AD forest with high numbers of privileged group accounts
Cayosoft Threat Definition CTD-000082
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An excessive number of privileged accounts in an Active Directory forest significantly increases the attack surface. The more accounts with elevated rights, the harder it becomes to monitor and control them, raising the likelihood of privilege abuse and undetected compromise.
- Severity: Critical
- Platform: Active Directory
- Category: Forest-wide, Privileged Access Management
- MITRE ATT&CK Tactics: Privilege Escalation
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
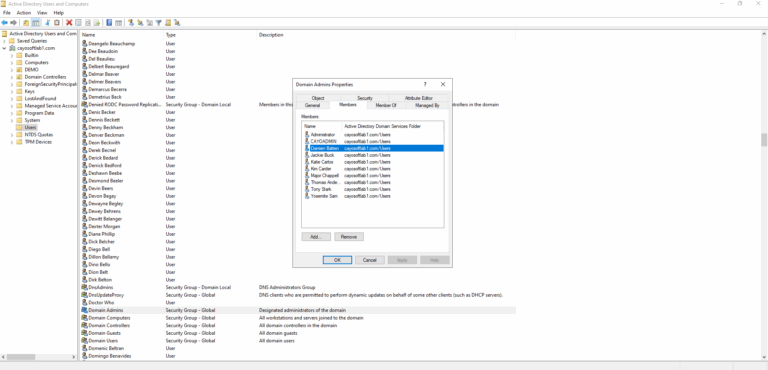
A large number of accounts in privileged groups makes it difficult to keep track of them, which can lead to poor accountability among privileged users. An environment with an excessive number of privileged users presents a bigger attack surface.
NOTE: Cayosoft Guardian considers both direct and indirect (nested) group permissions when evaluating risks. Privileged users are defined in Active Directory as users with adminCount=1. By design, Active Directory uses this attribute to protect members of administrative groups.
According to security best practices, it is not recommended to reuse admin accounts. Instead, these accounts must be de-provisioned. If an account has administrative permissions, it may also gain access to other resources using these permissions and retain this access even after being removed from the administrative groups. Learn more about AdminSDHolder and SDProp – Microsoft Community Hub.

Real-World Scenario
A global enterprise allows each regional IT team to maintain multiple privileged accounts for convenience. Over time, the forest accumulates hundreds of admin-enabled accounts, many of which are unused or belong to contractors who no longer work for the company. An attacker who compromises a single workstation discovers cached credentials for one of these dormant admin accounts and uses it to access domain controllers. From there, they escalate their privileges to gain complete forest control. Cayosoft Guardian could have detected the excessive privileged membership early, prompting a cleanup before the breach.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
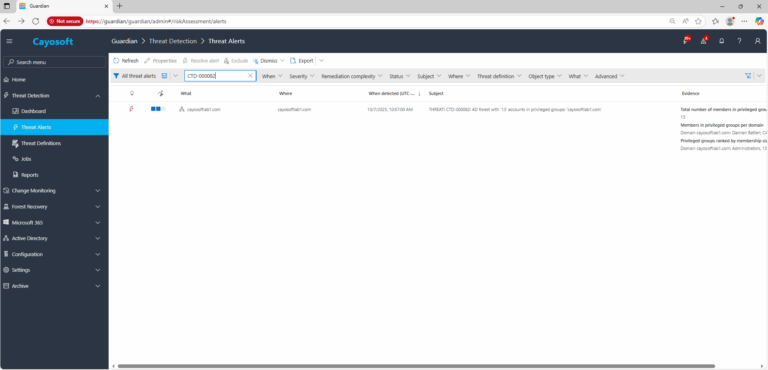
2.) View All Alerts and search for CTD-000082 or AD forest with high numbers of privileged group accounts.
3.) Open any alert and Click for details (from Raise Threat Alert action).
Evidence (example fields)
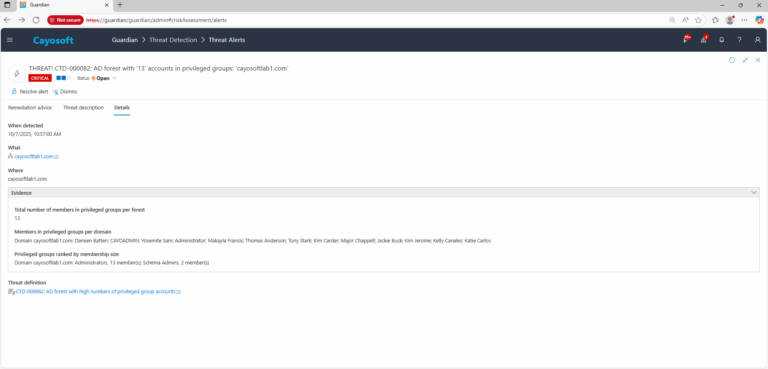
- Total number of members in privileged groups per forest
- Members in privileged groups per domain
- Privileged groups ranked by membership size
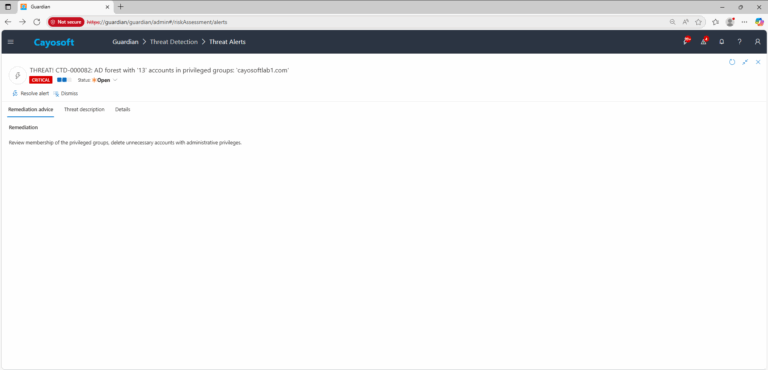
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD forest with high numbers of privileged group accounts. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Privileged accounts are members of protected administrative groups in AD. These accounts are automatically flagged with the attribute adminCount=1 to ensure their permissions remain protected.
Yes. Nested group membership can indirectly grant elevated rights. Tools like Cayosoft Guardian evaluate both direct and indirect memberships to reveal the true scope of privilege.
Dormant or duplicated accounts may still have cached credentials or lingering permissions. Attackers can exploit them to move laterally, escalate privileges, and compromise domain controllers.
Final Thought
Proactive monitoring and timely remediation of excessive privileged account membership is essential to maintaining a secure Active Directory environment. Reducing unnecessary elevated accounts lowers risk and improves administrative control.