Inactive AD Domain Controller
Cayosoft Threat Definition CTD-000137
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A domain controller that has not authenticated for over 45 days may have outdated secrets and be unable to participate in replication or authentication, increasing the risk of security gaps and lingering stale credentials.
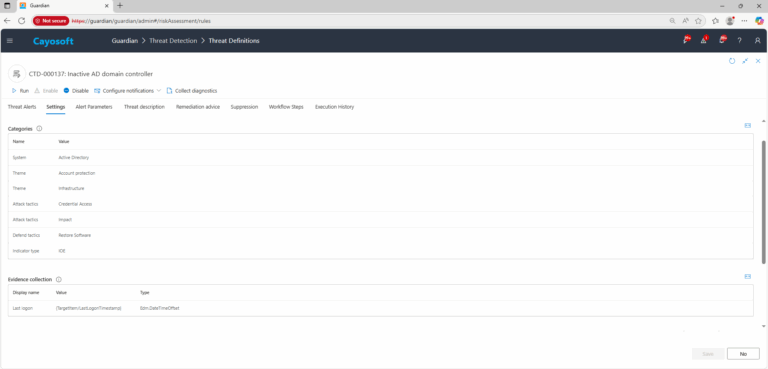
- Severity: Critical
- Platform: Active Directory
- Category: Account protection, Infrastructure
- MITRE ATT&CK Tactics: Credential Access, Impact
- MITRE D3FEND Tactics: Restore Software
Description
Some of your domain controllers haven’t been authenticating for over 45 days. This could indicate that their secrets haven’t been renewed, which normally occurs every 30 days by default. To address this, you should check the connectivity and replication status between your domain controllers. Running diagnostics, testing DNS, and examining Kerberos authentication can help identify the issue. If the problem persists, you may need to force a password change or reconfigure the affected domain controllers.
Note: If the ms-DS-Logon-Time-Sync-Interval Active Directory Schema attribute is greater than the Time Interval parameter defined in the threat rule, detection accuracy may be impacted, potentially causing false positives or false negatives.

Real-World Scenario
A remote site loses network connectivity to headquarters for two months, leaving its local domain controller unable to authenticate against other DCs. During that time, its computer account password becomes stale, replication halts, and its directory data becomes outdated. Attackers who compromise this isolated DC could exploit outdated credentials or replicate malicious changes once it reconnects. Cayosoft Guardian could have detected the inactivity early, allowing administrators to isolate or decommission the stale DC before it rejoined the domain.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000137 or Inactive AD domain controller.
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence fields:
- Last logon
Remediation Steps
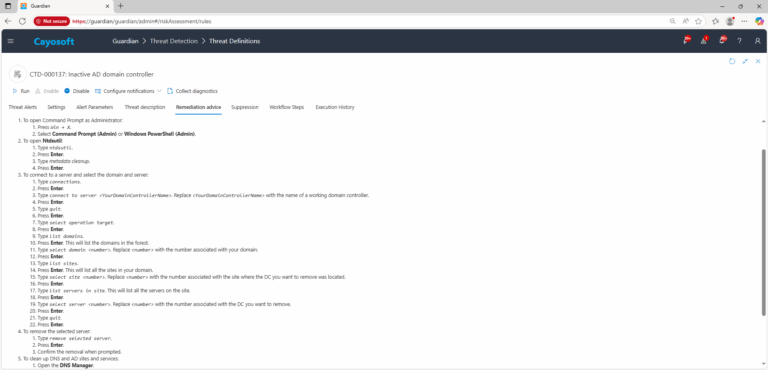
- ) To open Command Prompt as Administrator:
- Press
Win + X. - Select Command Prompt (Admin) or Windows PowerShell (Admin).
- Press
- ) To open Ntdsutil:
- Type
ntdsutil. - Press Enter.
- Type metadata cleanup.
- Press Enter.
- Type
- ) To connect to a server and select the domain and server:
- ) Type
connections. - ) Press Enter.
- ) Type
connect to server <YourDomainControllerName>. Replace<YourDomainControllerName>with the name of a working domain controller. - ) Press Enter.
- ) Type
quit. - ) Press Enter.
- ) Type
select operation target. - ) Press Enter.
- ) Type
list domains. - ) Press Enter. This will list the domains in the forest.
- ) Type
select domain <number>. Replace<number>with the number associated with your domain. - ) Press Enter.
- ) Type
list sites. - ) Press Enter. This will list all the sites in your domain.
- ) Type
select site <number>. Replace<number>with the number associated with the site where the DC you want to remove was located. - ) Press Enter.
- ) Type
list servers in site. This will list all the servers on the site. - ) Press Enter.
- ) Type
select server <number>. Replace<number>with the number associated with the DC you want to remove. - ) Press Enter.
- ) Type
quit. - ) Press Enter.
- ) Type
- ) To remove the selected server:
- ) Type
remove selected server. - ) Press Enter.
- ) Confirm the removal when prompted.
- ) Type
- ) To clean up DNS and AD sites and services:
- ) Open the DNS Manager.
- ) Delete any Host (A or AAAA) records and Name Server (NS) records associated with the removed DC.
- ) To clean up Active Directory Sites and Services:
- ) Open Active Directory Sites and Services.
- ) Expand the site that contained the removed DC.
- ) Right-click the DC.
- ) Select Delete.
- ) To verify that the DC has been removed, check Active Directory Users and Computers, DNS Manager and Active Directory Sites and Services
How to Prevent It
Cayosoft Guardian can proactively detect and alert on inactive domain controllers before they rejoin the network with stale data or compromised credentials. It continuously monitors AD, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning for remediation.
FAQ
An inactive domain controller that hasn’t authenticated for an extended period—typically over 45 days—may contain outdated secrets and stale directory data. If it reconnects, it can reintroduce invalid credentials, replicate corrupted or compromised data, and create authentication inconsistencies across the domain. This poses a critical risk because attackers could exploit the stale DC to gain unauthorized access or manipulate replication.
Common causes include network isolation, misconfigured replication links, DNS issues, or decommissioned sites that were never properly cleaned up. In some cases, temporary disconnections (such as maintenance or VPN downtime) extend beyond the password renewal period, leading to stale secrets. Regular monitoring and replication testing can help identify and resolve such issues before they become security concerns.
Administrators should verify the DC’s network connectivity, DNS resolution, and replication health. If the controller cannot reestablish secure communication, it should be cleanly removed using NTDSUTIL metadata cleanup and DNS record deletion to prevent replication of outdated data. After removal, review replication topology to confirm stability and ensure remaining domain controllers are healthy.
References
- Microsoft Docs – Remove Data in Active Directory After an Unsuccessful Domain Controller Demotion
Final Thought
Proactively identifying and removing inactive domain controllers helps maintain replication integrity and prevents stale or compromised systems from rejoining the environment, strengthening overall AD security posture.