DNS Zone Allowing Unsecure Update
Cayosoft Threat Definition CTD-000091
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An unsecure dynamic update in a DNS zone allows any device — authenticated or not — to modify DNS records.
This can enable attackers to redirect network traffic, impersonate legitimate services, and harvest credentials.
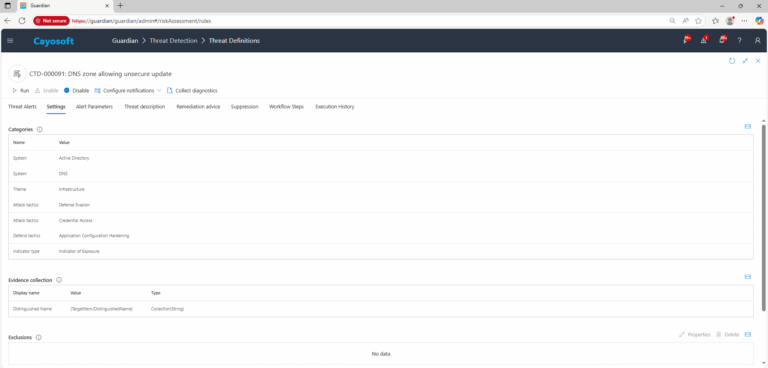
- Severity: Critical
- Platform: Active Directory
- Category: DNS, Infrastructure
- MITRE ATT&CK Tactics: Defense Evasion, Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Microsoft DNS supports dynamic updates, enabling devices to register and update their DNS records automatically.
However, if the zone is configured for Unsecure and Secure updates, no authentication is required for a DNS update request.
This opens several risks:
- Record Hijacking: Attackers replace an existing host record (e.g., a domain controller or web server) with their own IP address.
- Credential Theft: Redirecting authentication traffic to a rogue server for password capture.
- Service Disruption: Overwriting service records to break legitimate application connectivity.
Cayosoft Guardian detects and flags DNS zones where unsecure dynamic updates are allowed.

Real-World Scenario
A DNS zone for corp.local is configured for unsecure dynamic updates.
An attacker connected to the internal network issues a DNS update request, replacing the IP of dc01.corp.local with their own machine’s IP.
When users attempt to log in, authentication requests are sent to the attacker, who captures NTLM hashes.
Cayosoft Guardian would have detected the unsecure update setting and alerted before exploitation.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Search for CTD-000091 or DNS zone allowing unsecure update.
3.) Open any alert and Click for details (from Raise Threat Alert action).
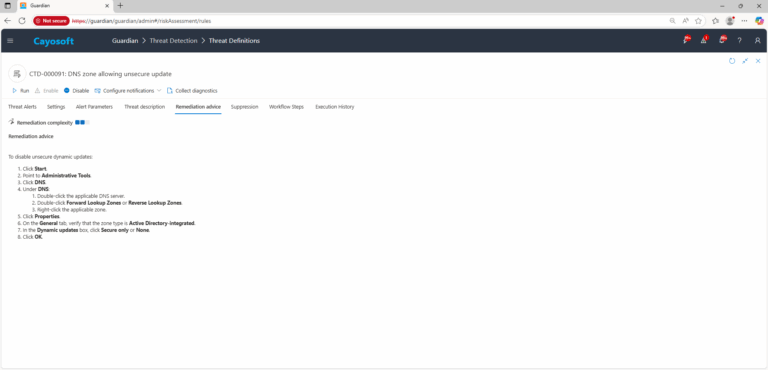
Remediation Steps
To disable unsecure dynamic updates:
- ) Click Start.
- ) Point to Administrative Tools.
- ) Click DNS.
- ) Under DNS:
- ) Double-click the applicable DNS server.
- ) Double-click Forward Lookup Zones or Reverse Lookup Zones.
- ) Right-click the applicable zone.
- ) Click Properties.
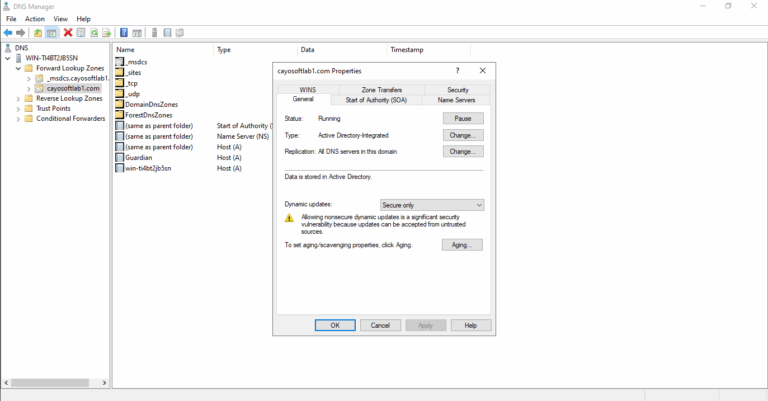
- ) On the General tab, verify that the zone type is Active Directory-integrated.
- ) In the Dynamic updates box, click Secure only or None.
- ) Click OK.
How to Prevent It
- Use Secure Only Updates: Require Active Directory authentication for all dynamic DNS changes.
- Restrict Permissions: Limit update rights to specific service accounts and trusted devices.
- Regular Auditing: Periodically check DNS zone properties to verify secure update settings.
FAQ
It’s when a DNS zone accepts record updates from any source, without authentication. This allows any device trusted or untrusted to modify DNS records.
Attackers can hijack critical records (like domain controllers or web servers), redirect authentication traffic, capture credentials, or disrupt business services.
Secure updates require Active Directory authentication and enforce ACL-based permissions. Unsecure updates accept changes from any device on the network, even those not trusted.
References
- Microsoft – Secure Dynamic Update
- CISA – Mitigating DNS Infrastructure Attacks
Final Thought
An unsecure DNS update setting is like leaving your company’s map editable by strangers — and attackers will gladly redraw it to lead your users straight into their traps.