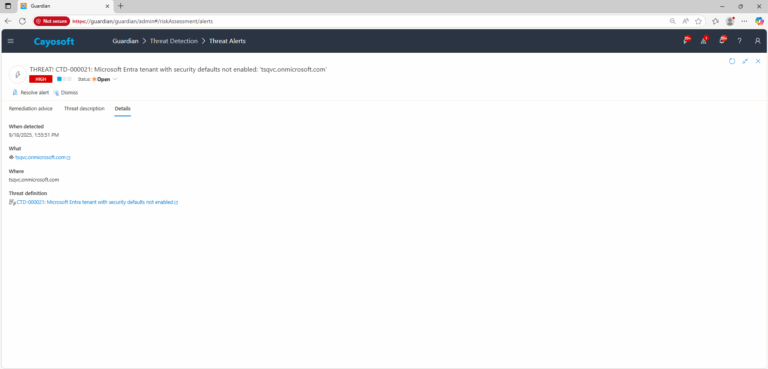
Microsoft Entra tenant with security defaults not enabled
Cayosoft Threat Definition CTD-000021
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Legacy authentication can’t enforce MFA or Conditional Access. If security defaults are not enabled (and no equivalent Conditional Access is in place), an attacker can reuse stolen credentials or perform password-spray attacks to gain access.
- Severity: High
- Platform: Entra ID
- Category: Infrastructure
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Microsoft Entra ID supports widely used protocols including legacy authentication. Legacy authentication can’t prompt users for MFA or satisfy Conditional Access requirements. With legacy authentication allowed in the tenant, a threat actor might use previously obtained credentials to log in and access resources.

Real-World Scenario
An attacker runs a low-and-slow password-spray against legacy protocols such as IMAP/POP or SMTP AUTH. Because the tenant hasn’t enabled security defaults or Conditional Access, the sign-ins bypass MFA and policy evaluation. The attacker lands mailbox access, sets forwarding rules to exfiltrate sensitive mail, and uses the account for internal phishing. Cayosoft Guardian flags CTD-000021 so operators can turn on security defaults or deploy Conditional Access to block legacy authentication before further compromise.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
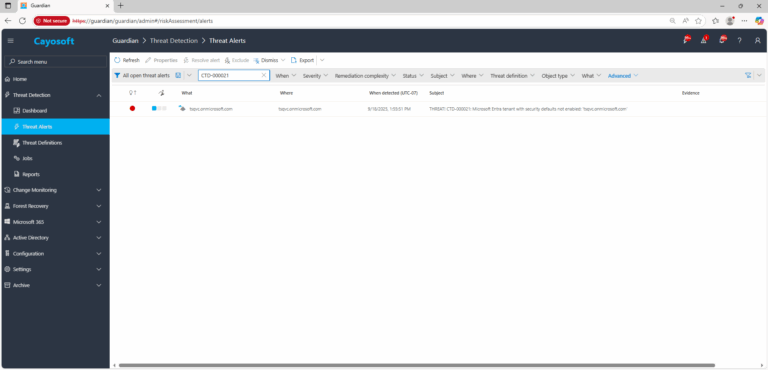
2.) View All Alerts and search for CTD-000021 or Microsoft Entra tenant with security defaults not enabled.
3.) Open any alert and Click for details (from Raise Threat Alert action).
Remediation Steps
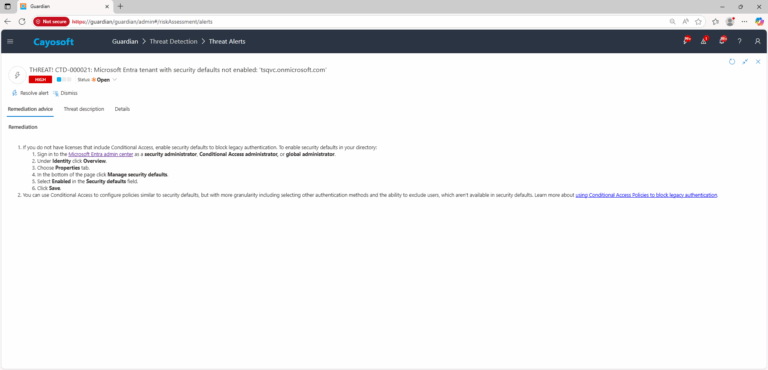
- ) If you do not have licenses that include Conditional Access, enable security defaults to block legacy authentication. To enable security defaults in your directory:
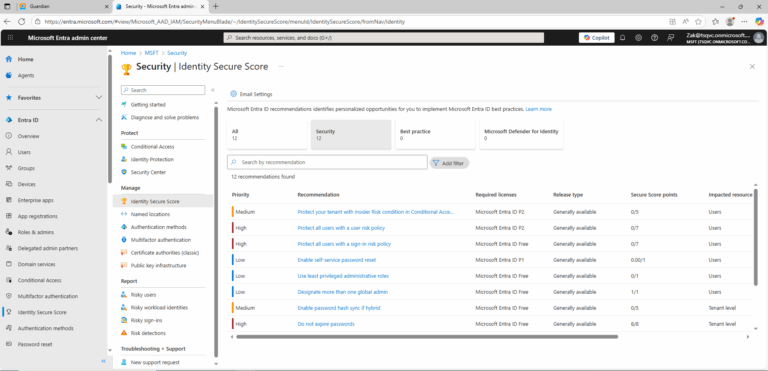
- ) Sign in to the Microsoft Entra admin center as a security administrator, Conditional Access administrator, or global administrator.
- ) Under Identity click Overview.
- ) Choose Properties tab.
- ) In the bottom of the page click Manage security defaults.
- ) Select Enabled in the Security defaults field.
- ) Click Save.
- ) You can use Conditional Access to configure policies similar to security defaults, but with more granularity including selecting other authentication methods and the ability to exclude users, which aren’t available in security defaults. Learn more about using Conditional Access Policies to block legacy authentication.
How to Prevent It
- Prefer Conditional Access to block legacy authentication and require MFA for all users.
- If CA isn’t available, enable Security defaults globally.
- Disable legacy/basic authentication protocols organization-wide where possible (Exchange Online, SMTP AUTH) and monitor for re-enablement.
- Enforce strong password policies and monitor failed sign-in patterns for password-spray indicators.
- Continuously monitor with Cayosoft Guardian for configuration drift (CTD-000021).
FAQ
Use Security defaults if you lack CA licenses; it provides baseline protection including blocking legacy auth. Use Conditional Access for granular policies and exclusions.
Yes, but limit them to the minimum, store credentials securely, excludeApps or devices relying on legacy protocols (POP/IMAP/SMTP AUTH/older Office clients) may fail. Migrate them to modern authentication or create targeted CA policies if licensed.from conditional access where appropriate, and audit frequently.
MFA is not evaluated on legacy auth. You must block legacy authentication via Security defaults or Conditional Access.
References
- Microsoft Entra admin center: https://entra.microsoft.com/
- Microsoft Learn — Use Conditional Access to block legacy authentication: https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/block-legacy-authentication
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra tenant with security defaults not enabled, you reduce attack surfaces and strengthen your organization’s overall security posture.