Dangerous ACLs Expose Certificate Templates Container
Cayosoft Threat Definition CTD-000143
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Non-default principals with elevated permissions on the Certificate Templates container can escalate privileges by creating or modifying certificate templates to issue high-privilege authentication certificates, enabling full domain compromise.
- Severity: Critical
- Platform: Active Directory
- Category: Privileged Access Management
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Credential Hardening
Description
The Certificate Templates container defines templates for issuing certificates across the domain. Misconfigured Access Control Lists (ACLs) allowing non-default principals elevated permissions can be exploited to create or alter templates that issue certificates for domain admins or other privileged accounts. These rogue certificates bypass normal authentication controls and can be used to impersonate high-value targets or gain long-term persistence.

Real-World Scenario
An attacker compromises an account with misconfigured permissions on the Certificate Templates container. They add a new template that allows issuance of smart card logon certificates mapped to domain admin accounts. By requesting such a certificate, the attacker authenticates directly as a privileged user, bypassing password policies and MFA. This remains hidden from most security monitoring, enabling the attacker to maintain persistent domain control. Cayosoft Guardian detects the dangerous ACL change before any malicious certificate templates can be created or abused.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
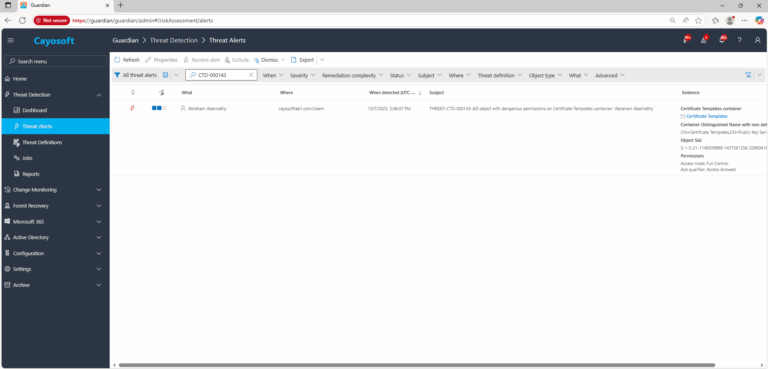
2.) View All Alerts and search for CTD-000143 or Dangerous ACLs expose Certificate Templates container.
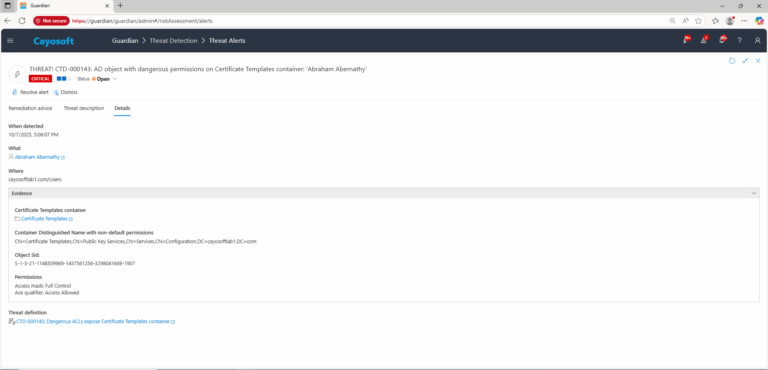
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review Evidence:
- Certificate Templates container
- Container Distinguished Name with non-default permissions
- Object SID
- Permissions
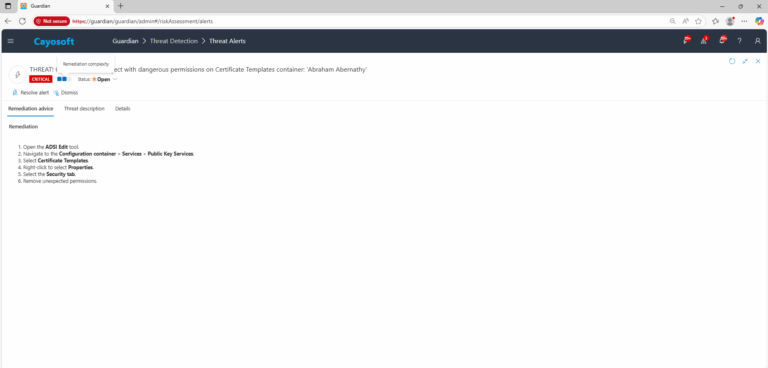
Remediation Steps
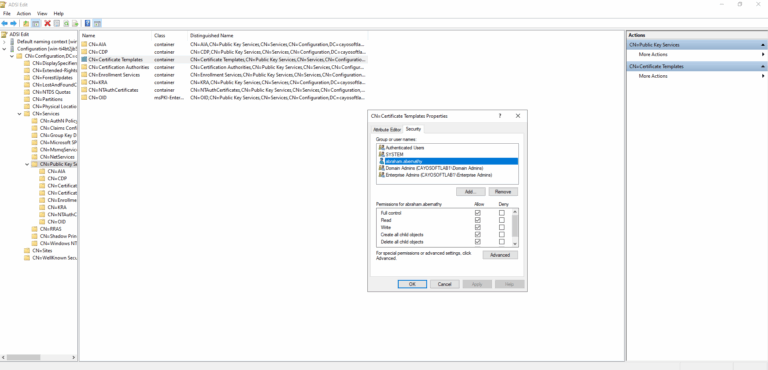
- ) Open the ADSI Edit tool.
- ) Navigate to the Configuration container > Services > Public Key Services.
- ) Select Certificate Templates.
- ) Right-click to select Properties.
- ) Select the Security tab.
- ) Remove unexpected permissions.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Dangerous ACLs expose Certificate Templates container. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Because the Certificate Templates container controls how authentication certificates are issued, non-default permissions allow unauthorized users to create or modify templates that can generate certificates for privileged accounts, effectively granting domain admin-level access without needing credentials.
Attackers can create or alter certificate templates that issue smart card logon or authentication certificates mapped to privileged accounts. Once they request a certificate using the compromised template, they can authenticate as a high-privilege user and move laterally within the domain while remaining undetected.
Regularly audit ACLs on the Certificate Templates container using tools like ADSI Edit or PowerShell’s Get-Acl, ensure only default system principals (e.g., Enterprise Admins) retain modify rights, and continuously monitor changes with solutions like Cayosoft Guardian to detect unauthorized access before exploitation occurs.
Yes. Cayosoft Guardian Protector provides free detection for misconfigured or overly permissive ACLs that expose the Certificate Templates container to exploitation.
Yes. Cayosoft Guardian delivers continuous monitoring, alerting, auditing, and prescriptive remediation for ADCS risks and more than 200 misconfigurations across Active Directory, Entra ID, Microsoft 365, and Intune.
References
- Microsoft – Certificate Templates Overview
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing dangerous ACLs on certificate management containers, you significantly reduce opportunities for credential theft and privilege escalation.