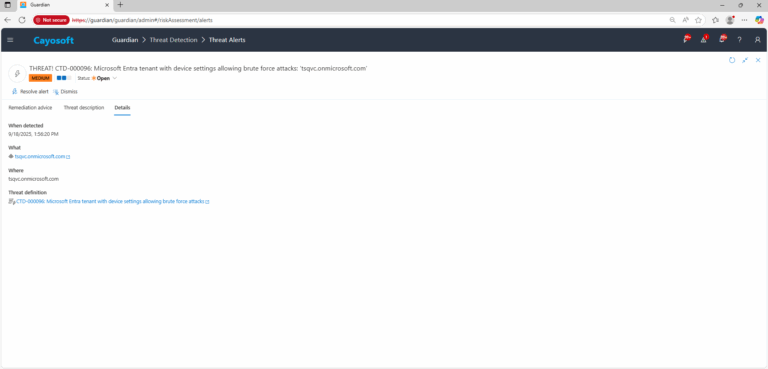
Microsoft Entra tenant with device settings allowing brute force attacks
Cayosoft Threat Definition CTD-000096
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
If devices allow unlimited password or PIN attempts, an attacker can brute-force credentials, gain device access, and install malware or extract corporate data.
- Severity: Medium
- Platform: Intune
- Category: Devices protection, Tenant-wide
- MITRE ATT&CK Tactics: Initial Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
If a device allows a threat actor to guess a password by making an unlimited number of attempts, a threat actor might get access to the device and compromise credentials, data, or install malicious software.

Real-World Scenario
An attacker steals a managed phone and repeatedly guesses the user’s PIN. Because Number of sign-in failures before wiping device is unset across the fleet, the device never wipes after failed attempts. After brute-forcing the PIN, the attacker unlocks the work profile, extracts cached OAuth tokens, and enrolls a malicious management app to persist. Business email and Teams data are exfiltrated before the user notices the loss. Cayosoft Guardian flags the risky Intune configuration (CTD-000096) so the security team can set a wipe threshold and block access, limiting impact.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
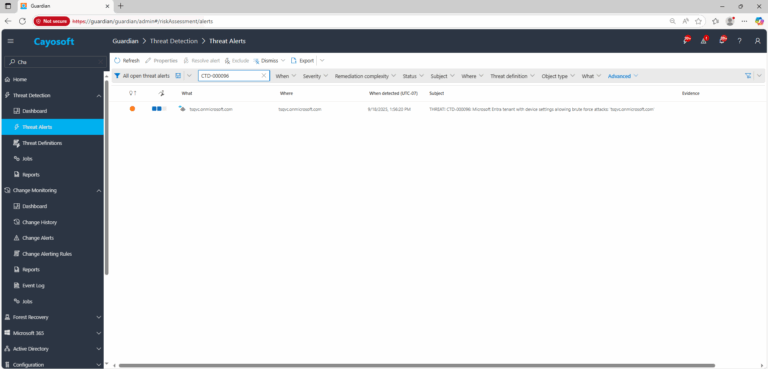
2.) Open All Alerts and search for CTD-000096 or Microsoft Entra tenant with device settings allowing brute force attacks.
3.) Open any alert and Click for details (from Raise Threat Alert action).
Evidence (example fields)
- Policy / Profile Name
- Platform / Profile Type
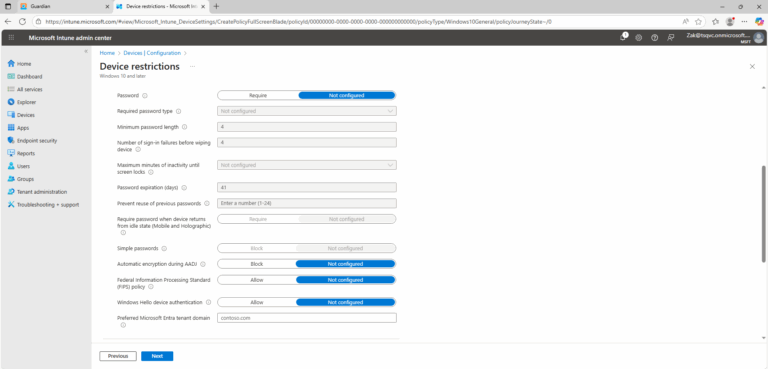
- Password policy: “Number of sign-in failures before wiping device”
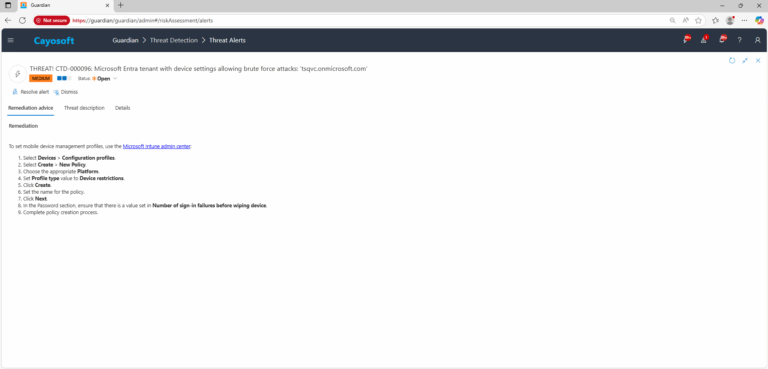
Remediation Steps
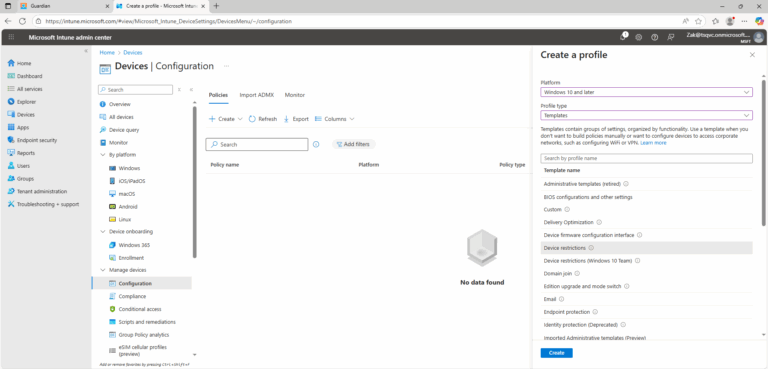
To set mobile device management profiles, use the Microsoft Intune admin center:
- ) Select Devices > Configuration profiles.
- ) Select Create > New Policy.
- ) Choose the appropriate Platform.
- ) Set Profile type value to Device restrictions.
- ) Click Create.
- Set the name for the policy.
- ) Click Next.
8.) In the Password section, ensure that there is a value set in Number of sign-in failures before wiping device.
9.) Complete policy creation process.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Microsoft Entra tenant with device settings allowing brute force attacks. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
If no limit is enforced, a stolen or unattended device can be brute-forced until the correct credentials are found, exposing cached tokens, applications, and sensitive data.
Many organizations use 5–10 failed attempts for smartphones and tablets. The threshold should balance security with user experience and align with organizational risk tolerance.
By enforcing strict device restriction policies in Intune, applying non-zero lockout thresholds, monitoring risky configurations with tools like Cayosoft Guardian, and reviewing compliance across all device groups.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra tenant with device settings allowing brute force attacks, you reduce attack surfaces and strengthen your organization’s overall security posture.