Exchange Online mailbox with SMTP forwarding address
Cayosoft Threat Definition CTD-000031
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An Exchange Online mailbox configured with an SMTP forwarding address can enable covert data exfiltration and long-term access. Attackers commonly add external forwarding to siphon sensitive email without triggering obvious sign-in alerts.
- Severity: Informational
- Platform: Exchange Online
- Category: Mailbox protection
- MITRE ATT&CK Tactics: Defense Evasion, Persistence
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Exchange Online mailbox with SMTP forwarding address might be an indication of threat activities. A threat actor might use an SMTP forwarding address to receive emails from the compromised mailbox.

Real-World Scenario
After compromising a user via phishing, an attacker adds an external SMTP forwarding address to the mailbox and hides their tracks by clearing audit logs in the client. Business-sensitive emails (e.g., invoices, MFA prompts, password resets) silently forward to an attacker-controlled inbox. The attacker maintains persistence even if the victim changes their password because forwarding happens server-side. Cayosoft Guardian detects the presence of an SMTP forwarding address and raises an alert with the destination address so operations can remove it and contain data leakage.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
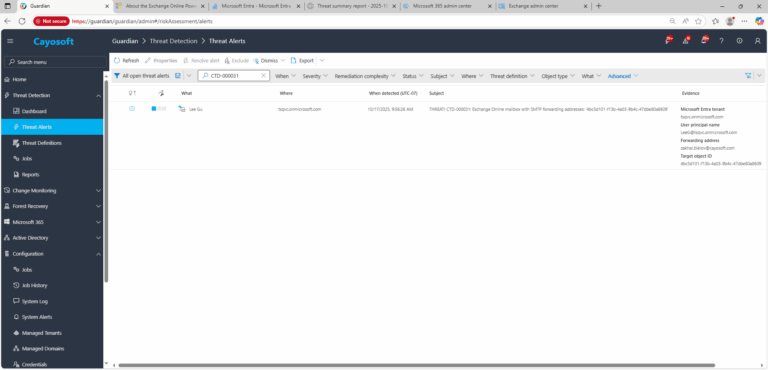
2.) Open All Alerts and search for CTD-000031 or Exchange Online mailbox with SMTP forwarding address.
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Microsoft Entra tenant
- User principal name
- Forwarding address
- Target object ID
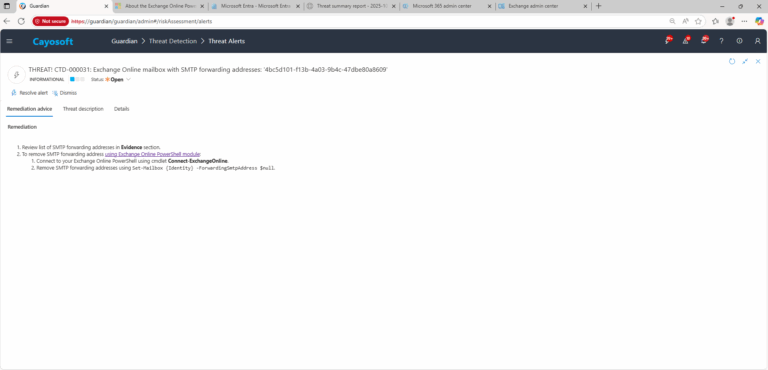
Remediation Steps
- ) Review list of SMTP forwarding addresses in Evidence section.
- ) To remove SMTP forwarding address using Exchange Online PowerShell module:
- ) Connect to your Exchange Online PowerShell using cmdlet Connect-ExchangeOnline.
- ) Remove SMTP forwarding addresses using
Set-Mailbox {Identity} -ForwardingSmtpAddress $null.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Exchange Online mailbox with SMTP forwarding address. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
Additionally:
- Enforce a policy that disables automatic external forwarding except for approved cases.
- Monitor and alert on new mailbox rules and forwarding settings, especially on high-risk mailboxes.
- Use least-privilege administration and require approvals for mailbox configuration changes.
FAQ
An SMTP forwarding address can be used by attackers to exfiltrate emails from a compromised mailbox silently. Forwarding occurs server-side, meaning sensitive messages—such as invoices, MFA prompts, or password resets—can be sent to an external mailbox without triggering sign-in alerts.
In the Cayosoft Guardian Threat Detection Dashboard, search for CTD-000031 or the issue name. Alerts provide the mailbox’s user principal name, the destination forwarding address, and the target object ID, allowing rapid verification and remediation.
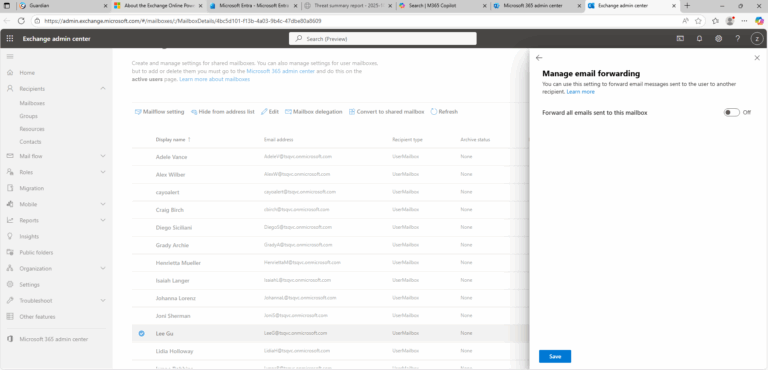
Validate whether the forwarding address is required for business purposes. If not, remove it via Set-Mailbox -ForwardingSmtpAddress $null in Exchange Online PowerShell. Additionally, check for suspicious inbox rules, reset credentials if compromise is suspected, and enforce tenant-wide policies that restrict external forwarding to approved cases only.
References
- Microsoft Docs — Exchange Online PowerShell (V2): https://learn.microsoft.com/powershell/exchange/exchange-online-powershell-v2?view=exchange-ps
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Exchange Online mailbox with SMTP forwarding address, you reduce attack surfaces and strengthen your organization’s overall security posture.