Constrained Delegation with Protocol Transition to the krbtgt Account
Cayosoft Threat Definition CTD-000139
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A krbtgt account configured for constrained delegation with protocol transition can be abused to impersonate any user and access sensitive services. If compromised, this configuration allows attackers to escalate privileges and move laterally without triggering standard authentication controls.
- Severity: Critical
- Platform: Active Directory
- Category: Account protection, Kerberos
- MITRE ATT&CK Tactics: Defense Evasion, Lateral Movement, Privilege Escalation
- MITRE D3FEND Tactics: Credential Hardening
Description
A threat actor can gain control of the trusted krbtgt account configured for constrained delegation with protocol transition. This setting enables the account to impersonate users and access specified services without requiring the user’s original credentials. In the wrong hands, this provides a powerful mechanism for escalating privileges across the environment, bypassing authentication barriers, and performing stealthy lateral movement.

Real-World Scenario
An attacker compromises a service account with constrained delegation and protocol transition rights to the krbtgt account. Using these permissions, they forge service tickets that impersonate privileged users, granting access to administrative shares and directory services. Because Kerberos trusts the krbtgt account, these tickets appear legitimate, allowing the attacker to move laterally and escalate privileges without raising typical security alerts. Cayosoft Guardian could have detected the risky delegation configuration early, enabling administrators to remove it before it was exploited.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
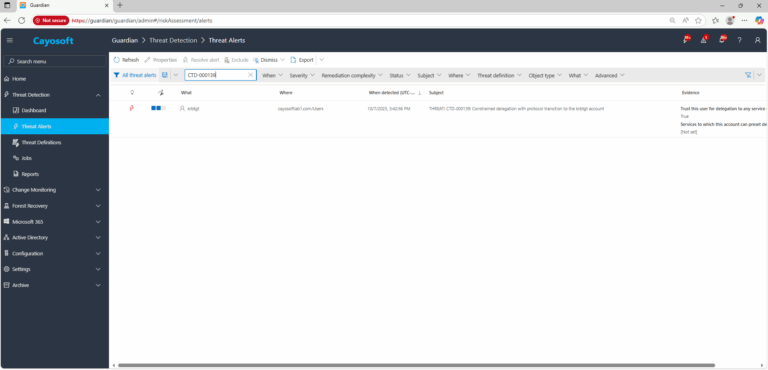
2.) View All Alerts and search for CTD-000139 or Constrained delegation with protocol transition to the krbtgt account.
3.) Open any alert and Click for details (from Raise Threat Alert action).
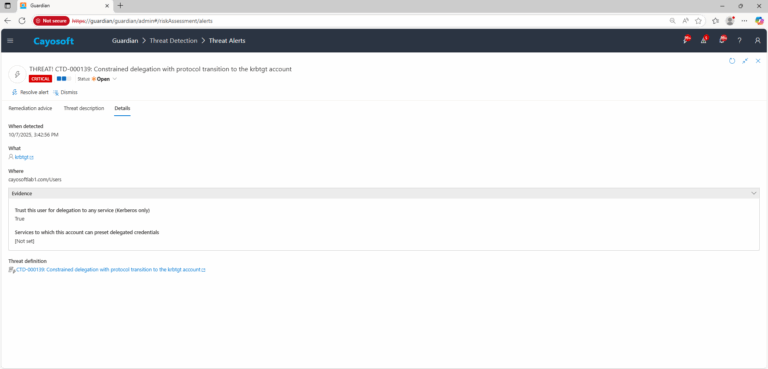
4.) Review Evidence fields:
- Trust this user for delegation to any service (Kerberos only)
- Services to which this account can preset delegated credentials
Remediation Steps
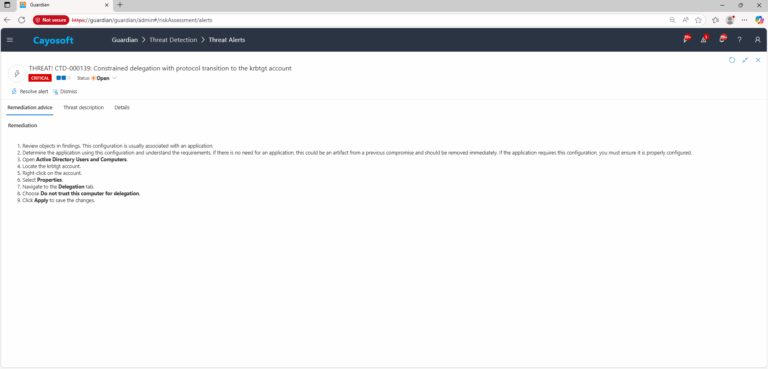
- ) Review objects in findings. This configuration is usually associated with an application.
- ) Determine the application using this configuration and understand the requirements. If there is no need for an application, this could be an artifact from a previous compromise and should be removed immediately. If the application requires this configuration, you must ensure it is properly configured.
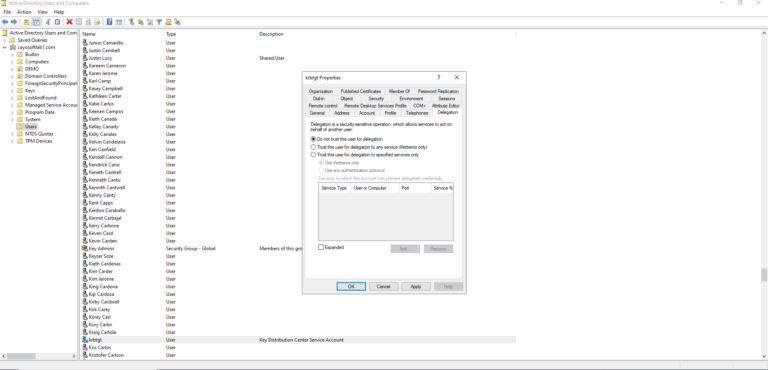
- ) Open Active Directory Users and Computers.
- ) Locate the krbtgt account.
- ) Right-click on the account.
- ) Select Properties.
- ) Navigate to the Delegation tab.
- ) Choose Do not trust this computer for delegation.
- ) Click Apply to save the changes.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on high-risk delegation configurations like protocol transition to the krbtgt account. It continuously monitors Active Directory for over 200 misconfigurations, helping to eliminate privilege escalation vectors before attackers can exploit them.
FAQ
The krbtgt account is the core of Kerberos authentication in Active Directory—it signs all ticket-granting tickets (TGTs). Allowing delegation or protocol transition to this account effectively gives any trusted service the power to impersonate any user, including Domain Admins. This configuration can let an attacker forge valid Kerberos tickets (Golden Ticket attacks), granting full domain control without detection.
Once an attacker compromises an account with constrained delegation and protocol transition rights to krbtgt, they can request service tickets on behalf of any user—even without knowing their credentials. These tickets appear legitimate because they are signed by the trusted krbtgt account, allowing the attacker to move laterally, access sensitive systems, and escalate privileges across the domain without raising security alerts.
Organizations should disable any delegation configuration involving the krbtgt account by setting it to “Do not trust this user for delegation” in Active Directory Users and Computers. Regular delegation audits should be performed using tools like Cayosoft Guardian to detect high-risk configurations. Additionally, enforcing the principle of least privilege and monitoring Kerberos ticket issuance logs helps identify and stop unauthorized delegation activity early.
References
- Microsoft Docs – Kerberos Constrained Delegation Overview
Final Thought
Eliminating insecure delegation to the krbtgt account is critical to preventing stealthy privilege escalation in Active Directory. Regular delegation audits with tools like Cayosoft Guardian can shut down these attack vectors before they become a breach.