AD no fine-grained password policy found or weak settings detected
Cayosoft Threat Definition CTD-000157
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
The absence of a fine-grained password policy or the misconfiguration of one or more settings has been identified. Privileged and service accounts without stronger controls increase the likelihood of credential theft and domain compromise.
- Severity: High
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Privilege Escalation, Credential Access
- MITRE D3FEND Tactics: Strong Password Policy
Description
Fine-grained password policies (FGPP) allow stricter requirements for privileged administrative and service accounts than the domain baseline. Weak or missing FGPP enables shorter, guessable, or re-used passwords and permissive lockout thresholds. An attacker who captures any Tier-0 account can escalate rapidly across AD and cloud-connected systems.
Because the Print Spooler runs under the SYSTEM account, these actions can expose the Domain Controller’s computer account credentials. Attackers can exploit this to perform lateral movement or escalate privileges within the domain. Microsoft recommends disabling the service on Domain Controllers to remove this attack surface.

Real-World Scenario
A domain relies only on the Default Domain Policy with an 8-character minimum and 90-day expiration. A contractor’s service account used on multiple servers has a reused password. After a phishing campaign, the attacker signs in and performs DCSync within hours. Strong FGPP for privileged groups (24+ length, history 24, complexity on, reversible encryption off, tight lockout) would have reduced the probability of compromise. Cayosoft Guardian would have detected CTD-000157 and highlighted the weak or missing settings before the attack.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
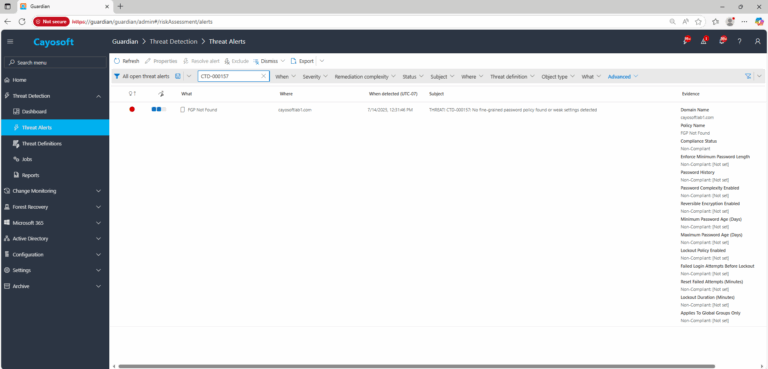
2.) View All Alerts and search for CTD-000157 or “AD no fine-grained password policy found or weak settings detected.”
3.) Open any alert and Click for details (from Raise Threat Alert action).
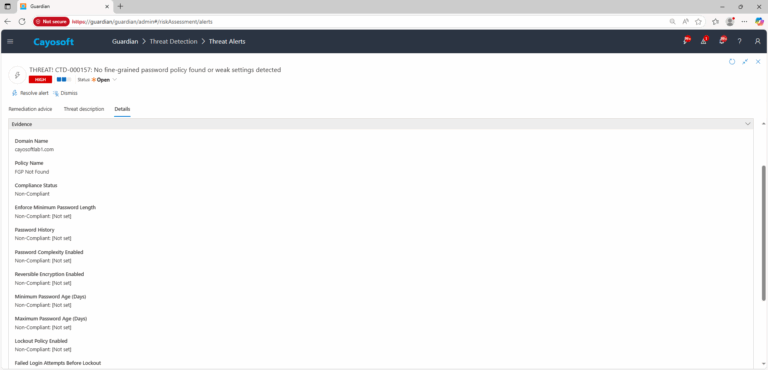
4.) Evidence (fields)
- Domain Name
- Policy Name
- Compliance Status
- Enforce Minimum Password Length
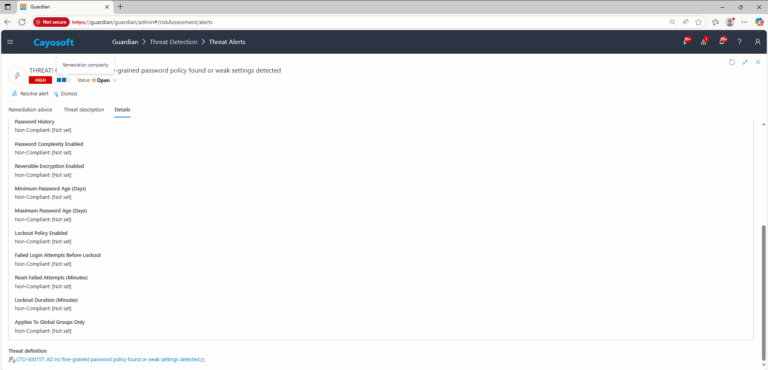
- Password History
- Password Complexity Enabled
- Reversible Encryption Enabled
- Minimum Password Age (Days)
- Maximum Password Age (Days)
- Lockout Policy Enabled
- Failed Login Attempts Before Lockout
- Reset Failed Attempts (Minutes)
- Lockout Duration (Minutes)
- Applies To Global Groups Only
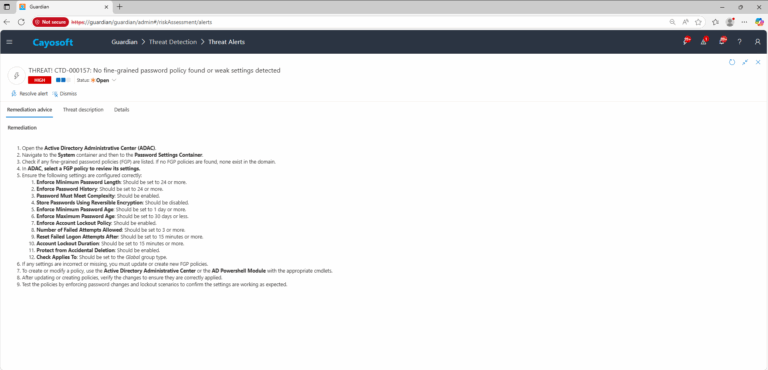
Remediation Steps
