hub — Five common questions about AdminSDHolder and SDProp: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged AD user not protected from using unsecure authentication methods, you reduce attack surfaces and strengthen your organization’s overall security posture.