Dangerous ACLs Expose DPAPI Key Objects
Cayosoft Threat Definition CTD-000144
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Dangerous Access Control Lists (ACLs) on Data Protection API (DPAPI) backup key objects can allow attackers to retrieve encryption keys used to protect sensitive data across the Windows domain. With these keys, an attacker could decrypt passwords, private keys, and other protected secrets, leading to widespread compromise.
- Severity: Critical
- Platform: Active Directory
- Category: Privileged Access Management
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Credential Hardening
Description
DPAPI keys are crucial for encrypting and decrypting sensitive data in Windows environments, including stored credentials, certificates, and browser secrets. If an attacker gains elevated permissions to the BCKUPKEY container in Active Directory, they can export DPAPI domain backup keys. This enables decryption of all DPAPI-protected data for any user or service in the domain, bypassing authentication safeguards.

Real-World Scenario
An attacker compromises a low-privilege domain account and discovers overly permissive ACLs on the BCKUPKEY container. They use these rights to extract the DPAPI domain backup keys and then decrypt stored browser passwords, cached RDP credentials, and private encryption keys from multiple administrative systems. This provides unfettered access to sensitive resources without triggering standard login events. Cayosoft Guardian detects and alerts on the dangerous ACL change before the keys are accessed, preventing domain-wide data exposure.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
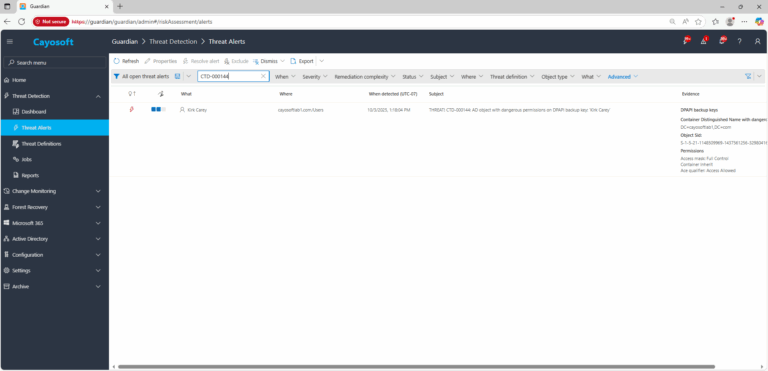
2.) View All Alerts and search for CTD-000144 or Dangerous ACLs expose DPAPI key objects.
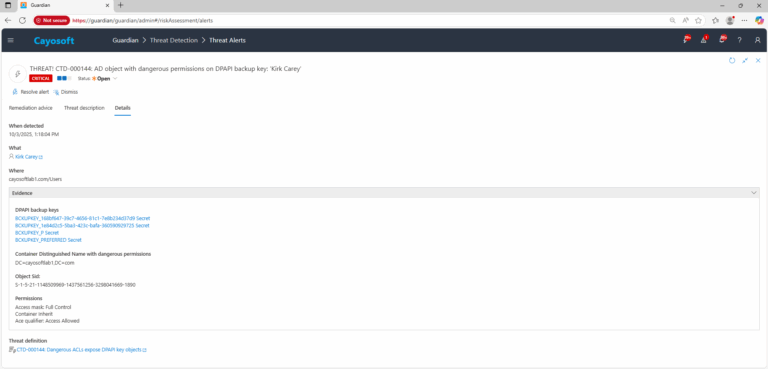
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- DPAPI backup keys
- Container Distinguished Name with dangerous permissions
- Object SID
- Permissions
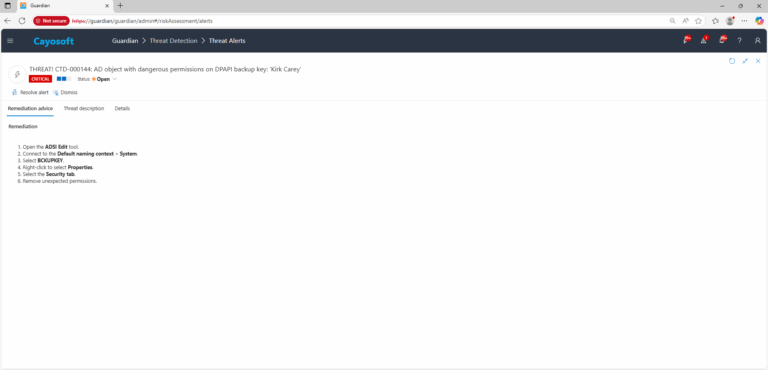
Remediation Steps
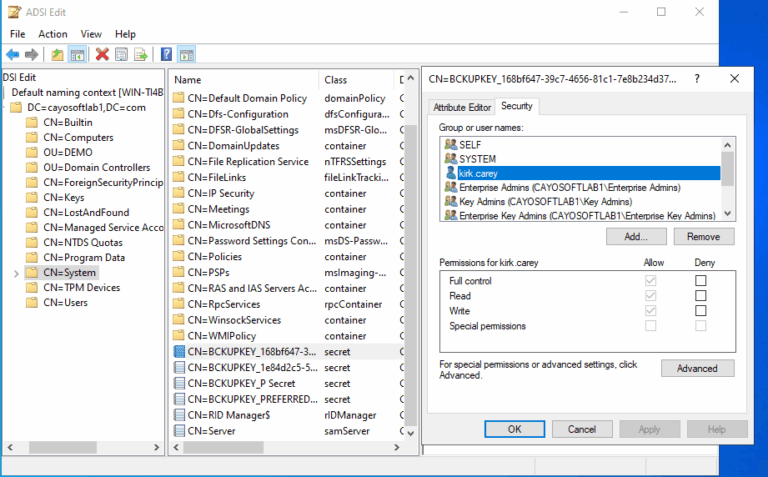
- ) Open the ADSI Edit tool.
- ) Connect to the Default naming context > System.
- ) Select BCKUPKEY.
- ) Right-click to select Properties.
- ) Select the Security tab.
- ) Remove unexpected permissions.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Dangerous ACLs expose DPAPI key objects. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Its main goal is to highlight how insecure ACL configurations on DPAPI backup key objects can lead to credential theft and to provide steps for detection and remediation.
Active Directory and security administrators are responsible for reviewing permissions on the BCKUPKEY container and ensuring that only authorized accounts have access.
It provides practical guidance on identifying dangerous ACLs, removing unauthorized permissions, and using continuous monitoring to stop attackers before sensitive data is compromised.
References
Final Thought
Proactive monitoring and timely remediation of dangerous ACLs on sensitive containers like BCKUPKEY is critical. By securing DPAPI key objects, you prevent attackers from decrypting sensitive data and protect the integrity of your entire Active Directory environment.