AD domain with unsecure RBCD delegation on domain controllers
Cayosoft Threat Definition CTD-000089
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
- Severity: Critical
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
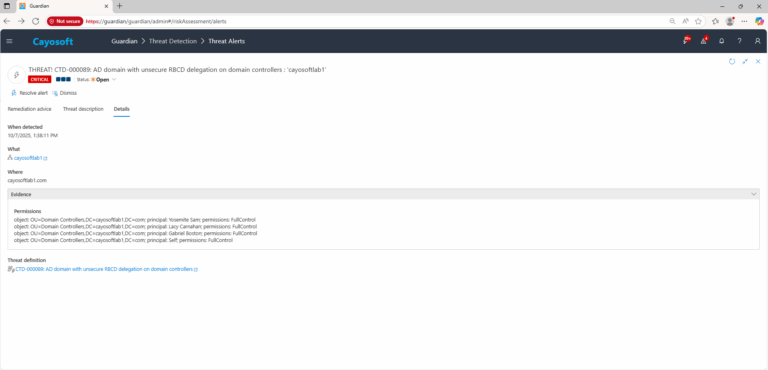
A threat actor could exploit this vulnerability by identifying non-privileged users outside of Domain Admins, Enterprise Admins, or Built-in Admins groups who have write access to RBCD settings on domain controllers.
With write access, attackers can configure a resource to impersonate any user (except those explicitly excluded in delegation settings).
This enables them to access services and systems under the guise of high-value accounts, bypassing normal authentication restrictions.

Real-World Scenario
In a large enterprise, a helpdesk technician account is mistakenly granted write permissions to RBCD settings on a domain controller.
An attacker compromises the technician’s account and uses these rights to configure a controlled machine to impersonate a domain admin. The attacker then remotely connects to critical servers, extracts password hashes, and moves laterally without triggering standard privileged account alerts.
Cayosoft Guardian could have detected the unsecure delegation settings early, preventing the escalation.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
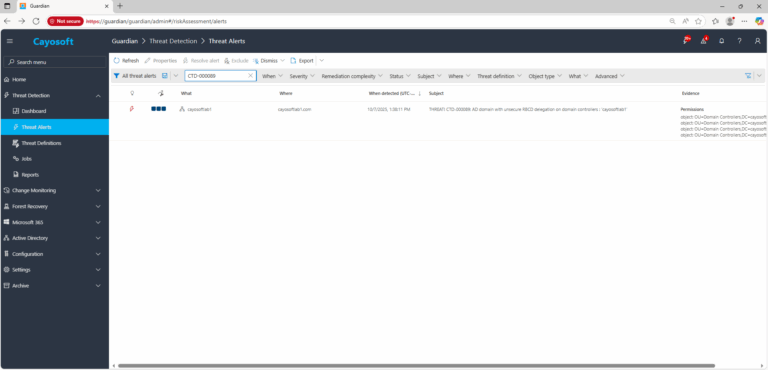
2.) Search for CTD-000089 or AD domain with unsecure RBCD delegation on domain controllers.
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review the evidence to see which accounts or groups have write permissions to RBCD settings on domain controllers.
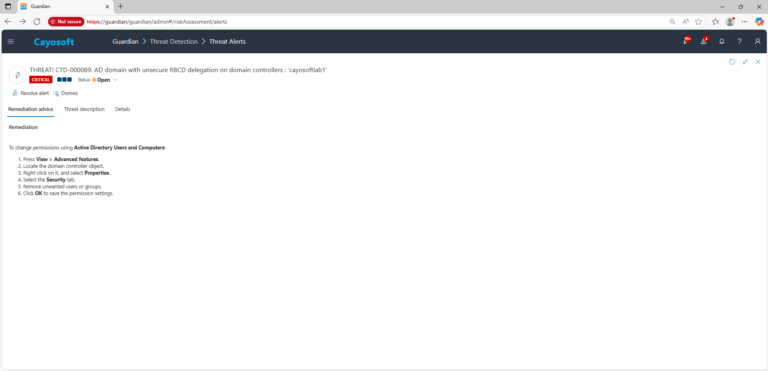
Remediation Steps
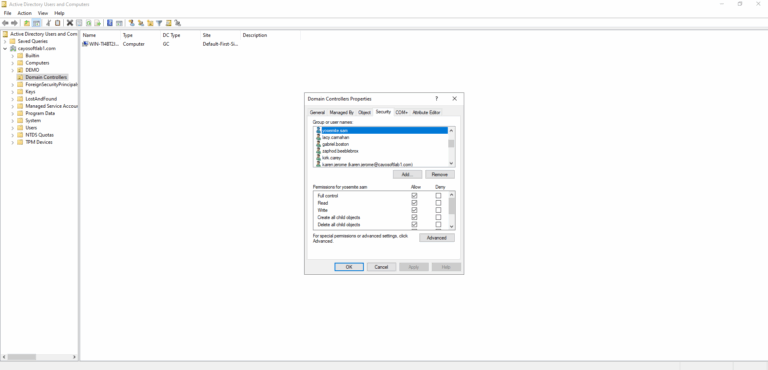
To change permissions using Active Directory Users and Computers:
- ) Press View > Advanced features.
- ) Locate the domain controller object.
- ) Right-click on it, and select Properties.
- ) Select the Security tab.
- ) Remove unwanted users or groups.
- ) Click OK to save the permission settings.
How to Prevent It
- Limit delegation rights strictly to trusted administrative accounts.
- Periodically audit RBCD permissions across all domain controllers.
- Use Cayosoft Guardian to continuously monitor delegation settings and receive real-time alerts for misconfigurations.
FAQ
RBCD is a Kerberos feature that allows a service or resource to act on behalf of a user when accessing another resource. It is designed for scenarios like front-end servers impersonating users to back-end services.
Domain controllers are the highest-value assets in Active Directory. If attackers gain the ability to set RBCD permissions on them, they can configure their own systems to impersonate privileged accounts, effectively bypassing authentication and MFA.
If a non-privileged account has write access to RBCD settings on domain controllers, attackers can abuse it to impersonate domain admins or service accounts, granting themselves unrestricted access to critical systems.
References
- Microsoft Documentation – RBCD
- ANSSI Advisory – vuln_delegation_a2d2
Final Thought
Unsecure RBCD on domain controllers is essentially a backdoor into impersonating admins. Closing this gap is critical to prevent stealthy privilege escalation attacks that bypass password and MFA protections.Bottom of Form