Guest account with Microsoft Entra role membership
Cayosoft Threat Definition CTD-000032
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A guest user account with membership in a Microsoft Entra role poses a threat to your environment. If the external account is compromised, an attacker can use the delegated role to access resources in your tenant.
- Severity: High
- Platform: Entra ID
- Category: Account protection, Guest management
- MITRE ATT&CK Tactics: Privilege Escalation
- MITRE D3FEND Tactics: User Account Permissions, Credential Transmission Scoping
Description
A guest user account that holds Microsoft Entra directory role membership increases exposure because the identity is controlled by an external organization or identity provider. If that external account is taken over, a threat actor can leverage the role for privileged actions in your tenant without needing to breach a first-party account.

Real-World Scenario
An attacker compromises a contractor’s account in a partner tenant. Because the contractor is a member of User Administrator in your tenant, the attacker silently resets passwords for internal users, creates new app registrations, and grants consent to malicious permissions. To avoid obvious detection, the attacker schedules actions during maintenance windows and uses API calls with common user agents. Cayosoft Guardian detects the guest user’s role membership and raises an alert with the user principal name and assigned roles before the attacker escalates further.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
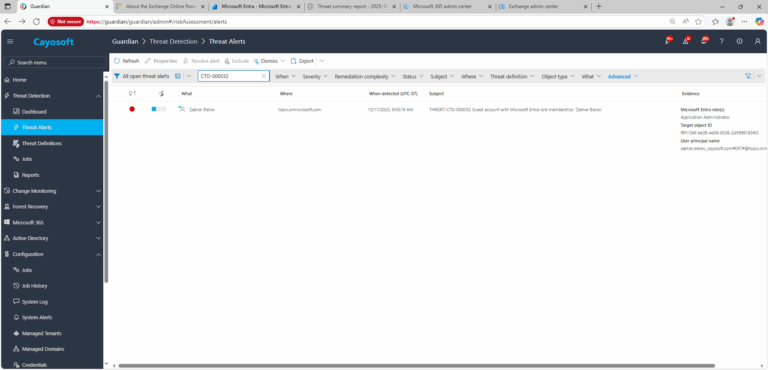
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Open All Alerts and search for CTD-000032 or Guest account with Microsoft Entra role membership.
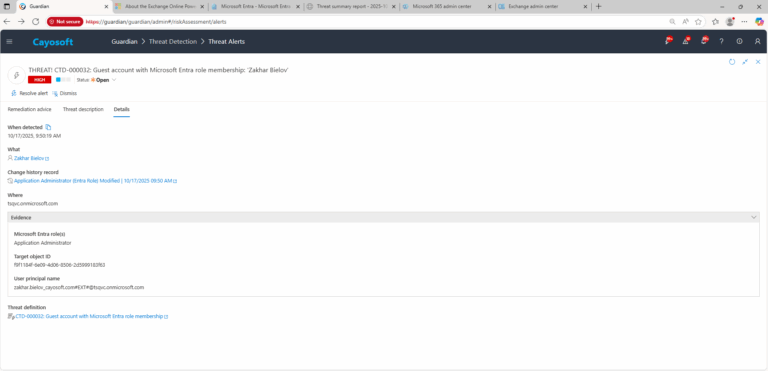
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Microsoft Entra role(s)
- Target object ID
- User principal name
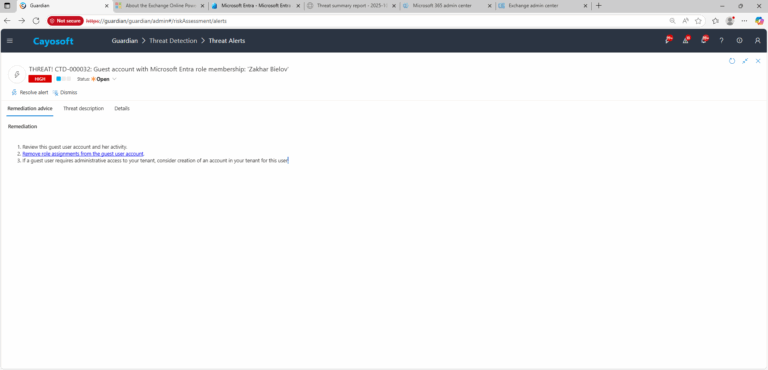
Remediation Steps
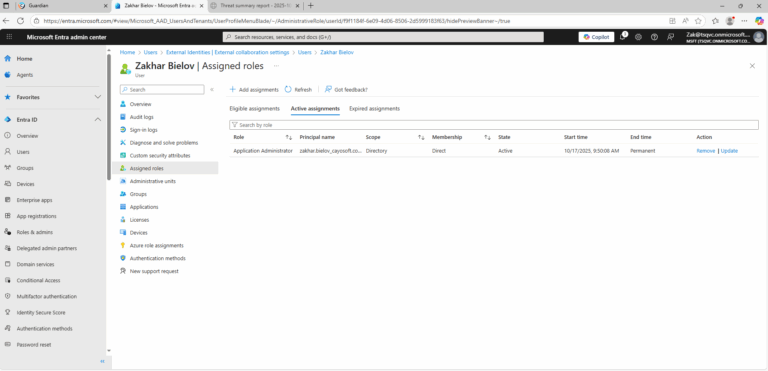
- ) Review this guest user account and her activity.
- ) Remove role assignments from the guest user account.
- ) If a guest user requires administrative access to your tenant, consider creation of an account in your tenant for this user.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Guest account with Microsoft Entra role membership. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
Additionally:
- Prefer first-party accounts for administrators; restrict guest users from holding privileged roles.
- Use Entra PIM for just-in-time elevation and approval workflows; require MFA for activation.
- Periodically review all guest role assignments; remove stale access and enforce least privilege.
- Scope credentials and consent: block broad admin consent and audit app permissions regularly.
FAQ
Guest users belong to external organizations or identity providers, which means their security posture is outside your control. If a guest account with a privileged Microsoft Entra role is compromised, the attacker can perform administrative actions—such as resetting passwords or creating app registrations—inside your tenant without breaching an internal account.
In the Cayosoft Guardian Threat Detection Dashboard, search for CTD-000032 or the issue name. The alert shows guest accounts that hold Entra role memberships, listing their assigned roles, object IDs, and user principal names to enable quick triage and removal of unauthorized privileges.
Review each guest user’s business justification for holding a role, then remove unnecessary assignments through the Microsoft Entra admin center or PowerShell. If administrative access is truly required, create a managed account in your tenant and apply Privileged Identity Management (PIM) for just-in-time, least-privilege elevation.
References
- Microsoft Learn — Remove role assignments: https://learn.microsoft.com/en-us/azure/role-based-access-control/role-assignments-remove
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Guest account with Microsoft Entra role membership, you reduce attack surfaces and strengthen your organization’s overall security posture.