Insufficient forest and domain functional levels
Cayosoft Threat Definition CTD-000159
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Active Directory environments operating at Windows Server 2012 R2 or lower functional levels lack foundational security features, such as robust encryption, advanced authentication methods, and recovery mechanisms. These limitations increase exposure to modern attacks and make recovery from compromise significantly harder.
- Severity: High
- Platform: Active Directory
- Category: Forest-wide, Infrastructure
- MITRE ATT&CK Tactics: Persistence, Privilege Escalation, Defense Evasion
MITRE D3FEND Tactics: D3-OSM (Operating System Monitoring)
Description
Active Directory environments operating at Windows Server 2012 R2 or lower functional levels lack foundational security features, such as robust encryption, advanced authentication methods, and recovery mechanisms. These limitations expose the environment to critical vulnerabilities, including outdated cryptographic standards, unprotected credentials, and difficulty recovering from accidental deletions. Forests and domains at these levels are highly susceptible to exploitation by attackers who rely on deprecated protocols and privilege escalation techniques. Maintaining insufficient forest and domain functional levels therefore represents an ongoing structural weakness across the entire AD forest.

Real-World Scenario
An organization still operates its production forest at Windows Server 2008 R2 domain and forest functional levels to avoid application compatibility testing. A threat actor gains a foothold on an on-premises server and discovers that legacy protocols and weaker encryption are still enabled due to the low functional level. The attacker uses deprecated authentication methods and older Kerberos behaviors to harvest credentials, move laterally between domain-joined servers, and eventually gain domain admin privileges while avoiding some modern detection controls. Because the forest lacks newer recovery and security features, responding teams find it harder to contain and remediate the breach. Cayosoft Guardian with CTD-000159 identifies the domains running at insufficient functional levels and raises a threat alert, giving administrators a chance to remediate before the attacker can fully exploit these weaknesses.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
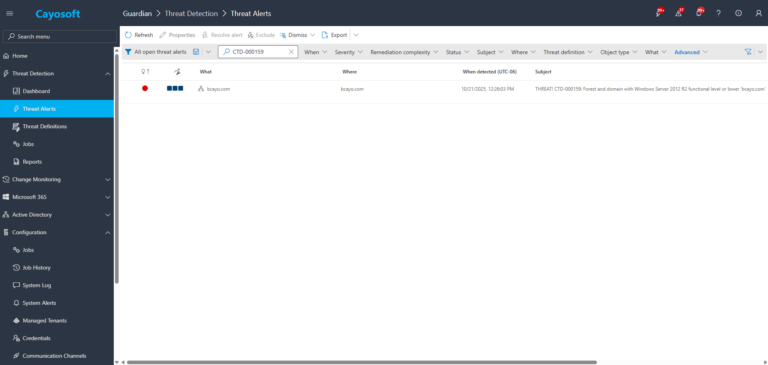
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Open All Alerts and search for CTD-000159 or “Insufficient forest and domain functional levels”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
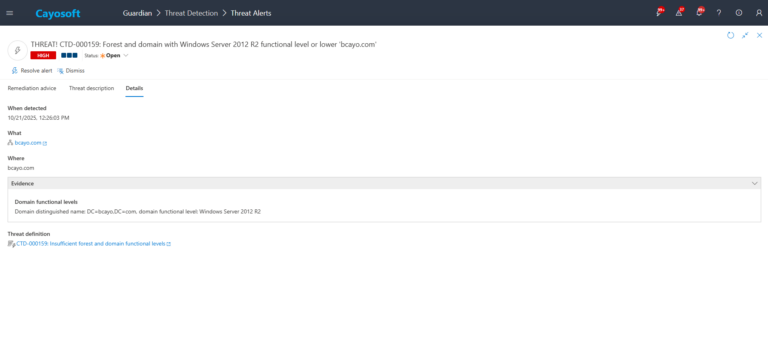
4.) Evidence:
- Domain functional levels
Remediation Steps
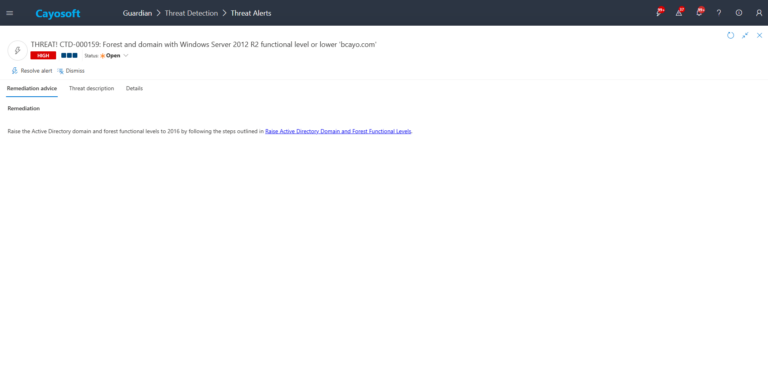
Raise the Active Directory domain and forest functional levels to 2016 by following the steps outlined in Raise Active Directory Domain and Forest Functional Levels.
How to Prevent It
- Establish a minimum supported forest and domain functional level in the organization’s security baseline (for example, Windows Server 2016 or later).
- Regularly review forest and domain functional levels and plan upgrades as Windows Server versions reach end of support.
- Remove or upgrade legacy systems and applications that block raising the functional level, or isolate those systems in tightly controlled segments.
- Use Cayosoft Guardian and CTD-000159 to continuously monitor forests and domains and ensure that no new domains are introduced at insufficient functional levels.
- Document a repeatable process for raising functional levels and include this process in standard AD lifecycle and modernization projects.
Cayosoft Guardian can proactively detect and alert on Insufficient forest and domain functional levels. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Low functional levels (2012 R2 or earlier) lack modern security enhancements, updated cryptographic protections, and improved authentication protocols. This makes the environment far more susceptible to credential theft, privilege escalation, and attacks leveraging legacy protocols.
CTD-000159 inspects the functional levels reported by each domain and forest in Active Directory. If any are operating below the organization’s minimum baseline (such as Windows Server 2016), the rule raises a threat alert with evidence indicating the specific levels detected.
Attackers may leverage outdated Kerberos behaviors, weak NTLM configurations, older encryption ciphers, and legacy authentication workflows to escalate privileges, evade modern detection controls, and maintain persistent access within the forest.
Yes. Native tools like PowerShell (Get-ADForest, Get-ADDomain) and legacy GUI utilities can display functional levels, and Cayosoft Guardian Protector provides free assessment capabilities that help highlight outdated domain and forest modes more efficiently.
Yes. Cayosoft Guardian delivers continuous monitoring, real-time alerts, and prescriptive remediation guidance for CTD-000159 and more than 200 other AD/Entra/M365 risk conditions. It automatically surfaces outdated functional levels and ensures environments meet modern security baselines.
References
- Microsoft Learn – Raise Active Directory Domain and Forest Functional Levels:
https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/raise-active-directory-domain-forest-functional-levels
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Insufficient forest and domain functional levels, you reduce attack surfaces and strengthen your organization’s overall security posture.