Privileged AD user account with associated SPNs
Cayosoft Threat Definition CTD-000058
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Privileged user accounts that have Service Principal Names (SPNs) are prime targets for Kerberoasting. Attackers can request service tickets for these SPNs and crack them offline to obtain the privileged account’s password, enabling rapid lateral movement.
- Severity: High
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Credential Access, Lateral Movement
- MITRE D3FEND Tactics: Domain Account Monitoring, Application Configuration Hardening, User Account Permissions
Description
Kerberoasting attacks abuse the Kerberos Ticket Granting Service (TGS) to gain access to accounts by requesting service tickets for accounts that have SPNs and then cracking those tickets offline. Targets often include privileged accounts, which increases impact if cracked.
Note: Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1 (a protection applied to members of administrative groups). Links about this protection are provided in References.

Real-World Scenario
A legacy admin account (member of a protected group) runs a line-of-business service and has several SPNs. An attacker with only domain user rights requests TGS tickets for those SPNs, exports them, and brute-forces the RC4/AES hashes offline. After recovering the admin password, the attacker signs into servers, pushes tools via SMB/WinRM, and creates scheduled tasks for persistence while avoiding noisy group membership changes. Cayosoft Guardian with CTD-000058 would flag privileged users that have SPNs so the SPNs or privileges could be removed before compromise.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
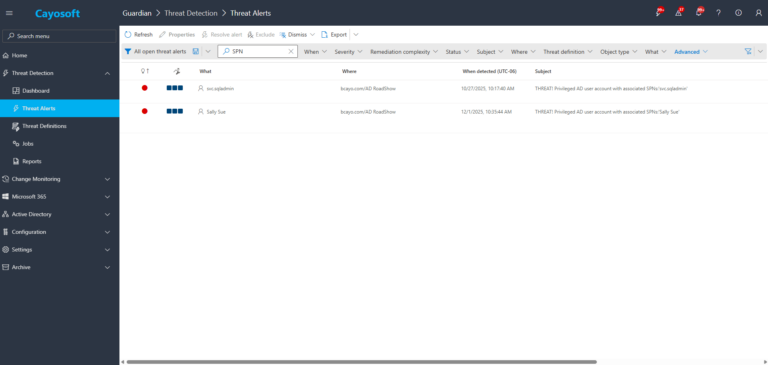
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000058 or Privileged AD user account with associated SPNs.
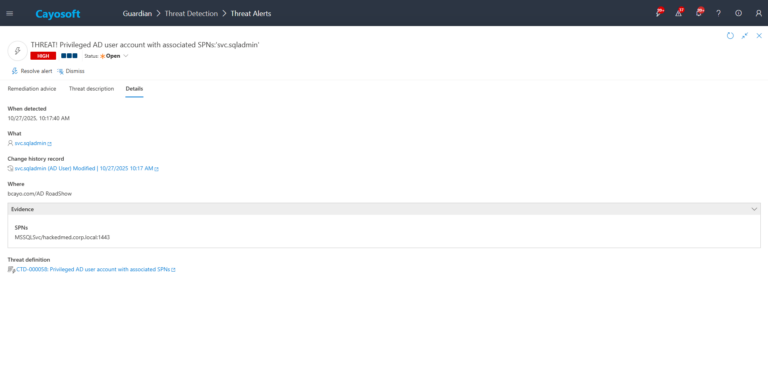
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- SPNs (servicePrincipalName)
Remediation Steps
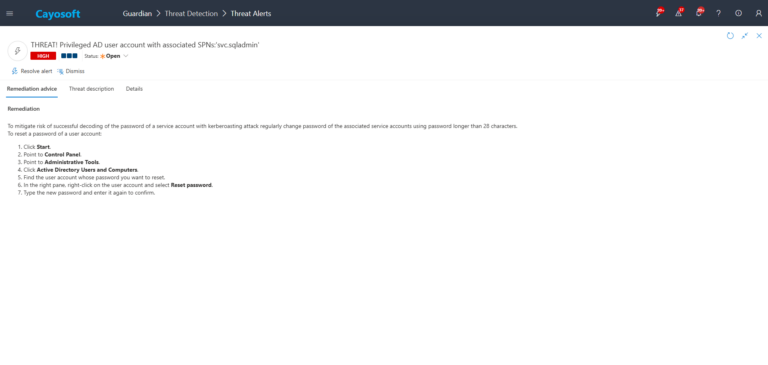
Using the remediation advice in Cayosoft Guardian, follow these steps to remove the vulnerability:
To mitigate risk of successful decoding of the password of a service account with kerberoasting attack regularly change password of the associated service accounts using password longer than 28 characters.
To reset a password of a user account:
- ) Click Start.
- ) Point to Control Panel.
- ) Point to Administrative Tools.
- ) Click Active Directory Users and Computers.
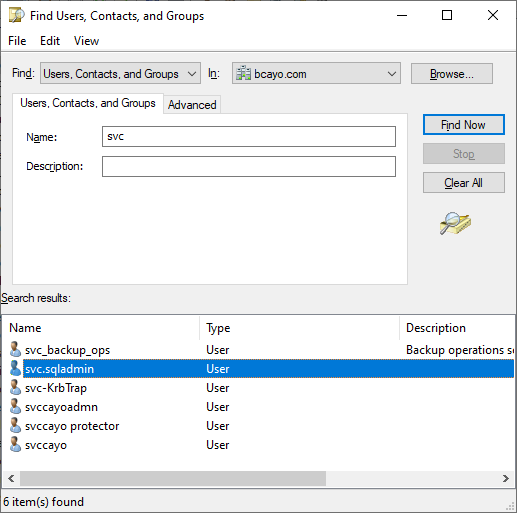
- ) Find the user account whose password you want to reset.
- ) In the right pane, right-click on the user account and select Reset password.
- ) Type the new password and enter it again to confirm.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Privileged AD user account with associated SPNs. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Because any authenticated domain user can request Kerberos service tickets for those SPNs and perform offline cracking. If the password belongs to a privileged account, a successful crack grants the attacker immediate high-value access and rapid lateral movement.
Migrate services off privileged user identities to gMSAs or dedicated non-privileged service accounts, remove stale SPNs, and rotate service credentials with long, high-entropy passwords.
Yes. Cayosoft Guardian Protector can detect privileged accounts with SPNs and other AD misconfigurations at no cost.
Yes. Cayosoft Guardian provides continuous monitoring, alerting, configuration auditing, and prescriptive remediation for Kerberoasting-related risks and more than 200 other AD/M365 vulnerabilities.
References
- Microsoft Open Specifications — adminCount attribute: https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- Microsoft Community Hub — Five common questions about AdminSDHolder and SDProp: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged AD user account with associated SPNs, you reduce attack surfaces and strengthen your organization’s overall security posture.