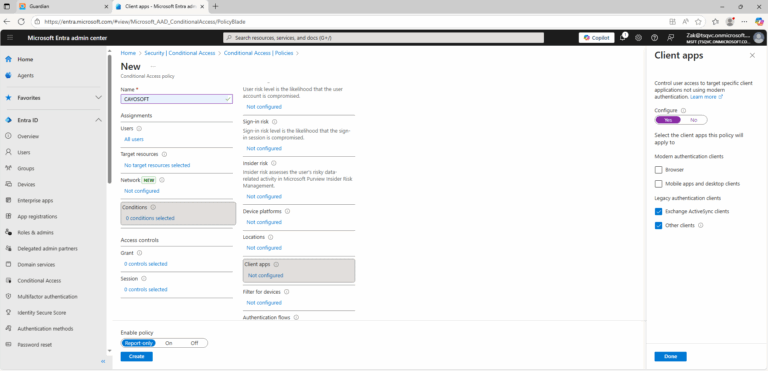
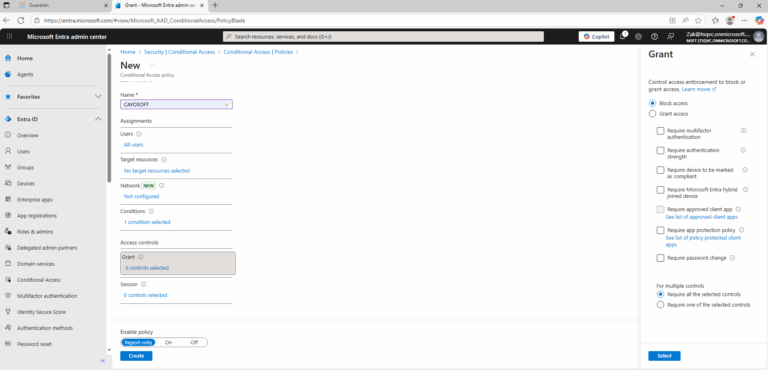
Missing Conditional Access Policies for blocking legacy authentication
Cayosoft Threat Definition CTD-000170
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
- Severity: High
- Platform: Entra ID
- Category: Account protection, Tenant-wide
- MITRE ATT&CK Tactics: Persistence, Defense Evasion, Credential Access
- MITRE D3FEND Tactics: D3-APA (Access Policy Administration)
Description
The absence of Conditional Access Policies to block legacy authentication poses a significant security vulnerability. Legacy authentication protocols like POP, IMAP, and SMTP do not support modern authentication methods such as multifactor authentication (MFA). These protocols are frequently exploited by threat actors for credential stuffing, brute force, and phishing attacks. Enforcing a block on legacy authentication greatly diminishes the risk of unauthorized access and enhances the overall security posture.

Real-World Scenario
A phished mailbox still receives IMAP connections from a residential proxy network. Because legacy auth isn’t blocked, the attacker keeps harvesting mail, sets server-side forwarding, and periodically authenticates via SMTP to send convincing internal phishing. Even after the user resets their password and enrolls MFA, the attacker’s basic-auth sessions continue to succeed. Cayosoft Guardian flags that the tenant lacks a block legacy authentication Conditional Access (CA) control so responders can close the gap.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
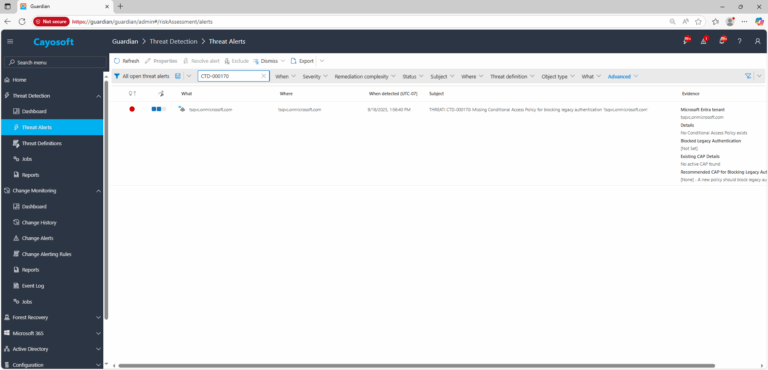
2.) View All Alerts and search for CTD-000170 or Missing Conditional Access Policies for blocking legacy authentication.
3.) Open any alert and Click for details (from Raise Threat Alert action).