- ) Open the Active Directory Administrative Center (ADAC).
- ) Navigate to the System container and then to the Password Settings Container.
- ) Check if any fine-grained password policies (FGP) are listed. If no FGP policies are found, none exist in the domain.
- ) In ADAC, select a FGP policy to review its settings.
- ) Ensure the following settings are configured correctly:
- ) Enforce Minimum Password Length: Should be set to 24 or more.
- ) Enforce Password History: Should be set to 24 or more.
- ) Password Must Meet Complexity: Should be enabled.
- ) Store Passwords Using Reversible Encryption: Should be disabled.
- ) Enforce Minimum Password Age: Should be set to 1 day or more.
- ) Enforce Maximum Password Age: Should be set to 30 days or less.
- ) Enforce Account Lockout Policy: Should be enabled.
- ) Number of Failed Attempts Allowed: Should be set to 3 or more.
- ) Reset Failed Logon Attempts After: Should be set to 15 minutes or more.
- ) Account Lockout Duration: Should be set to 15 minutes or more.
- ) Protect from Accidental Deletion: Should be enabled.
- ) Check Applies To: Should be set to the Global group type.
- ) If any settings are incorrect or missing, you must update or create new FGP policies.
- ) To create or modify a policy, use the Active Directory Administrative Center or the AD Powershell Module with the appropriate cmdlets.
- ) After updating or creating policies, verify the changes to ensure they are correctly applied.
- ) Test the policies by enforcing password changes and lockout scenarios to confirm the settings are working as expected.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD no fine-grained password policy found or weak settings detected. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Without FGPP, these accounts fall back to the domain baseline policy. This often results in short, guessable, or reused passwords, dramatically increasing the likelihood of brute-force, phishing, or password reuse attacks.
Frequent mistakes include applying FGPP to OUs instead of global groups, using weak parameters (e.g., length < 12 characters), not enforcing password history, and enabling reversible encryption.
Review the settings against best practices (minimum length ≥ 24, history ≥ 24, complexity enabled, reversible encryption disabled, strict lockout). Then test password creation and reset workflows for privileged groups to ensure the policy is enforced correctly without disrupting business operations.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD no fine-grained password policy found or weak settings detected, you reduce attack surfaces and strengthen your organization’s overall security posture.