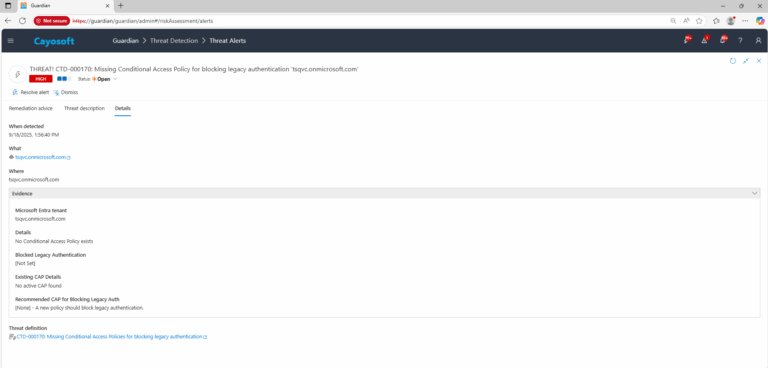
4.) Evidence:
- Microsoft Entra tenant
- Details (list)
- Blocked Legacy Authentication (Yes/No)
- Existing CAP Details (list)
- Recommended CAP for Blocking Legacy Auth
Remediation Steps
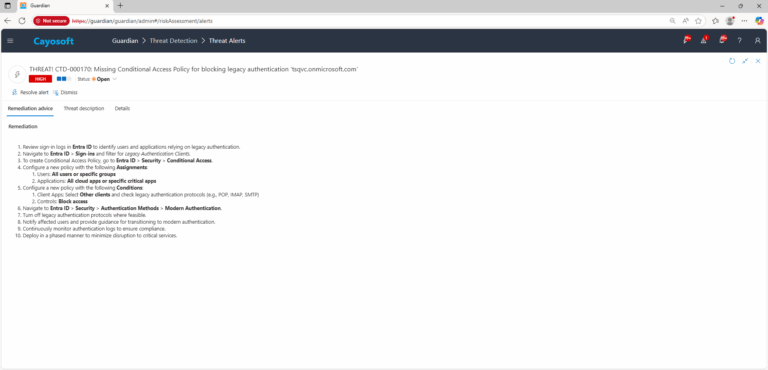
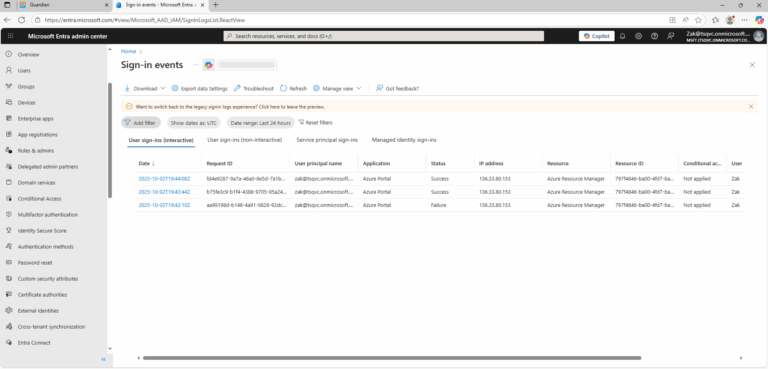
- ) Review sign-in logs in Entra ID to identify users and applications relying on legacy authentication.
- ) Navigate to Entra ID > Sign-ins and filter for Legacy Authentication Clients
- ) To create Conditional Access Policy, go to Entra ID > Security > Conditional Access.
- ) Configure a new policy with the following Assignments:
- ) Users: All users or specific groups
- ) Applications: All cloud apps or specific critical apps
- ) Configure a new policy with the following Conditions:
- ) Client Apps: Select Other clients and check legacy authentication protocols (e.g., POP, IMAP, SMTP)
- ) Controls: Block access
- ) Navigate to Entra ID > Security > Authentication Methods > Modern Authentication.
- ) Turn off legacy authentication protocols where feasible.
- ) Notify affected users and provide guidance for transitioning to modern authentication.
- ) Continuously monitor authentication logs to ensure compliance.
- ) Deploy in a phased manner to minimize disruption to critical services.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on missing Conditional Access policies for blocking legacy authentication. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Without a policy to block legacy authentication, attackers can exploit outdated protocols like POP, IMAP, and SMTP. These protocols do not support multifactor authentication (MFA) and are frequently abused for credential stuffing, brute force, and phishing attacks. Even if a user resets their password and enables MFA, legacy auth sessions can still succeed, leaving the environment exposed.
Tools such as Cayosoft Guardian can identify when a tenant is missing this control. To remediate, administrators should create a Conditional Access policy in Entra ID that blocks legacy authentication for all users and apps, with tightly controlled exclusions only for break-glass or critical accounts. Additionally, they should review sign-in logs to detect active use of legacy protocols, migrate affected services to modern authentication, and continuously monitor for residual attempts.
The recommended approach is to first run the policy in Report-only mode or target a pilot group to assess impact. Once validated, enforce the policy tenant-wide with a “Block access” grant. If any legacy clients are still required, replace them with modern clients wherever possible, or use a temporary, time-limited exception that is closely monitored.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Missing Conditional Access Policies for blocking legacy authentication, you reduce attack surfaces and strengthen your organization’s overall security posture.